Although strong encryption has recently become trendy, websites have been routinely using strong end-to-end encryption for the last 20 years. After all, if websites could not be made very secure, then no form of online commerce such as shopping or banking would be possible. The encryption protocol used for this is HTTPS, which stands for HTTP Secure (or HTTP over SSL/TLS). It is used by any website that needs to secure users’ and is the fundamental backbone of all security on the internet.
HTTPS is also increasingly being used by websites for which security is not a major priority. This is in large part heightened concern over general internet privacy and security issues in the wake of Edward Snowden’s mass government surveillance revelations.
Projects such as the EFF’s Let’s Encrypt initiative, Symantec's Encryption Everywhere program and Mozilla choosing to depreciate non-HTTPS secured search results, however, have accelerated the general adoption of the protocol.
So what does HTTPS do?
When you visit a non-secure HTTP website all data is transferred unencrypted, so anyone watching can see everything you do while visiting that website (including things such as your transaction details when making payments online). It is even possible to alter the data transferred between you and the web server.
With HTTPS, a cryptographic key exchange occurs when you first connect to the website, and all subsequent actions on the website are encrypted, and therefore hidden from prying eyes. Do note that anyone watching can see that you have visited a certain website, but cannot see what individual pages you read, or any other data transferred while on that website.
For example, the ProPrivacy website is secured using HTTPS. Assuming that you are not using a while reading this web page your ISP can see that you have visited proprivacy.com, but cannot see that you are reading this particular article.
If you are using a VPN, then your VPN provider can see the same information, but a good one will use shared IPs so it doesn’t know which of its many users visited proprivacy.com, and it will discard all logs relating to the visit anyway.
Note that HTTPS uses end-to-end encryption, so all data passing between your computer (or smartphone, etc.) and that website is encrypted. This means that you can safely access HTTPS websites even when connected to unsecured public WiFi hotspots and the like.
How do I know if a website is secure?
It is easy to tell if a website you visit is secured by HTTPS:
- In all, you will see a locked padlock icon to the immediate left of the main URL/Search bar.
- In most, the web address will start with https://. (Unsecured websites start with http://, but both https:// and http:// are often hidden.)
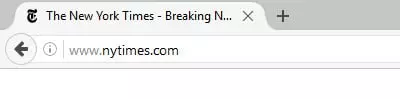
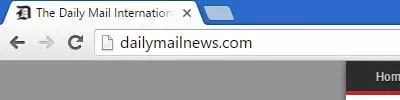
Here is are examples of unsecured websites (Firefox and Chrome). Notice that the web addresses (URLs) do not begin with https: and that no padlock icon is displayed to the left of the search bar
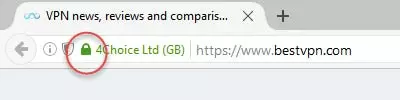
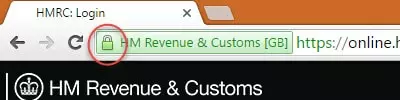
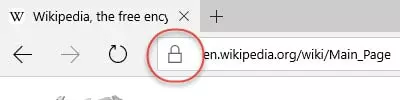
Here are some secure HTTPS websites in Firefox, Chrome, and Microsoft Edge. Although they all look slightly different, we can clearly see a closed padlock icon next to the address bar in all of them. Note that unlike most browsers, Edge does not show https:// at the beginning of the URL. You will also notice that icon can be either green or grey…
What is the difference between green and grey padlock icons?
If a padlock icon is shown, then the website is secure. If the icon is green, however, it denotes that the website has presented your browser with an Extended Validation Certificate (EV). These are intended to verify that the SSL certificate presented is correct for the domain and that the domain name belongs to the company you would expect to own the website.
In theory, then, you should have greater trust in websites that display a green padlock. In practice, however, the validation system can be confusing.
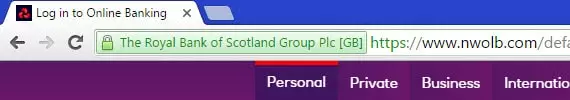
For example, in the UK, NatWest bank’s online banking address (www.nwolb.com) is secured by an EV belonging to what the casual observer might think of as a high-street competitor - the Royal Bank of Scotland. Unless you know that NatWest is owned by RBS, this could lead mistrust the Certificate, regardless of whether your browser has given it a green icon.
Confusion can also be caused by the fact that different browsers sometimes use different criteria for accepting Firefox and Chrome, for example, display a green padlock when visiting Wikipedia.com, but Microsoft Edge shows a grey icon.
In general, common sense should prevail. If you are visiting Google and the URL is www.google.com, then you can be pretty certain that the domain belongs to Google, whatever the of the padlock icon!
Other padlock icons
You may also encounter other padlock icons that denote things such as mixed content (website is only partially encrypted and doesn't prevent eavesdropping) and bad or expired SSL certificates. Such websites are not secure.
Additional information
In all browsers, you can find out additional information about the SSL certificate used to validate the HTTPS connection by clicking on the padlock icon.
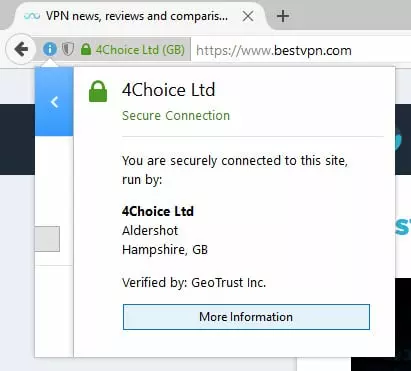
Most browsers allow dig further, and even view the SSL certificate itself
How does HTTPS actually work?
The name Hypertext Transfer Protocol (HTTP) basically denotes standard unsecured (it is the application protocol that allows web pages to connect to each other via hyperlinks).
HTTPS web pages are secured using TLS encryption, with the and authentication algorithms determined by the web server.
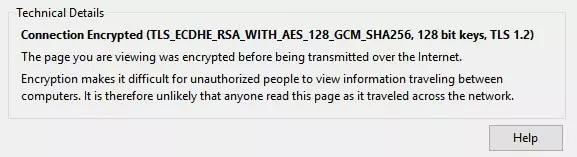
Most browsers will give you details about the TLS encryption used for HTTPS connections. This is the encryption used by ProPrivacy, as displayed in Firefox. More information on many of the terms used can be found here
To negotiate a new connection, HTTPS uses the X.509 Public Key Infrastructure (PKI), an asymmetric key encryption system where a web server presents a public key, which is decrypted using a browser’s private key. In order to ensure against a man-in-the-middle attack, X.509 uses HTTPS Certificates – small data files that digitally bind a website’s public cryptographic key to an organization’s details.
An HTTPS Certificate is issued by a recognised Certificate Authority (CA) which certifies the ownership of a public key by the named subject of the certificate – acting in cryptographic terms as a trusted third party (TTP).
If a website shows your browser a certificate from a recognised CA, your browser will determine the site to be genuine (a shows a closed padlock icon). And as noted earlier, Extended Validation Certificates (EVs) are an attempt to improve trust in these SSL certificates.
HTTPS Everywhere
Many websites can use but don’t by default. In such it is often possible to access them securely simply by prefixing their web address with https:// (rather than ://). A much better solution, however, is to use HTTPS Everywhere.
This is a free and open source browser extension developed by a collaboration between The Tor Project and the Electronic Frontier Foundation. Once installed, HTTPS Everywhere uses "clever technology to rewrite requests to these sites to HTTPS.”
If an HTTPS connection is available, the extension will try to connect you securely to the website via HTTPS, even if this is not performed by default. If no HTTPS connection is available at all, you will connect via regular insecure HTTP.
With HTTPS Everywhere installed you will connect to many more websites securely, and we therefore strongly recommend installing it. HTTP Everywhere is available for Firefox (including Firefox for Android), Chrome and Opera.
Problems with HTTPS
Fake SSL Certificates
The biggest problem with HTTPS is that the entire system relies on a web of trust – we trust CAs to only issue SSL certificates to verified domain owners. However…
There exist some 1200 CAs that can sign certificates for domains that will be accepted by almost any browser. Although becoming a CA involves undergoing many formalities (not just anyone can set themselves up as a CA!), they can be (and are) leaned on by governments (the biggest problem), intimidated by crooks, or hacked by criminals to issue false certificates.
This means that:
- With hundreds of Certificate Authorities, it takes just one ‘bad egg’ issuing dodgy certificates to compromise the whole system
- Once a certificate is issued, there is no way to revoke that certificate except for the browser maker to issue a full update of the browser.
If your browser visits a compromised website and is presented with what looks like a valid HTTPS certificate, it will initiate what it thinks is a secure connection, and will display a padlock in the URL.
The scary thing is that only one of the 1200+ CAs need to have been compromised for your browser accept the connection. As this EFF article observes,
In short: there are a lot of ways to break HTTPS/TLS/SSL today, even when websites do everything right. As currently implemented, the Web’s security protocols may be good enough to protect against attackers with limited time and motivation, but they are inadequate for a world in which geopolitical and business contests are increasingly being played out through attacks against the security of computer systems.
Unfortunately, this problem is far from theoretical. Equally unfortunately, there no generally recognised solutions, although together with EVs, public key pinning is employed by most modern websites in an attempt to tackle the issue.
With public key pinning the browser associates a website host with their expected HTTPS certificate or public key (this association is ‘pinned’ to the host), and if presented with an unexpected certificate or key will refuse to accept the connection and issue you with a warning.
The Electronic Frontier Foundation (EFF) did also start an SSL Observatory project with the aim of investigating all certificates used to secure the internet, inviting the public to send it certificates for analysis. As far as I am aware, however, this project never really got off the and has lain dormant for years.
Traffic analysis
Researchers have shown that traffic analysis can be used on HTTPS connections to identify individual web pages visited by a target on HTTPS-secured websites with 89 accuracy.
Although worrying, any such analysis would constitute a highly targeted attack against a specific victim.
HTTPS Conclusion
Although not perfect (but what is?), HTTPS is a good security measure for websites. If it wasn’t, then none of the billions of financial transactions and transfers of personal data that happen every day on the internet would be possible, and the internet itself (and possibly the world economy!) would collapse overnight.
That HTTPS implementation is increasingly becoming standard on websites is great for both and for privacy (as it makes the job of the NSA and its ilk much harder!).
The main thing to remember is to always check for a closed padlock iconwhen doing anything that requires security or privacy on the internet. If you are using an insecure internet connection (such as a public WiFi hotspot) you can still surf the web securely as long as you only visit HTTPS encrypted websites.
If for any reason you are worried about a website, you can check its SSL certificate to see if it belongs to the owner you would expect of that website.
The TL is that thanks to HTTPS you can surf websites securely and privately, which is great for your peace of mind!
