After years of awareness-raising campaigns by privacy activists, which culminated this year in the European Union passing a ‘cookie law’ banning any EU company or any company targeting EU citizens from placing ‘non-essential’ cookies on users computers without their consent, most internet users now know about cookies.
Unfortunately, most of what people know about cookies regards HTTP (or ‘normal’) cookies; small text files that are left in your browser’s cookie folder and that, in addition to doing lots of useful things such as remembering your passwords and favorite website preferences, can be used to identify you and track your movements across the World Wide Web.
Understandably concerned about the privacy issues involved, the internet-using public has fought back and taken increasing effective measures to block, delete or control cookies, assisted by the fact most modern browsers have added cookie management and blocking features.
Perhaps unsurprisingly, marketing and analytics companies have looked for ways to circumvent these measures and to continue uniquely identifying and tracking internet users. A primary means of doing this has been through the use of supercookies.
What is a supercookie?
Supercookie is a catch-all term used to refer to bits code left on your computer that performs a similar function to cookies, but which are much more difficult to find and get rid of than regular cookies. The most common type of supercookie is the Flash cookie (also known as an LSO or Local Shared Object), although HTTP ETags and Web Storage also fall under the moniker. In 2009 a survey showed that more than half of all websites used Flash cookies.
The reason that you may never have heard of supercookies, and why they are so hard to find and get rid of, is that their deployment is deliberately sneaky and designed to evade detection and deletion. This means that most people who think they have cleared their computers of tracking objects have likely not.
The EU ‘cookie law’ does encompass supercookies within its generic description, but as the law has been very vaguely worded about what constitutes a ‘bad’ cookie, and has been poorly enforced anyway (not to mention that most sites demand you accept their use of cookies if you wish to continue using them), its effectiveness at curbing supercookie use (or even regular HHTP cookie use other than by raising people's awareness of the issue) has been minimal at best.
Apple’s stand against Flash’s various insecurities however, has helped contribute to Flash Player’s growing obsolescence, with HTML5 increasingly fulfilling the functions once more commonly performed by Flash. Combined with support for LSA deletion by the major browsers, this has led to a decline in the use of Flash cookies, although they remain a substantial menace to internet users worried about tracking.
Flash Cookies and Zombie Cookies
The most common kind of supercookie is a Flash cookie which uses Adobe’s multimedia Flash plugin to hide cookies on your computer that cannot be accessed or controlled using your browser’s privacy controls (at least traditionally, most major browsers now include deletion of Flash cookies as part of their cookie management).
Because these cookies are stored outside the browser you cannot protect yourself by using a different browser (for example one for your banking website and another for riskier web surfing), as the Flash cookies will be available to all browsers (i.e. a cookie acquired when using Chrome will also be available to websites when using Firefox). In addition to this, Flash cookies can hold up to 100kb rather than just the 4kb held by HTTP cookies.
One of the most notorious (and freaky!) kinds of Flash cookie is the ‘zombie cookie’, a piece of Flash code that will regenerate normal HTTP cookies whenever they are deleted from a browser’ cookie folder.
How to deal with Flash cookies
Change your Flash preferences
This is always worth doing, although some LSOs seem adept at evading the preferences settings.
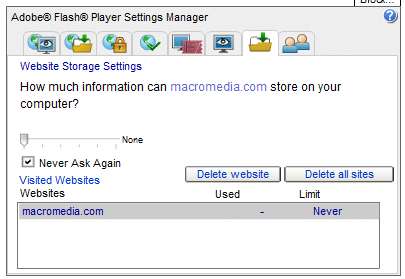
1. To remove existing site cookies go to the Adobe Website Storage Settings Panel, where will you see a list of Flash cookies on your computer. If you recognize any of the websites in the list and visit them regularly, then you may want to keep their cookies as they can provide useful functionality, but you can delete the others.
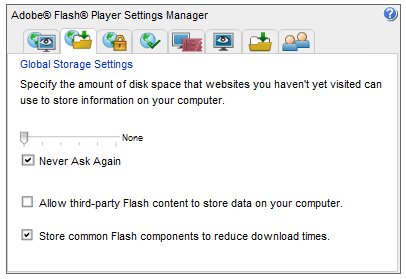
2. To prevent new sites from writing cookies, go to the Adobe Global Storage Settings Panel (or just click on the Global Storage Settings tab in the Settings Manager), drag the slider to ‘None’, and click ‘Never Ask Again’. Note that doing this may create problems with websites that rely on Flash functionality.
Manually delete Flash cookies This is also a good way to check that other methods have worked properly.
- In Windows open an Explorer window and type ‘%appdata%’ into the search bar. Double-click Macromedia -> Flash Player -> macromedia.com -> support’ -> flashplayer -> sys (we told you they were hidden away!). Any folders you see (which should contain a .sol file, which is the actual cookie) can be deleted.
- In OSX try going to Users -> username -> Library -> Preferences -> Macromedia -> Flash Player-> and look for any .sol files in the folders
- In Linux go to home -> username/ .macromedia -> Flash_Player -> macromedia.com -> support -> flashplayer -> sys, or run the command ‘find ~/.macromedia/ -type f -name settings.sol -exec rm -v {} \;’
Use CCleaner to automatically delete Flash cookies
CCleaner is a great tool for clearing the rubbish out of your system, but by default it does not clear out Flash cookies. To set CCleaner to clean Adobe Flash Cookies:
- In CCleaner, click the Cleaner icon and then the Applications tab.
- Under Multimedia, select Adobe Flash Player.
[Note. As of 2026, this is an old article. Most of the information remains current, but the use of CCleaner is no longer recommended.]
Use a dedicated Flash cookie cleaner utility
Examples include GrekSoft Flash Cookie Remover (Windows) and FlushFlash (Windows and OSX).
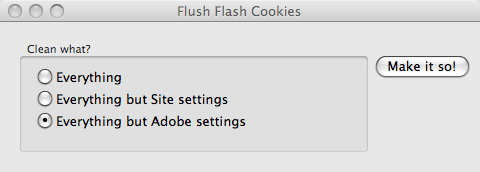
Flush Flash for Mac
Use Google Chrome or Internet Explorer to delete Flash Cookies
Modern versions of Chrome, Internet Explorer (IE8+), and Firefox work with Flash Player 10.3+ to delete Flash cookies automatically, using the browsers’ built-in Clear History functions. While we applaud this move, which uses the NPAPI ClearSiteData API, it is not perfectly implemented and we and we found LSOs on our system after using it.
Block Flash cookies in Android
Apple led the charge when it came to making a stand against Flash, and iOS users do not have to worry about LSOs, although they do miss out on the functionality provided by Flash. Android 4.1 also dropped support for Flash, although older devices may still have it installed, and those who value the fact that much of the web still relies on Flash can still manually sideload the .apk. If you do have Flash installed, then you will be able to find an icon for ‘Flash Player settings’ in the app drawer. To turn off Flash cookies, go to ‘Local Storage’ and select ‘Never’.

Use browser plugins
A number of browser plugins exist which can block or manage Flash cookies, the best example of which is uBlock Origin. Unfortunately, using these plugins increases the uniqueness of your browser and therefore makes you more vulnerable to Fingerprinting, so we do not recommend them.
Conclusion
Flash cookies are insidious things, but growing general awareness of cookies, decreasing use of Flash, and support from the major browsers for the NPAPI ClearSiteData API, means that their threat has diminished somewhat.
Unfortunately, this also means that in the ongoing arms war waged against the internet-using public by unscrupulous marketing and analytics firms, new techniques are being developed and deployed to identify individuals and track them across the web (and otherwise perform functions similar to traditional cookies).
The most alarming and prevalent of these is browser fingerprinting, which we discuss in detail here, but other forms of supercookie (HTTP ETags and Web Storage) and ‘history stealing’ (also very scary) are also deployed, which we discuss here.
