For a long time TrueCrypt was the go-to full disk encryption solution of choice for security professions (it was recommended by Edward Snowden, and successfully prevented the UK police from accessing files carried by Glen Grunewald’s partner, David Miranda).
The security world was therefore extremely alarmed when the TrueCrypt developers withdrew their product under very suspicious circumstances (a situation which led to no small amount of general paranoia). At the time, a crowdfunded full audit of the software was being performed, Phase I of which had recently given it the all-clear.
The withdrawal of TrueCrypt by its developers threw the auditing project into some disarray, but it was finally decided to continue onto Phase II and finish the audit. This was completed at the beginning of April 2015, and although some problems were discovered, the report (as summarized in this blog post) found that,
‘Truecrypt appears to be a relatively well-designed piece of crypto software. The NCC audit found no evidence of deliberate backdoors, or any severe design flaws that will make the software insecure in most instances.’
This is great news, but leaves the problem that TrueCrypt is no longer supported. With some known weaknesses, plus the fact that no more updates will become available, it is therefore difficult to recommend using TrueCrypt these days…. so enter VeraCrypt…
VeraCrypt
VeraCrypt is a fully audited and open source fork of TrueCrypt that ‘solves many vulnerabilities and security issues found in TrueCrypt.’ It is also under active development, and is therefore likely to be improved and any remaining flaws patched in due time.
With VeraCrypt you can:
- Create a virtual encrypted disk (volume) which you can mount and use just like a real disk (and which can be made into a Hidden Volume)
- Encrypt an entire partition or storage device (e.g. a hard drive or USB stick)
- Create a partition or storage drive containing an entire operating system (which can be hidden)
All encryption is performed on-the-fly in real-time, making VeraCrypt transparent in operation. It should be noted, however, that groovy as this ability to mount an encrypted drive is (and it is one of the things that makes VeraCrypt a great program), it does mean that cryptographic keys are stored in temporary memory (RAM) during use, which can theoretically expose VeraCrypt users to the possibility of attack through the use of pre-installed keyloggers and other malware.
Hidden volumes and hidden operating systems provide plausible deniability, as it should be impossible to prove they exist (as long as all the correct precautions are taken). In Part 2 of this article we explore hidden volumes in detail.
VeraCrypt is available for Windows, OSX and Linux. Our how-to guide was written for Windows 8.1, but the basics should more or less the same for any operating system (and other forks or versions of TrueCrypt).
Note that unlike Ciphershed, VeraCrypt is not compatible with TrueCrypt volumes (see the end of this article for more information on this subject).
How to create and use a simple VeraCrypt container
Creating a container
The simplest way to use VeraCrypt is to create an encrypted container within a file. This file behaves just like any other file, and can be moved, deleted, renamed etc. as if it was a normal file.
1. Download VeraCrypt, install and run it, then click ‘Create Volume’ on the main screen.
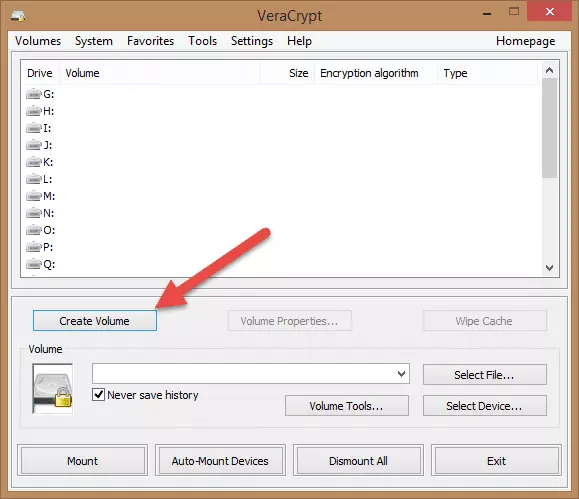
2. Make sure the ‘Create an encrypted file container’ radio button is selected and click ‘Next’.
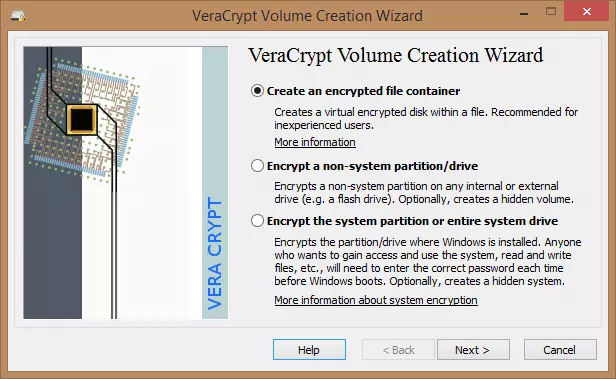
3. Make sure that ‘Standard VeraCrypt volume’ is selected and click ‘Next’.
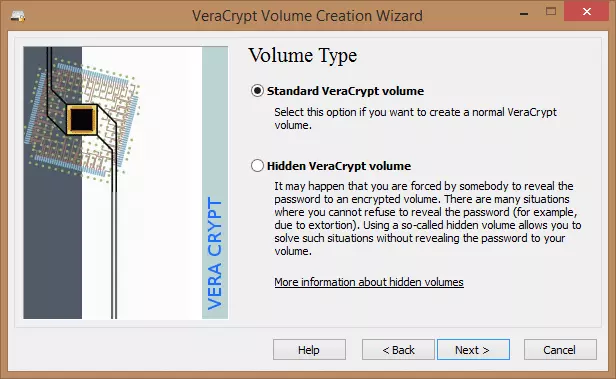
4. Click ‘Select File’, choose where you want the file saved, and pick a name for the file. Do not select an already existing file as VeraCrypt will delete it and replace it with a new VeraCrypt container.
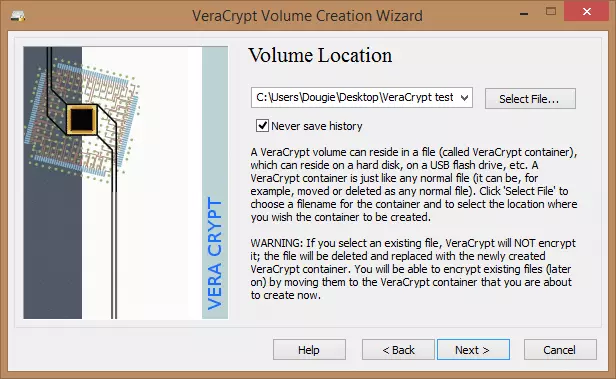
5. Choose an encryption algorithm and a hash algorithm. Information is provided on each encryption algorithm to help you choose one that is right for you. Generally speaking, the stronger the encryption, the longer the encryption/decryption process will take.
You can benchmark how fast the encryption/decryption takes, and test that all the algorithms are working properly.
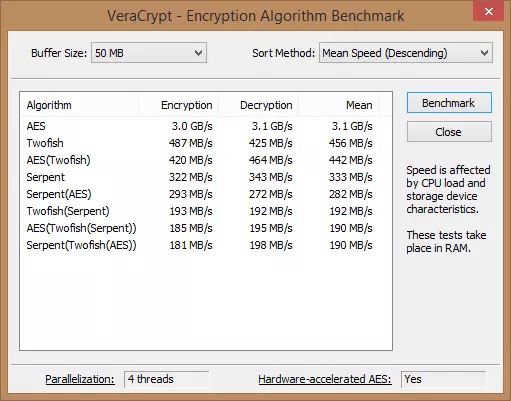
Although not as fast as AES, we prefer Twofish because we are suspicious of anything NIST certified (we explain why here.) We’ll also go with the Whirlpool hash algorithm for the same reason (see the full documentation for more info on this subject)
6. Choose how big you want the file to be. It can be any size up the available free space on the drive it is located.
7. Chose a password. This is a vital step; if your data is worth encrypting then it is worth protecting with a good password. The wizard offers some good advice on choosing a strong password (it is possible to use a keyfile instead, but for simplicity in this beginner’s tutorial we’ll just stick to using a password)
8. In the ‘Volume Format’ screen you can choose which file system to use. We’ll go for FAT to maintain maximum compatibility across devices and platforms. Moving your mouse pointer around the window increases the cryptographic strength of the encryption keys by introducing a truly random element (which increases security), so you should wiggle it around for at least 30 seconds. When you are done, click ‘Format’ and wait for the confirmation dialogue (then click ‘OK’ and ‘Exit’).
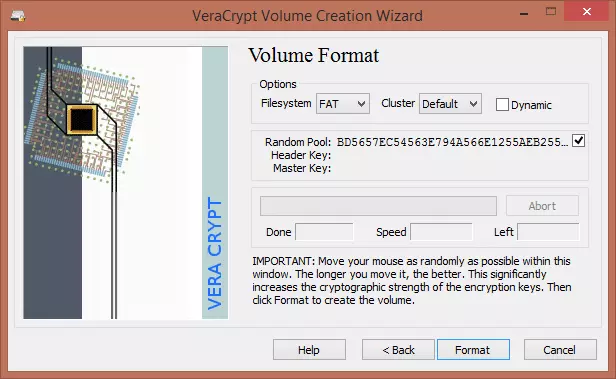
You have now created a VeraCrypt volume (file container)! Yay!
Mounting and using a VeraCrypt volume
1. Select a drive letter from the list on the VeraCrypt main screen. Then click ‘Select File’ and navigate to where you saved the VeraCrypt volume you just created, and ‘Open’. Once done, click ‘Mount’.
Any spare letter will do, so we’ll choose ‘J’. This will now be the drive letter assigned to our encrypted volume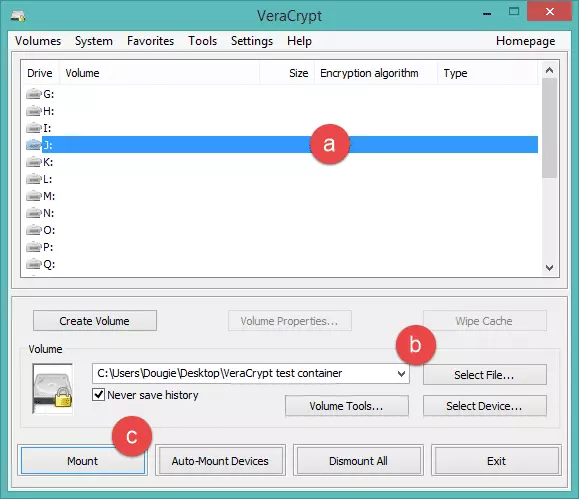
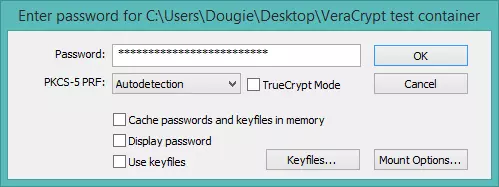
2. You will be asked for the password you specified earlier.
3. The volume is now mounted and will behave in all ways like a normal volume, except that all data on it is encrypted. You can open it by double-clicking on the volume name from the VeraCrypt main screen…
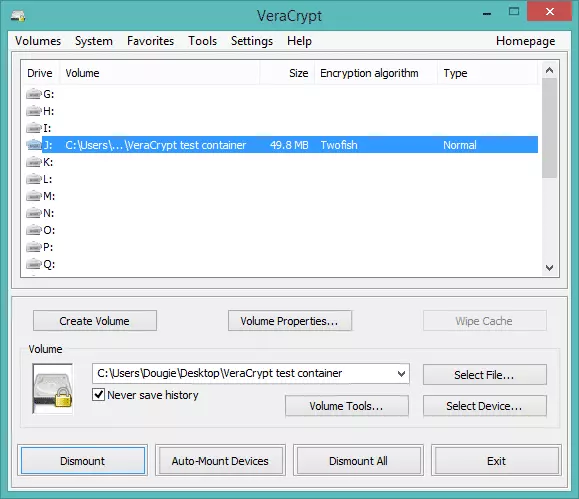
… or it can be accessed as regular volume in Explorer.
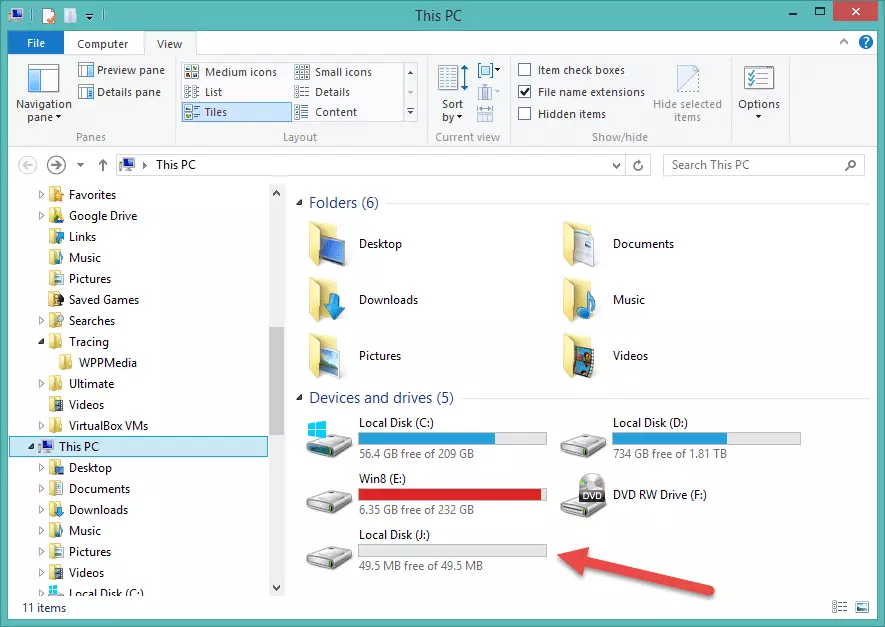
As you can see, the basics of setting up a simple encrypted volume are quite easy, and VeraCrypt does a good job at holding your hand. To see how to setup a hidden volume, check out Part 2 of this guide.
Handy tip
If you use Dropbox and are worried about Dropbox being able to see your files, you can create an encrypted VeraCrypt container inside your Dropbox folder. In this way, all files placed in the mounted container will be encrypted before being uploaded to Dropbox, and decrypted locally for viewing.
Of course, this does not make sharing and collaborating on files easy, but it does secure them against prying eyes. Android users are also in luck, as the EDS (full) app allows you to browse and open VeraCrypt encrypted volumes when on the move (the free EDS Lite is compatible with TrueCrypt containers.)
Other TrueCrypt forks
The main rival to VeraCrypt is Ciphershed, which is also a fork based off the original TrueCrypt code. Unlike VeraCrypt, Ciphershed is fully compatible with legacy TrueCrypt containers, but is generally considered not as secure.
‘As the author of VeraCrypt, I can say that the main difference with CipherShed is related to security:
- Since 2013, we choose to enhance the key derivation because the TrueCrypt approach doesn't offer the same security as in 2004 when it was released. This explains why TrueCrypt containers can't be supported anymore in VeraCrypt (a conversion tool is planned).
- In the latest version, we corrected most of the security issues discovered by the Open Crypto Audit project. In the next version, we'll correct the security issue in the bootloader.
I understand CipherShed decision to stick with TrueCrypt format but this makes it difficult for them to enhance the security of the key derivation. Nevertheless, they can benefit from all the security fixes we have implemented so far (lack of time makes it difficult from me to contribute to CipherShed but since the two projects share the same code base, reporting the modifications from one project to another is feasible).’
Some users prefer to stick with the last known ‘safe’ version of TrueCrypt (7.1a), but as this contains known (if not critical) weaknesses we recommend using VeraCrypt instead (or Ciphershed if backwards compatibility is important).
For those still wary of anything to do with TrueCrypt (a quite understandable position in our view, regardless of the audit results) we have an article on 6 best open source alternatives to TrueCrypt.
