Privacy is important, and as we live our lives ever more in the digital space, it is natural to worry about whether our digital privacy is being invaded. Technologies such as VPN services can be very effective at hiding what we do online, but they do not help if someone has direct access to your computer and is using it without your consent.
This may sound rather paranoid, but a recent study by ProPrivacy.com found that a shocking 63 percent of respondents admitted to looking at their partner’s phone when they were out of the room, while almost 47 percent had checked their partner's browsing history. These are not reassuring figures.
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Tell-tale signs
- Check your browsing history. If it shows any websites that you have visited then you may well have an intruder.
- Check recent files in your file manager (such and Windows File Explore or macOS Finder). Again, if anything has been opened that you didn’t open then it is time to worry.
- A more tech savvy intruder may try to cover their tracks by deleting your browsing or file history so that you can’t take the above steps. So if you find either of these mysteriously deleted, then it may indicate an uninvited guest.
- It may be a little obvious, but if your mouse cursor starts to move without you controlling it then it’s time to panic.
It is also possible to see who has logged into your computer and at what time using your platform’s built-in logging functionality. If you are the sole user of of your computer then lookout for logons at times you know that you were not using your computer.
How to check logons in Windows
Note that full login auditing is only available using Windows Professional. Windows Home users are limited to seeing only successful logons, but this should be enough to alert you that someone is using your PC without permission.
The instructions below are for Windows 10, but are similar for previous versions of Windows.
1. Right-click Start -> Event Viewer.

2. Look for Events with Event ID: 4625, Task Category: Logon.

3. You can double-click on an event for more details.

You can also check to see if anyone else is remotely logged into your computer. Right-click Start -> Command Prompt -> type query user and hit enter.
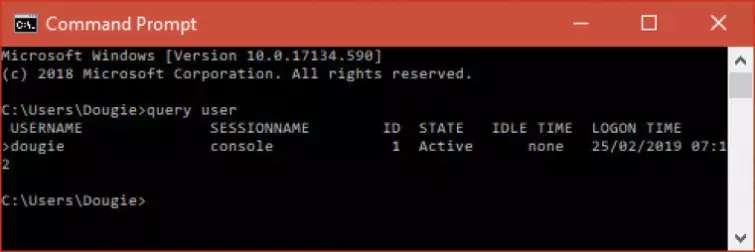
I’m rather relieved to see that the only person logged in is me, myself, and I.
How to check logons in macOS and Linux
Open Terminal. In macOS this can be done using Launchpad or going to Applications -> Utilities -> Terminal. In Ubuntu by going to Show Applications -> Terminal.
Type last and hit enter.

You will now be able to see all recent logons, together with a timestamp. While you are there, you might want to check that no other users are remotely logged in via SHH or telnet. Type who into terminal and hit enter.
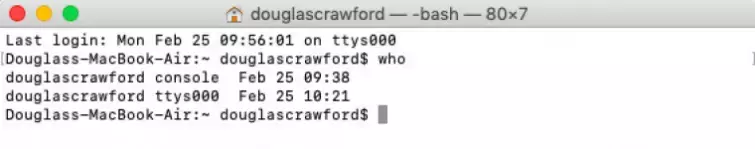
Again, I’m pleased to see that I don’t have company.
What to do if someone is using your computer without your consent
Change your logon password
The first thing you should do if you suspect a digital intruder is change your logon password to something that is strong and that no-one will be able to guess. Consider using a secure passphrase (a sentence made up of easy to remember but random words plus spaces), as this is almost always more secure than using a single-word password.
Use two-factor authentication for logon
One-factor authentication secures your logon using something know i.e. your logon details. Two-factor authentication (2FA) provides additional security by requiring that you also validate your identity using something only you physically have.
Without this additional thing (such as a YubiKey) it will not be possible to login to your computer, even if an intruder knows (or can guess) your password.
Always logout or enable screen lock whenever you leave your computer unattended
Doing this will prevent all but the most tech savvy intruder from physically accessing your computer when you are not there.
Encrypt your hard drives
If you are worried about a technically sophisticated intruder physically accessing your computer when you are away, then you should enable full-disk encryption to secure your data.
Windows 10 Pro users can turn on Bitlocker full-disk encryption by going to Control Panel -> BitLocker Drive Encryption, while all Windows users can secure their drives using open source VeraCrypt.

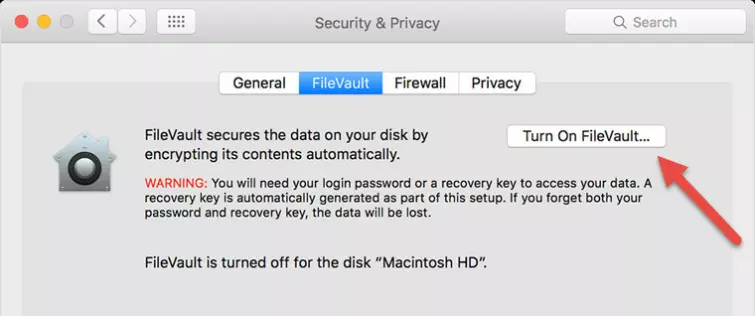
Mac users can turn on FileVault by going to System Preferences -> Security & Privacy -> FileVault tab.
Linux users have the built-in dm-crypt full-disk encryption program, although many people prefer combining this with the more flexible Linux Unified Key Setup (LUKS) key management tool. A good guide for this is available here.
Use a good anti-virus program
And keep its definitions up to date. Most viruses distributed criminal hackers these days are either keyloggers which hoover up all your password as you type them, or ransomware which locks you out of your computer unless you pay ransom money.
But other types of virus exist, including ones that allow an adversary to gain full control over your commuter. The only real defense against these is to use a good virus checker and maintain good internet hygiene (such as not opening email attachments from unknown sources, not visiting pirate websites, and suchlike).
Use your webcam to catch intruders!
It may sound a little extreme, but in an office environment it may not be enough to simply prevent someone from accessing your computer when you’re out of the room. If you have an enemy in the workplace then your entire career might rely on identifying who they are!
Lockscreen Pro for Windows is an open source app that can take a snapshot using your PC’s webcam every time someone either logs on or tries to logon unsuccessfully. The Mac App Store features a number of lock screen apps with similar functionality, although it must be said that none of them are terribly well-reviewed.
