"Out of the box", Mozilla’s Firefox browser is widely regarded as the most privacy-friendly mainstream browser available.
However, there are still some Firefox security and privacy concerns to be had, even if you are using a VPN service!
In this guide, I'll show you how you can make Firefox more secure with just a few simple steps.
Firefox's privacy-friendly status comes down to the fact that Firefox is a fully audited open source software and that, unlike proprietary browsers such Google Chrome, Microsoft Edge, Internet Explorer, and Apple Safari, it does not track what you get up to on the internet.
Another reason for its popularity among privacy-heads is the large number of add-ons available that can greatly improve the privacy and security of your browsing. In addition to this, it is possible to access Firefox’s deep configuration settings in order to tweak its privacy and security parameters.
WebExtensions
In recent months Firefox has transitioned away from its old add-ons framework to WebExtensions. As of Firefox 57 "Quantum", it is only possible to use WebExtensions add-ons. Most of the add-ons listed below have been transitioned to WebExtensions, or are expected to in the near future.
Please see Are we WebExtensions yet? for the latest news about which add-ons have been updated to the new platform.
Check out our guide to Firefox VPN web extensions for a detailed look at the best ones to use.
Browser Fingerprinting
The way in which your browser is configured (especially the browser plugins used), together with details of your Operating System, allows you to be uniquely identified and tracked with a worryingly high degree of accuracy.
A particularly insidious (and ironic) aspect of this is that the more measures you take to avoid tracking (for example by using the plugins listed below), the more unique your browser fingerprint becomes.
The best defense against browser fingerprinting is to use as common and plain vanilla an OS and browser as possible. The hardened Tor browser with Tor disabled is the usual recommendation here. However, we do cover some alternative secure web browsers in our secure browsers guide.
Unfortunately, this leaves you open to other forms of attack. It also reduces the day-to-day functionality of your computer to such an extent that most of us will find the idea impractical.
For more information see my browsers and fingerprinting guide.
Things to Do When you First Install Firefox
Disable telemetry
By default, Firefox collects some telemetry information about you. This is mainly harmless, and is primarily to improve performance. Given that data collected in this way has privacy implications, however, it is a shame that Mozilla has decided to make it opt-out, rather than opt-in.
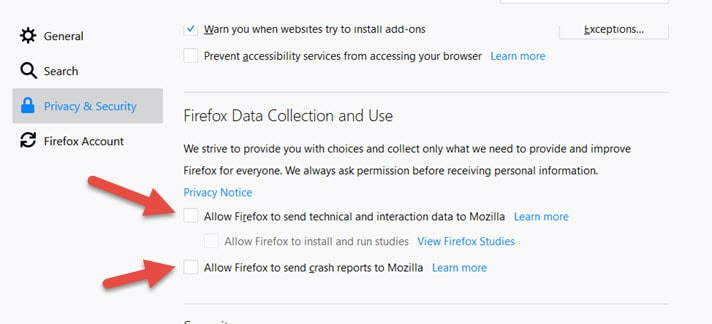
To disable telemetry in Firefox Desktop, go to:
- Open Menu (the three bars to the top right of the browser)
- Options
- Privacy & Security
- Firefox Data Collection and Use
- Uncheck both boxes.
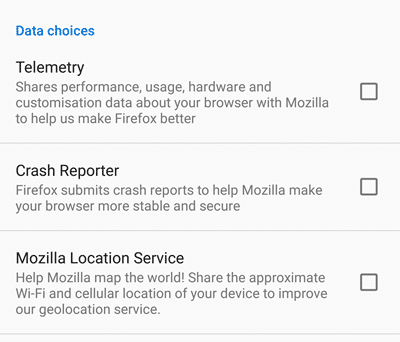
To disable telemetry in Firefox for Android, go to:
- Menu
- Settings
- Privacy
- Data Choices
- uncheck all three boxes
Telemetry can also be disabled using about.config, as discussed below.
Change the default search engine
Firefox Quantum switched from using Bing to Google as its default search engine. There are no doubt sound financial reasons for this move, but neither of these are good choices for privacy.
Check out our private search engines guide to find a search engine that values your privacy.
Fortunately, it is very easy to change the default search engine. Just go to:
- Menu
- Options
- Privacy & Security
- Default Search Engine
- Pick an engine from the drop-down dialog box. A quick guide to adding StartPage is also available here.
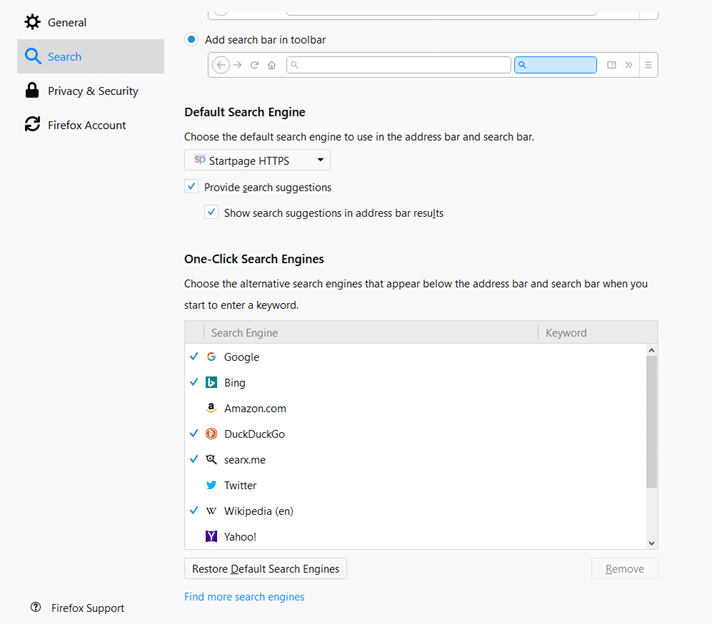
From here you can also change the "One-click" search engine options and add new search engines.
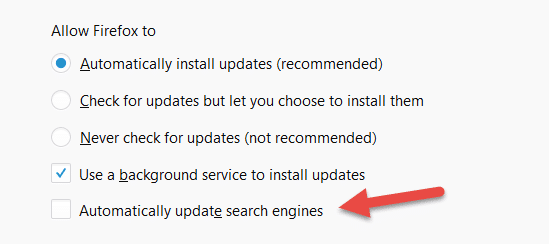
Please Note: From Firefox 57+, each browser update will switch the default search engine back to Google. To prevent this, go to Menu > Options > General > Allow Firefox to > uncheck Automatically update search engines.
So which search engine should you change to? Please check out our Privacy Search Engines Group Review for a rundown of the best options available.
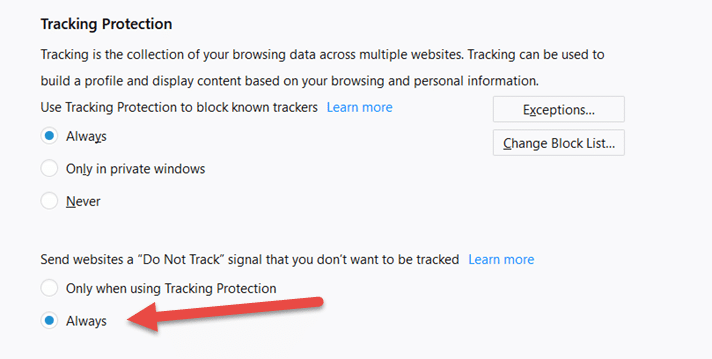
Enable Tracking Protection Globally
Tracking protection has been available for Firefox since 2015, but the option to enable it was hidden away in about:config (see below). Firefox 57+ brings tracking protection to the main interface, but by default it is only enabled in Private Browsing mode.
To enable tracking protection for all browsing, go to:
- Open
- Options
- Privacy & Security
- Tracking Protection
- Click the Always button
![]()
In Firefox for Android go to:
- Menu
- Settings
- Privacy
- Tracking Protection
- Enabled
Please Note: In addition to its privacy benefits, "Tracking Protection also enjoys performance benefits of a 44% median reduction in page load time and 39% reduction in data usage in the Alexa top 200 news sites".
Turn on Do Not Track
As with most browsers, Firefox offers a "Do not Track" (DNT) option. If enabled, Firefox will request websites you visit not to track you. Please note that compliance from websites is entirely voluntary, and it is sad fact that DNT requests are routinely ignored.
There is, however, zero harm in enabling this option, and it may work sometimes. Go to:
- Open Menu
- Options
- Privacy & Security
- Tracking Protection
- Set the "Do Not Track" radio button to Always.
In Firefox for Android go to:
- Menu
- Settings
- Privacy
- Do not track.
Disable WebRTC
Web Real-Time Communication (WebRTC) is a potentially useful standard that allows browsers to incorporate features such as voice calling, video chat, and P2P file sharing directly into your browser.
A good example of this is the new Firefox Hello video and chat client that lets you talk securely to anyone else using an up-to-date Firefox, Chrome, or Opera browser, without the need to download any add-on, or configure any new settings.
Unfortunately for VPN users, WebRTC allows a website (or other WebRTC service) to directly detect your host machine’s true IP address, regardless of whether you are using a proxy server or VPN.
Given that WebRTC is potentially useful, it is something of a shame that the only way to prevent it from leaking your true IP address when using a VPN is to disable WebRTC in your browser completely. But there you go.
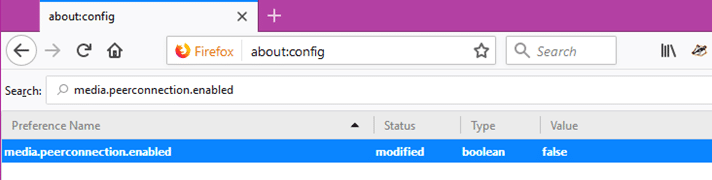
Type about:config into the URL bar to enter Firefox’s advanced settings, and change the media.peerconnection.enabled value to false. See below for more about about:config. This works for both Firefox Desktop and Firefox for Android.
Various Firefox browser add-ons can also disable WebRTC, including, uBlock Origin and NoScript.
Remove DRM (optional)
In order to watch videos on sites such as Netflix, Amazon Prime and Hulu, you must use Digital Rights Management (DRM). This encrypts the content and protects copyright by limiting what you can do with it.
Did you know? You can expand your Netflix library with a VPN? To find out how, check out our best VPNs for Netflix guide.
Back in 2015 Mozilla made the controversial decision to include DRM in Firefox. In many ways this was an understandable decision. Being able to play Netflix etc. content can be seen as necessary if Firefox is to stay cooperative with its rivals.
The decision infuriated many, however, because it requires bundling closed source code into the open source Firefox. This code is probably doing nothing other than exactly what it says it is doing, but since it is closed source there no way to know this for sure.
In order to mitigate this problem, Firefox runs DRM in a separate sandboxed container. In theory, this should prevent the DRM from doing any harm, even if it wanted to.
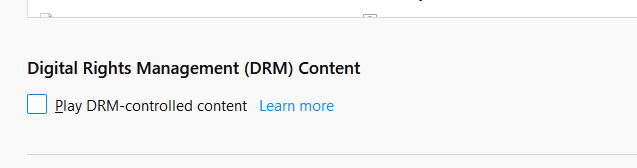
Open source purists and privacy-heads, however, may prefer to remove DRM from Firefox altogether. Do note that doing so will reduce functionality, as Firefox will no longer be able to play DRM-protected content.
- In Firefox Desktop go to Menu -> Settings -> General -> Digital Rights Management (DRM) Content and uncheck Play Digital Rights Management (DRM) Content.
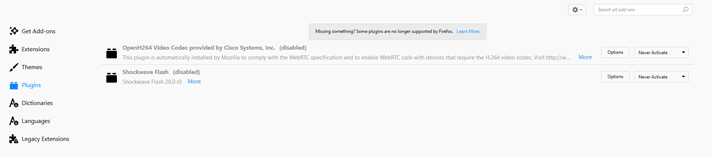
This will completely remove all HTML5 DRM code from your hard drive. - Go to Menu -> Add-ons -> Plugins and ensure Shockwave Flash is set to Never Activate.
![Firefox DRM Content]()
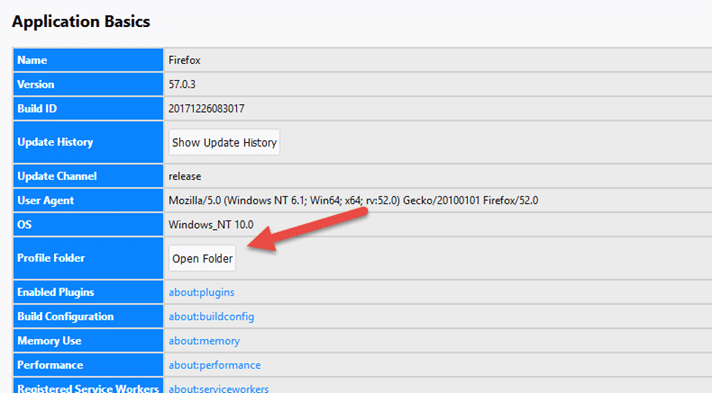
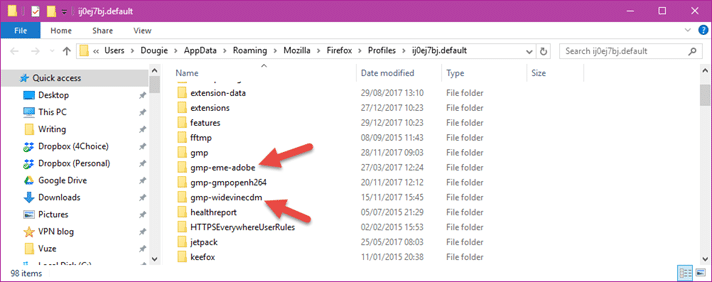
- Type about:supportinto the URL bar and hit enter. Scroll down to Application Basics -> Profile Folder and hit the Open Folder button.
![Disable Shockwave]()
- In the now open Profile Folder, find and delete the gmp-eme-adobe and gmp-widevinecdmsubfolders. Restart Firefox.
![Application Basics]()
It is not possible to remove all DRM from Firefox for Android, but it is possible to install Fennec F-Droid from the F-Droidrepository. This is a fork based on the latest Firefox release, but which strips out all closed source code from Firefox for Android – including DRM.
Using a VPN with Firefox
Plenty of the industry's best VPN services now offer browser extensions for Firefox, Chrome, and even Safari. These add-ons are stripped-back versions of a full VPN client that you can toggle on or off as you browse, and are generally easier to install and use. They're great for folks who want a simple way to geo-hop from location to location, VPN newbies, or anyone who might be unable to download a full VPN client at work or school.
A VPN (or Virtual Private Network) creates an encrypted tunnel for your traffic and conceals your original IP address. So, you'll be able to browse the web without worrying about who might be trying to monitor your activity (like your ISP, hackers, or even your government). This encryption vastly improves your online privacy and keeps your identity hidden, and also makes it possible to unblock content from around the globe! As a result, VPNs are vital for anyone looking to browse the web without restrictions, secure sensitive information, and boost their digital anonymity.
So, if you're interested in checking out a VPN browser extension for Firefox, we've listed our top five picks below – and be sure to visit our detailed guide for a more in-depth comparison of each of these services.
Extension limitations
Remember, a VPN browser extension will only secure your web browser! Any other apps (like Skype, Outlook, and your video games) won't benefit from its encryption – and you'll need to install a full VPN client onto your device in order to secure your entire network.

From $6.67/month
The best VPN for Firefox. A sleek, easy-to-use service that can unblock sites as easily as it secures your browser, with strong encryption and leak protection, and a 30-day money-back guarantee.
- ProPrivacy TrustScore:
- 10 out of 10
- Simultaneous connections
- 8
- Server locations
- 160
- Free trial
- No

From $2.19/month
The best value VPN for Firefox. Users get unlimited simultaneous connections and access to virtually any streaming service out there, so unblocking content is a breeze. With a 30-day money-back guarantee.
- ProPrivacy TrustScore:
- 9.9 out of 10
- Simultaneous connections
- Unlimited
- Server locations
- 140
- Free trial
- Yes

From $2.19/month
The best secure VPN for Firefox. A privacy-oriented, zero-logs policy that packs superb encryption and a huge number of servers to choose from. Also includes a 30-day money-back guarantee.
- ProPrivacy TrustScore:
- 9.8 out of 10
- Simultaneous connections
- Unlimited
- Server locations
- 154
- Free trial
- No

From $1.19/month
The best all-rounder VPN for Firefox. It can bypass network blocks and geo-restrictions, offers 10 simultaneous connections, and a 30-day money-back guarantee.
- ProPrivacy TrustScore:
- 9.7 out of 10
- Simultaneous connections
- 10
- Server locations
- 100
- Free trial
- No

From $3.99/month
The best streaming-friendly VPN for Firefox. A super-speedy service that can unblock Netflix US, and other sites, and boasts 188 dedicated streaming servers. With a 30-day money-back guarantee.
- ProPrivacy TrustScore:
- 9.6 out of 10
- Simultaneous connections
- 5
- Server locations
- 290
- Free trial
- No
Recommended Firefox Privacy and Security add-ons
All Firefox add-ons are free and open source software (FOSS).
uBlock Origin
uBlock Origin is a lightweight but powerful ad-blocker that pulls double duty as an anti-tracking add-on. It uses a number of blocking lists to filter unwanted content from appearing in your browser. The lists it comes with are pretty good, but I recommend also adding those compiled by EasyList and Fanboy.
Blocking ads and tracking scripts can break some web pages, making uBlock Origin’s on-the-fly whitelisting feature very handy. You can also toggle which types of elements are blocked (pop-ups, large media elements, cosmetic elements and remote fonts), or use the Element picker and Element Zapper modes to customize what is permitted to run on a web page.
uBlock Origin works very well in tandem with Privacy Badger, and I recommend using both together. It is also worth noting to avoid confusion, that uBlock Origin is recommended over the very similar uBlock add-on.
Privacy Badger
Developed by the Electronic Frontier Foundation (EFF), this is an excellent anti-tracking add-on that does double-duty as an ad-blocker. Although there is some overlap in function, Privacy Badger and uBlock Origin complement each other and are best run together.
Rather than using blocklists, Privacy Badger keeps track of scripts that are embedded in web pages. If it detects that a source is tracking you, it "springs into action, telling your browser not to load any more content from that source".
Privacy Badger allows you see which tracking scripts are present on a web page and which ones are actually tracking you. You can then decide how to deal with them (block, block cookies, or allow), or let Privacy Badger decide.
HTTPS Everywhere
An essential tool. HTTPS Everywhere was developed by the Electronic Frontier Foundation and tries to ensure that you always connect to websites using a secure HTTPS connection - if one is available.
It works because many websites can accept HTTPS connections, but use regular insecure HTTP ones by default. Just be aware that if no HTTPS connection is possible, HTTPS Everywhere will default to an insecure HTTP connection (although this can be changed in its settings).
It is, therefore, a good idea to keep an eye on the padlock icon in the URL that shows whether you are using an HTTPS connection.
NoScript
NoScript is a potent tool that gives you unparalleled control over what scripts are run on your browser. However, many websites will not play game with NoScript, and it requires a fair bit of technical knowledge to configure and tweak it to work the way you want it to.
It is easy to add exceptions to a whitelist, but even this requires some understanding of the risks that might be involved. Not for the casual user then, but for web-savvy power-users, NoScript is challenging to beat.
Note that if you use NoScript, you do not also need to use uBlock Origin + privacy Badger or uMatrix.
See here for some tips on getting the best out of NoScript. The last one is particularly worth paying attention to. It is worth keeping NoScript installed even if you "Allow Scripts Globally", as this still protects against nasty things such as cross-site scripting and clickjacking
uMatrix
Developed by the team behind uBlock Origin, uMatrix is something of a half-way house between that and NoScript. It provides a great deal of customizable protection but requires a fair bit of work and know-how to set up correctly.
uMatrix is not as hard to configure as NoScript and does not break as many sites. But neither is it as comprehensive.
Note that if you use uMatrix, then it is not necessary to also use uBlock Origin + Privacy Badger or NoScript.
Cookie AutoDelete
A drop-in replacement for the popular but now defunct Self-Destructing Cookies, Cookie AutoDelete automatically deletes HTTP (regular) cookies when you close the browser tab that set them. This provides a high level of protection from tracking via cookies without "breaking" websites.
Cookie AutoDelete also provides some protection against Flash/zombie cookies and ETags, and cleans DOM storage (although it can't clean local storage yet).
Note that Cookie AutoDelete and BetterPrivacy complement each other, and I recommend running them both together.
BetterPrivacy
This add-on controls Flash cookies. It should be configured to remove these automatically on a regular basis.
There is an argument that BetterPrivacy is now redundant as Flash is used much less by websites than it used to be. Personally, I think it is still worth running. It is recommended to run this add-on and Self-Destructing Cookies together.
Note that at time of writing BetterPrivacy has been removed by its author from official Firefox Add-on website. The WebExtensions version is in beta, however, so we should hopefully see it reappear soon.
Random Agent Spoofer
A web browser user agent tells website what type of computer, what OS, and what browser you are using. Many sites use this information to optimize their pages to improve user experience, but this information can be used for browser fingerprinting.
Random Agent Spoofer randomly changes what user agent information is given to a website. For example, it can tell a website that you are accessing it on an iPhone using Safari, rather than on a PC using Firefox.
Note that there is some debate on how effective Random Agent Spoofer and similar add-ons are at preventing Browser Fingerprinting. It is true that using an unmodified generic browser such as the Tor Browser is almost certainly better in this regard. But if you are using other add-ons which make your browser more unique, changing your user agent is probably useful.
Canvas Defender

Canvas fingerprinting is the most common form of browser fingerprinting. It uses a script that asks your browser to draw a hidden image, and uses tiny variations in how the image is drawn to generate a unique ID code which can then be used to track you. Canvas Defender helps prevent this by creating a unique and persistent noise that hides your real canvas fingerprint.
Note that at the time of writing, Mozilla has promised upcoming versions of Firefox will feature built-in canvas fingerprinting protection. If and when this becomes available, Canvas Defender should become redundant, Until then, however, I strongly recommend its use.
Decentraleyes
This add- aims to improve your privacy while browsing by hosting CND resources locally. When your browser requests one of these CDN resources, the application is blocked, and you are served up a local version instead.
If the above just sounds like techno-babble to you, please check out my Decentraleyes Review for a full explanation.
Bloody Vikings!
Bloody Vikings is an easy-peasy way to create temporary email addresses.
Just right-click in an email registration field, select ‘Bloody Vikings’ (or expand to see a choice of services), and a newly generated email address will be inserted into the field while a new browser tab opens to the temporary mailbox.
Mailvelope
PGP is by far the most secure way to send private emails. But it is a pain in the butt to use. Such a significant pain, in fact, that few people bother. Mailvelope is a browser add-on that allows end-to-end PGP encryption within Firefox.
It works with popular browser-based webmail services such as Gmail, Hotmail, Yahoo!, and GMX. It makes using PGP about as painless as it gets. However, it is not as secure as using PGP with a dedicated email client. Check out my detailed look at Mailvelope here.
keepasshttp-connector
KeePassis a fantastic open source password manager. keepasshttp-connector is a Firefox add-on that brings full browser integration to KeePass.
Please check out my KeePass Review for further details.
Privacy Settings
Firefox allows quite fine-grained control of its privacy settings, but to do this requires accessing its advanced configuration settings using about:config. I describe how to do this, plus provide an extensive list of privacy-related settings below.
Privacy Settings, however, allows you easy ‘one-click’ control of many of these settings using a simple GUI interface. Because it merely flips configuration settings, you can install the add-on, disable whichever settings you prefer, and then uninstall Privacy Settings to save browser resources.
How to make Firefox More Secure Using about:config
Built into Firefox are a number of "under the hood" settings. These can be changed to improve your privacy and security when browsing.
To access Firefox’s advanced configuration settings, type about:config into the search bar, and hit enter.
While it might be possible to do some damage, this warning seems a bit strong to us! Click "I accept the risk!" if you are feeling brave enough.
You will now see the configuration screen, with Preference Name’s listed in alphabetical order (by default).
To change a boolean entry (i.e. it has a true/false value), simply double-click anywhere on the entry line. To change an integer (i.e. numeric value), double-click the entry and enter a numeric value.
To change a string value, double-click the entry and enter the required text.
When you see an option in bold in the about:config pane, it has been changed from its default value.
Where an entry is marked with an asterisk*, I strongly suggest that you follow my advice.
Warning: Some websites rely on features we discuss disabling for security reasons below. Disabling these features will therefore "break" some websites (causing problems when using them, or even causing them to refuse to load altogether).
The good news is that simply re-enabling the relevant features will un-break the affected websites, so you may require some trial-and-error to find the right balance between maximum security and accessing the services you use.
browser.privatebrowsing.autostart
The Private Browsing mode was introduced to stop you leaving any embarrassing trails of what you have been up to for other users of your browser to find. Most importantly it stops (most) cookies and does not record any History of websites you have visited or forms you have filled in.
The critical thing to remember is that Private Browsing is excellent for protecting your privacy from others using the same computer, but does little to protect someone from the outside seeing what you get up to (e.g. your ISP).
Even if you are the sole user of a computer, it is still a good idea to always surf the internet in Private Browsing mode, thanks to its cookie blocking features in particular.
By setting this Preference to true you will automatically start Firefox in Private Browsing mode, so you will never forget to turn it on.
browser.safebrowsing.phishing.enabled*
Firefox ships with the Google Safe Browsing extension built-in and enabled by default. Designed to prevent phishing, it compares the websites you visit to a Google-run blacklist. This means that Google is constantly able to track you.
If you have installed our recommended Firefox extensions (see above) then you will gain no additional protection from Google Safe Browsing, while telling Google a great deal about your browsing history. I therefore strongly recommend that you turn it off by setting the value to false.
browser.safebrowsing.malware.enabled*
Safe Browsing (now renamed Phishing Protection) is basically a version of Google Safe Browsing licensed to Mozilla (but which still reports to Google). I, therefore, recommend that you set it to false, for the same reasons as above. Click here for the Mozilla help entry.
Note that there are a lot of browser.safebrowsing.xxx settings, and it may be worth going through them all and disabling them/deleting their string values.
browser.startup.homepage
By default, Firefox will start on the Mozilla Firefox Start Page, displaying a Google search box. Google (along with most major commercial search engines such as Bing! and Yahoo!) stores a great deal of information about you, including a record of the searches you make.
To start on a different page, simply enter the website address of your preferred choice. I use StartPage, but please check out our Privacy Search Engines Group Review for a rundown of the best options available. Click here for the Mozilla help entry.
browser.startup.page
If you prefer to start Firefox on a blank page, change this setting to ‘0
datareporting.healthreport.uploadEnabled
You can see details about your Firefox browser’s performance and stability any time by reviewing the Firefox Health Report (Firefox tab -> Help -> Firefox Health Report). By default, this report is periodically sent to Mozilla (in anonymous aggregate form) to help it understand problems and plan future developments.
For maximum security, you should prevent this by setting this entry to false (you will still be able to see your report, it just won’t be sent to Mozilla).
dom.event.clipboardevents.enabled*
If you cut, copy or paste something from a website, then the website owners can get notified of exactly which part of a webpage you have cut, copied or pasted. If they wish, they can then record or modify the text, or prevent you from copying (etc.). They can also prevent you from pasting text into online forms.
By setting this entry to false you prevent websites knowing where you pasted their text, and as a side benefit will be able to bypass restrictions on cutting and pasting).
dom.storage.enabled*
I discuss the dangers of DOM storage (also known as web storage) in "More things that go bump in the night: HTTP ETags, Web Storage, and ‘history stealing". Basically, this way of storing information within web browsers is one of the most pernicious methods used by commercial internet companies to track you across the web and is growing in popularity as netizens become more aware of the danger of ‘regular’ cookies.
Fortunately, DOM storage is easy to turn off by setting this entry to false.
Update: Thanks to feedback from readers, it is clear that setting dom.storage.enabled to false can "break" some website. Changing this setting should, therefore, be done with caution.
geo.enabled*
When you visit a "location-aware" website you will be asked if you want to share your location. If you answer yes then Firefox will send information about nearby wireless access points and your computer’s IP address to Google Location Service, and then pass that information on to the website (a random client identifier is also assigned by Google, which expires every 2 weeks).
Although you should be asked every time this happens, and need to give your explicit consent, you can prevent giving consent accidentally or through carelessness by turning this feature off (set the value to false). Click here for the Mozilla help entry.
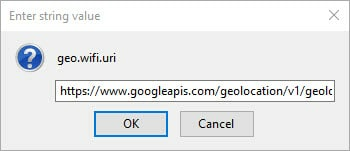
geo.wifi.uri
This setting determines the geolocation service used (Google Location Service by default). If you set geo.enabled (above) to false, then this setting shouldn’t matter. If it makes you feel better, however, then you can change it to 127.0.0.1 (also known as localhost or the ‘loopback address’).
In theory, this setting could point to an alternative service, but none such really exist at the moment. Click here for the Mozilla help entry.
media.peerconnection.enabled
Web Real-Time Communication (WebRTC) is a potentially useful standard that allows browsers to incorporate features such as voice calling, video chat, and P2P file sharing directly into your browser.
A good example of this is the new Firefox Hello video and chat client that lets you talk securely to anyone else using an up-to-date Firefox, Chrome, or Opera browser, without the need to download any add-on or configure any new settings.
Unfortunately for VPN users, WebRTC allows a website (or other WebRTC service) to directly detect your host machine’s true IP address, regardless of whether you are using a proxy server or VPN. Some modern VPN clients will block WebRCT leaks, but it is safest to disable in your browser entirely. To do so, change this value to false.
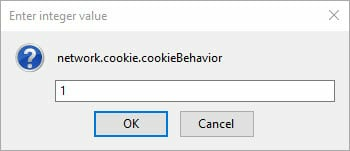
network.cookie.cookieBehavior
If you use a good cookie manager such as Cookie AutoDelete (recommended), then you will not need to touch this preference. If not, then it is probably a good idea to set it to ‘1’ (only cookies from the originating server are allowed).
network.cookie.lifetimePolicy
Again, using the Cookie AutoDelete add-on is probably the best policy, but if you prefer not to, then you can control when cookies expire by setting this setting to ‘2’ (the cookie expires at the end of the session (when the browser closes)).
network.dns.disablePrefetch
Firefox improves page load times by resolving domain names ‘proactively and in parallel’ (i.e. it pre-fetches the information). In their paper ‘DNS Prefetching and Its Privacy Implications: When Good Things Go Bad’, Srinivas Krishnan and Fabian Monrose argue that this practice can lead to "privacy threats that are ripe for abuse. More specifically… where it is possible to infer the likely search terms issued by clients using a given DNS resolver".
DNS prefetching can be turned off by setting this value to true. If you can’t find this setting then you will have to add it manually by right-clicking on the about:config screen, selecting ‘New’ -> ‘Boolean’ and entering ‘network.dns.disablePrefetch’ into the dialog box.
network.http.sendRefererHeader
When you click on a hyperlink, the page you go to can request information about the page you clicked the link from. This information is contained in the ‘referer header’, and can be used to track you across a website.
Furthermore, Javascript scripts can "see" and reference the referrer header if this setting is turned on. Although Mozilla cautions that disabling referrer headings may cause problems with some websites, we advise changing the setting to ‘0’ (never send the referer header or set ‘document.referrer’).
network.http.sendSecureXSiteReferrer*
More or less the same as the entry above, except that it allows you to be tracked across websites. You can disable this setting by changing the value to false.
network.prefetch-next*
Firefox speeds up the browsing process by scanning links on a webpage, and pre-downloading linked-to webpages when idle. Although disabling this preference will slow down browsing somewhat, from a privacy perspective you really should set it to false. .
privacy.donottrackheader.enabled*
Most modern browsers now support a "Do not track’ feature, which asks websites not to track you, and Firefox is no exception. While this should most certainly be turned on (set to true), you should be aware that compliance from websites is entirely voluntary. So the protection it affords can be considered fairly minimal.
privacy.donottrackheader.value*
While the privacy.donottrackheader.enabled (above) setting determines whether a ‘Do not track’ instruction is sent to a website, this setting determines what that instruction actually says.
You should, therefore, set it to 1 to request that websites do not track you (a header stating consent to being tracked is sent to all websites if privacy.donottrackheader.enabled is set True).
privacy.trackingprotection.enabled
This enables a blocklist based on Disconnect’s blocklist, to help prevent cross-site tracking. Once Tracking Protection is activated, you will see a shield in your address bar whenever Firefox is blocking either tracking domains or mixed content.
As a side-benefit, this setting also causes pages to load 44 percent quicker on average, data usage drops by 29 percent when connecting to the top 200 Alexa websites, and the number of HTTP cookies stored by the browser falls by 67.5%.
toolkit.telemetry.enabled
Telemetry covers all sorts of statistical data related to your browser’s performance, usage, and responsiveness. Firefox can send anonymous reports with this data to Mozilla, which is of great assistance to developers, and for this reason, you may consider turning it on, but for maximum privacy, you should check that it is false. Click here for the Mozilla help entry.
Additional Notes
Private Browsing (aka incognito mode)
Like most modern browsers, Firefox offers a Private Browsing mode. Unfortunately, this feature is often poorly understood. This can be very dangerous.
When you open a Private Window, pages you visit are not added to the browser’s History, text you enter into forms and search bars is not saved, passwords, downloads, cookies, and temporary internet files are also not saved.
This makes Private Browsing great at hiding what you get up to on the internet from family members and others who have access to your computer. There is a reason private browsing is often referred to as porn mode!
Firefox 57+ enables Tracking Protection in Private Browsing by default, but in general, Private Browsing does not hide what you get up to on the internet from your ISP. Nor does it hide your real IP address from websites you visit.
Private Browsing is therefore great for hiding what you get up to online from your family, but will not hide what you get up to online from anyone else. To hide what you get up to online from the rest of the world, you need to use a VPN or Tor.
Firefox Privacy Conclusion
Firefox is an excellent browser for privacy and security, but there are lots of things you can do make it even more so! The elephant in the room is that modifying your Firefox browser in many ways makes you more unique, and therefore more susceptible to browser fingerprinting techniques. Unfortunately there is currently no way to square this circle.