While existing VPNs come with a multitude of subscription choices, most of them – or the fast, reliable ones at least – are only available with a monthly purchase. In this guide, we show you how to create a VPN on Amazon web services, so you can avoid those monthly subscription costs.
AWS Requirements
Amazon Web Services provides two different VPN server options: OpenVPN and SSH Tunneling. Each option has its ups and downs, and both are worth extensively researching before making a decision. Regardless of whether you choose OpenVPN or SSH Tunneling, you will still need to meet the following requirements:
- An account with Amazon Web Services
- A credit card to register for Amazon Web Services (with no charge unless you go over the preset amounts)
- PuTTy (SSH client)
- PuTTyGen (key generator)
- WinSCP (FTP server)
How to set up Amazon VPN on AWS
Setting up your VPN on Amazon Web Services is pretty straightforward. For Windows users, you’ll need to complete the following steps after registering for an account and setting up your billing information.
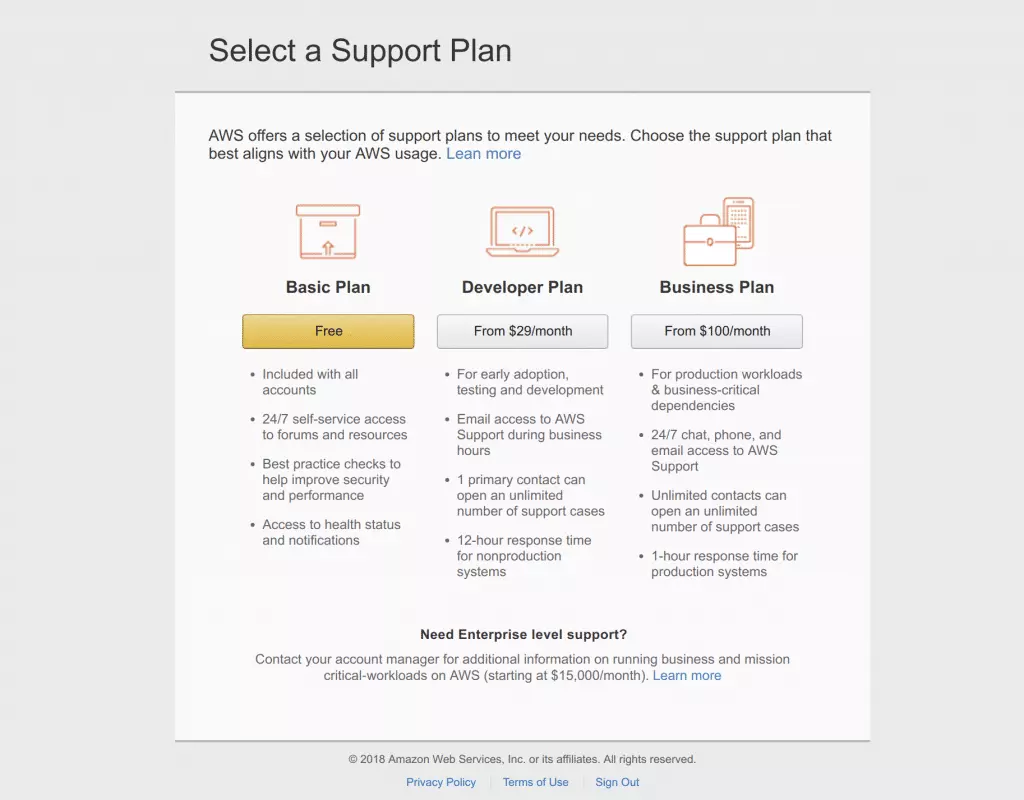
- When prompted, choose the Free Basic Plan
![1 basic plan select 1 basic plan select]()
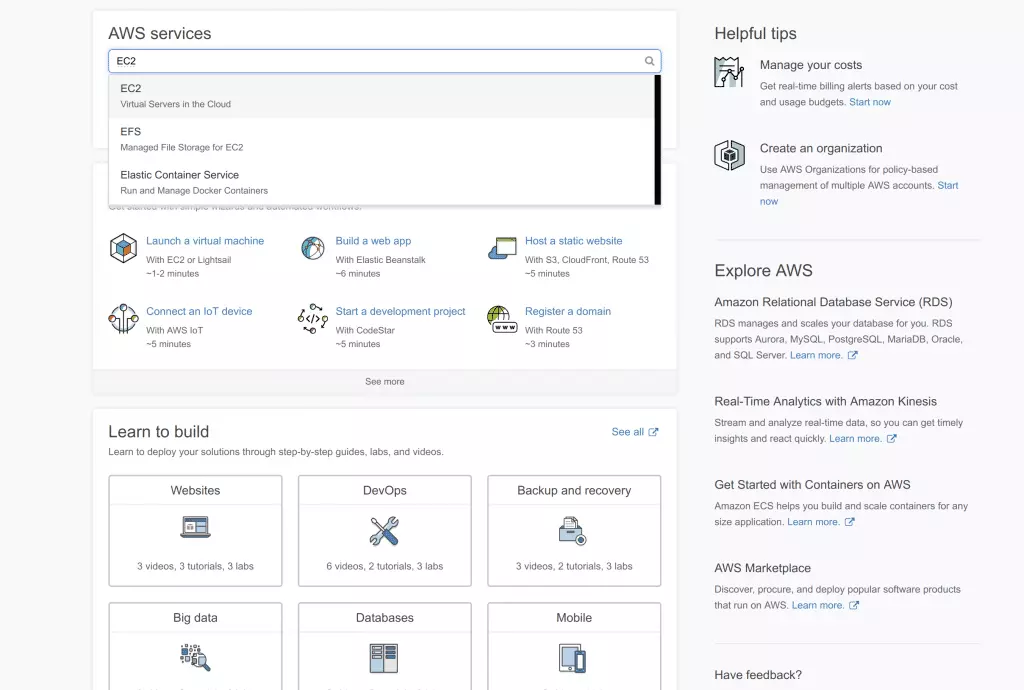
- In the search bar, type and click on EC2
![2 EC2 search bar 2 EC2 search bar]()
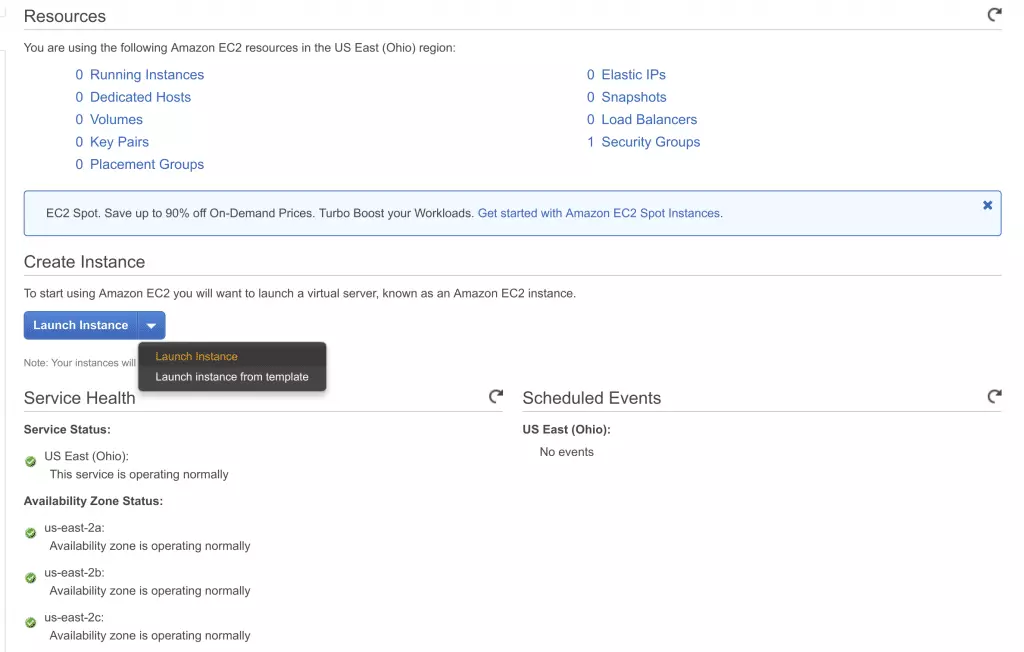
- From the EC2 dashboard, select Launch Instance
![3 AWS EC2 dashboard 3 AWS EC2 dashboard]()
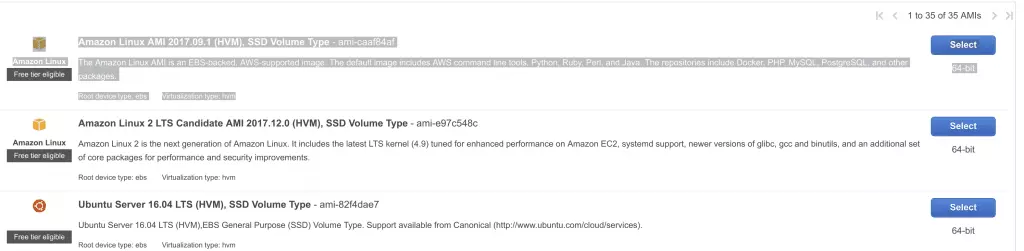
- Select the first free tier eligible option: Amazon Linux AMI
![4 Amazon Linux AMI 4 Amazon Linux AMI]()
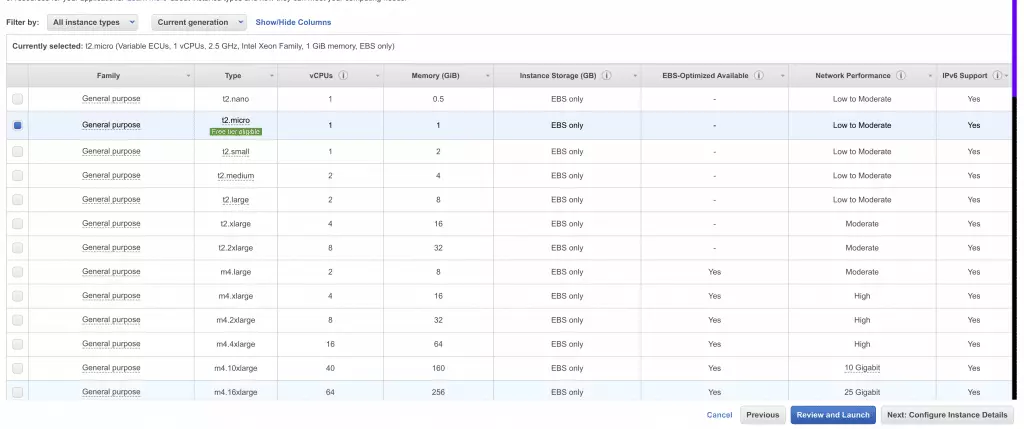
- Choose the free tier eligible t2.micro option (usually pre-selected)
![5 t2.micro selection 5 t2.micro selection]()
- Select Review and Launch at the bottom of the page
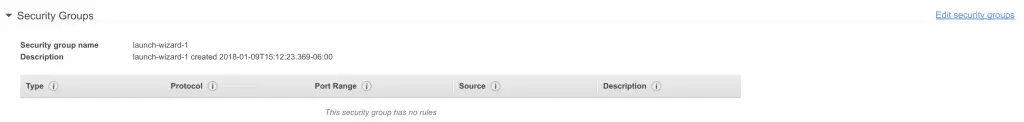
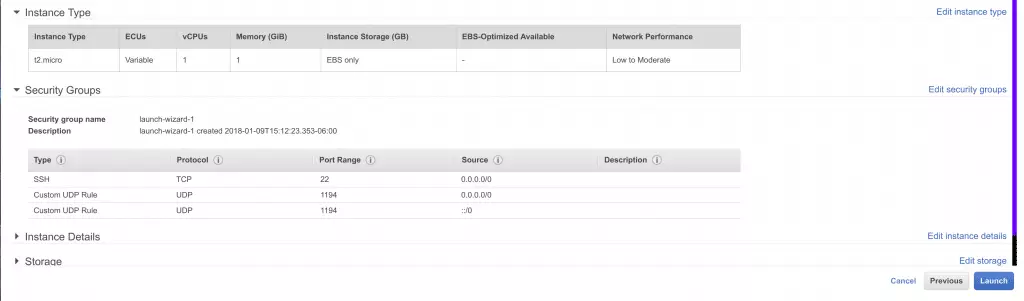
- Click on Edit security groups
![6 edit AWS security groups 6 edit AWS security groups]()
- Click on Add Rule
![7 add new rule 7 add new rule]()
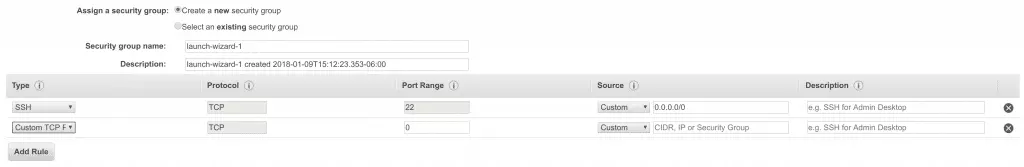
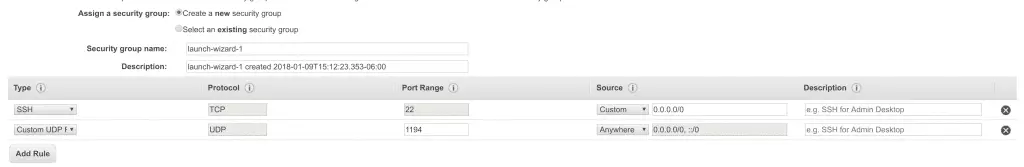
- Under the dropdown menu for Type, select Custom UDP
![8 change to UDP and port 8 change to UDP and port]()
- Set the Port Range to 1194
- Under Source, select Anywhere
- Select Launch
![9 Click on AWS Launch 9 Click on AWS Launch]()
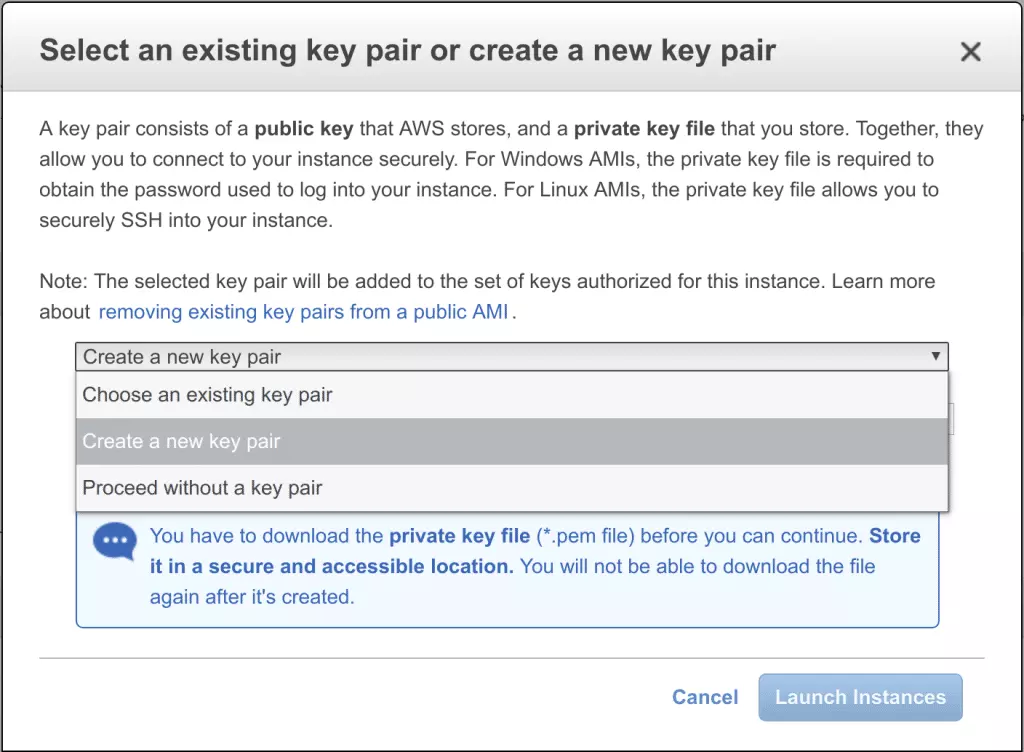
- When prompted, select the drop-down menu and choose Create a new key pair
![10 create a new key pair 10 create a new key pair]()
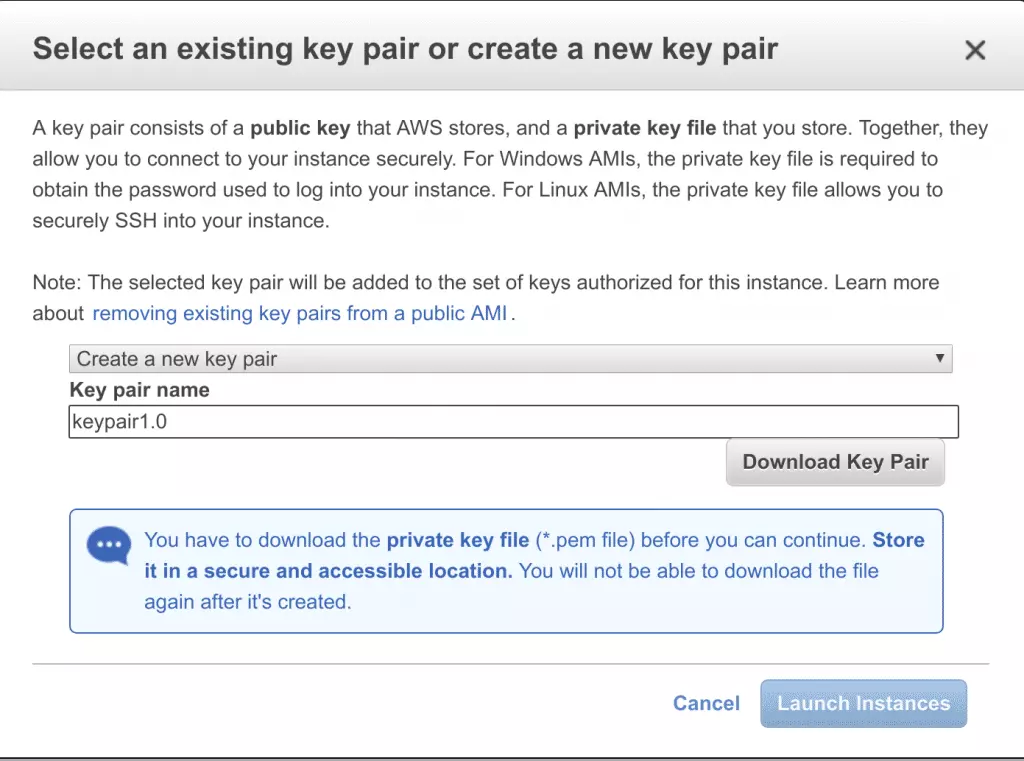
- Name your key pair
![11 name your new key pair 11 name your new key pair]()
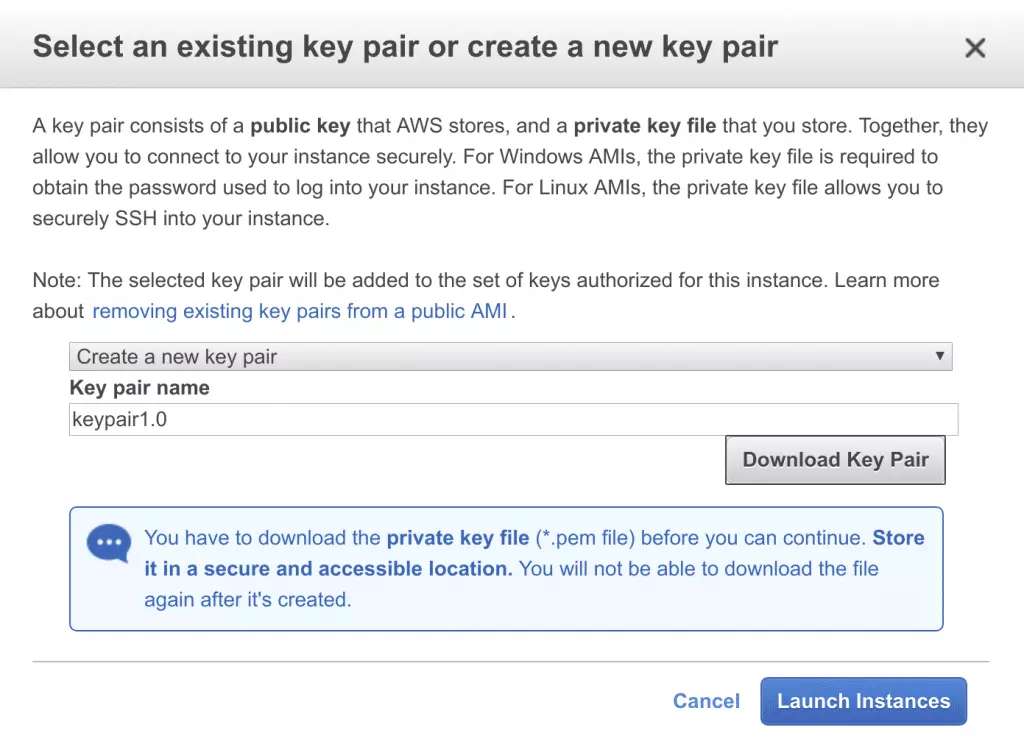
- Select Download Key Pair and store it somewhere safe
![12 download your key pair and launch 12 download your key pair and launch]()
- Select Launch Instances
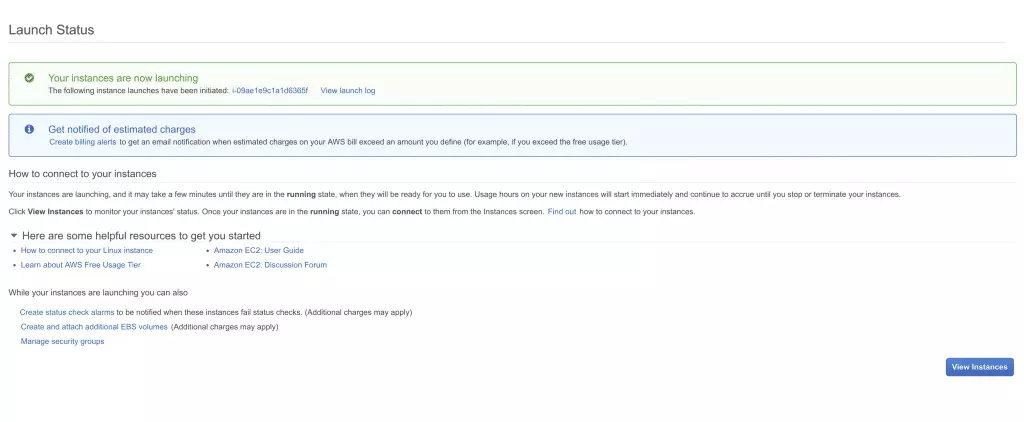
- On the Launch Status screen, select View Instances
![13 click on view instances 13 click on view instances]()
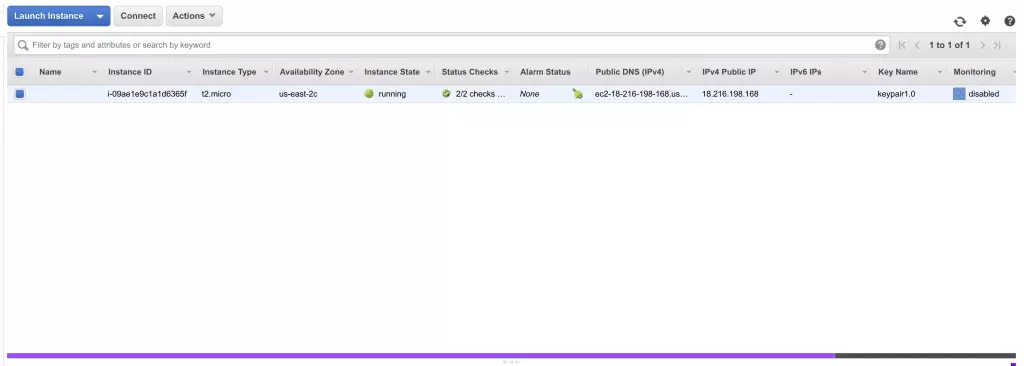
- Verify that only one instance is launched (if this is your first time using EC2)
![14 view instances 14 view instances]()
How to Use your Amazon VPN with SSH Tunneling
Many people use VPNs in the hopes of accessing geographically restricted content. If your sole reason for wanting to use a VPN is to access content that’s not available in your country, SSH tunneling is probably your best and easiest option. While SSH tunneling isn’t perfect, it is great for lightweight use such as basic web browsing or weaseling your way around geographically locked websites/services.
To set up SSH tunneling, complete the following steps:
- Download the PuTTy and PuTTyGen .exe files
- Double click on PuTTyGen to open it
- Select Load
- On the dropdown menu in the lower right corner, select All File Types
- Choose your key pair file from earlier
- Select Save Private Key
- Your file name must match your .pem key verbatim
- OPTIONAL: create a passphrase
- Exit out of PuTTyGen and open PuTTy
- Navigate to your AWS EC2 Dashboard
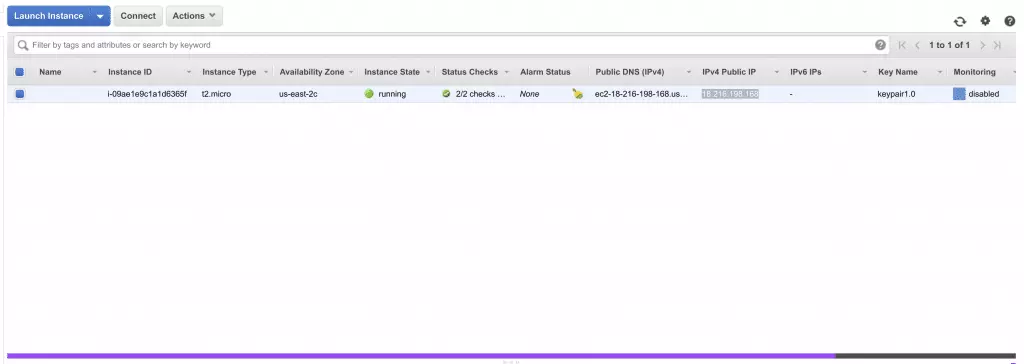
- Copy your IPv4 Public IP
![IP address for AWS IP address for AWS]()
- Paste your IPv4 Public IP into PuTTy’s Host Name (or IP address)
- Choose a Session Name
- Select Save
- In the left panel, navigate to SSH>Auth
- Under Authentication parameters, select Browse
- Navigate to the private key you generated earlier and select it
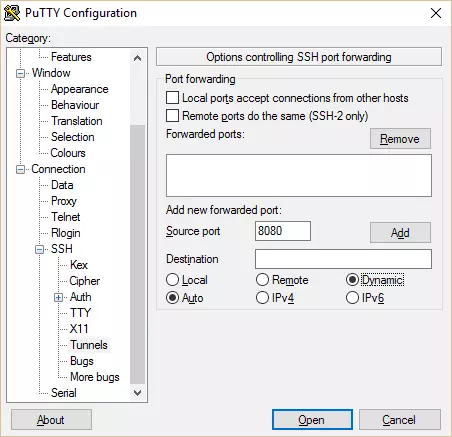
- In the left panel, navigate to SSH>Tunnels
- Under Add new forwarded port: type in 8080 & select Dynamic and Auto
![PuTTy configuration PuTTy configuration]()
- Navigate back to Session & select Save
- Select Open
- When prompted for a username, type ec2-user for Amazon Linux AMI
- Proceed to the next steps based on your preferred browser
Firefox
- Open Firefox
- Navigate to Tools>Options>Advanced>Network>Connection>Settings>Manual proxy configuration
- Set the SOCKS Host to 127.0.0.1
- Set the Port to 8080
- Hit Save
Chrome
- Install the Proxy SwitchySharp extension
![Chrome Store Web Page Chrome Store Web Page]()
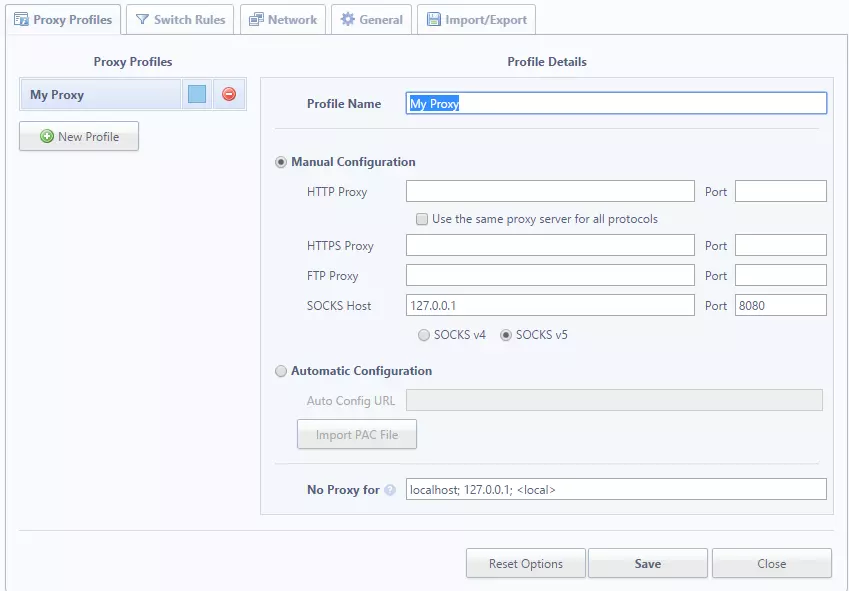
- A setup screen will pop up
![google chrome extension google chrome extension]()
- Choose a name
- Select Manual Configuration
- Change the SOCKS Host to 127.0.0.1
- Change the Port to 8080
- Everything else should be left blank
- Select Save
- Click the extension icon and select your proxy profile
After completing the above steps, you’ll be successfully tunneling your browser’s traffic through your EC2 instance. That said, SSH tunneling is only useful for lightweight browsing and accessing some geographically restricted content. If your intent is to create a fully functioning VPN with the ability to reroute all internet traffic, OpenVPN is the option you’ll want to look into. We go into detail below.
How to Use AWS with OpenVPN
As an open source application, OpenVPN is a great VPN tool to use. With the ability to reroute all of your internet traffic through your EC2 instance, OpenVPN is also able to assist in VPN usage for applications like Steam or Battle.net. OpenVPN setup might seem complex when drifting your eyes over the instructions, but the truth is that it’s fairly simple (if not a bit time consuming).
Installing OpenVPN On AWS
- Using the instructions above, connect your EC2 instance to PuTTy
- A command prompt displaying Amazon Linux AMI should pop up
- Copy & paste the following commands individually into your command prompt:
- sudo yum install -y openvpn
- sudo modprobe iptable_nat
- echo 1 | sudo tee /proc/sys/net/ipv4/ip_forward
- sudo iptables -t nat -A POSTROUTING -s 10.4.0.1/2 -o eth0 -j MASQUERADE
- sudo iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
- If the first command listed above doesn’t work, replace it with:
- sudo apt-get install -y openvpn
Connecting to OpenVPN via easy-rsa
When it comes to setting up your OpenVPN server, you have a couple of different methods. The first one allows you to connect to various devices simultaneously via easy-rsa, while the second method only allows one connection at a time via static encryption.
Server Configuration
- Copy & paste the following commands individually into your command prompt:
- sudo yum install easy-rsa -y --enablerepo=epel
- sudo cp -via /usr/share/easy-rsa/2.0 CA
- Enable root user by typing into your command prompt sudo su
- In the next step, you will be asked to fill in information like your occupation/company – select the default by hitting Enter when prompted
- Copy & paste the following commands individually into your command prompt:
- cd /usr/share/easy-rsa/2.0/CA
- source ./vars
- ./clean-all
- ./build-ca
- ./build-key-server server
- ./build-dh 2048
- To set up your device, copy & paste the following commands individually in your command prompt:
- ./build-key client
- cd /usr/share/easy-rsa/2.0/CA/keys
- openvpn --genkey --secret pfs.key
- mkdir /etc/openvpn/keys
- for file in server.crt server.key ca.crt dh2048.pem pfs.key; do cp $file /etc/openvpn/keys/; done
- cd /etc/openvpn
- nano server.conf
- Nano text editor will open – copy & paste the following text:
port 1194
proto udp
dev tun
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
key /etc/openvpn/keys/server.key # This file should be kept secret
dh /etc/openvpn/keys/dh2048.pem
cipher AES-256-CBC
auth SHA512
server 10.8.0.0 255.255.255.0
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
ifconfig-pool-persist ipp.txt
keepalive 10 120
comp-lzo
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 3
tls-server
tls-auth /etc/openvpn/keys/pfs.key
- To save and exit the config text, hit CTRL+O followed by CTRL+X
- Start OpenVPN by typing into your command prompt:
- sudo service openvpn start
Client Configuration
- Copy & paste the following commands into your command prompt:
- cd /usr/share/easy-rsa/2.0/CA
- chmod 777 keys
- cd keys
- for file in client.crt client.key ca.crt dh2048.pem pfs.key ca.key; do sudo chmod 777 $file; done
- Download WinSCP with default installation options & open it
- WinSCP will prompt you to import your server authentication details from PuTTy
- Select the one you created in earlier steps
- Select Edit and type in under username: ec2-user
- Hit Login
- Click on Edit & then Advanced
- Navigate to SSH>Authentication>Private key file
- Find your PPK file
- Back on the main screen, enter your EC2 instance IPv4 address in the Host Name field
- Save your settings
- In the right panel, navigate to the directory that holds your key files
- You’ll need to highlight the five necessary files: client.crt, client.key, ca.crt, dh2048.pem, and pfs.key
- Select the green Download button
- Save the files wherever you want
- Navigate back to the PuTTy Command Prompt
- Copy & paste the following command:
- for file in client.crt client.key ca.crt dh2048.pem pfs.key; do sudo chmod 600 $file; done
- cd ..
- chmod 600 keys
- On your PC, move the five files into your OpenVPN configuration folder (default location is C:\\Program Files\\OpenVPN\\config
SUB: Creating the Client Configuration File
The last thing we need to do is create the client configuration file. Luckily, this is easily done using your basic text editor.
- Right-click on any basic plaintext editor
- Select Run as administrator
- Copy & paste the following configuration:
client
dev tun
proto udp
remote YOUR.EC2.INSTANCE.IP 1194
ca ca.crt
cert client.crt
key client.key
tls-version-min 1.2
tls-cipher TLS-ECDHE-RSA-WITH-AES-128-GCM-SHA256:TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256:TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA256
cipher AES-256-CBC
auth SHA512
resolv-retry infinite
auth-retry none
nobind
persist-key
persist-tun
ns-cert-type server
comp-lzo
verb 3
tls-client
tls-auth pfs.key
- Save the config as client.ovpn
- Save the config file in the same directory as your other five files (Default is C:\\Program Files\\OpenVPN\\config)
- Finally, right click on the OpenVPN GUI and select Run as administrator
- In your system tray below, right click on the OpenVPN icon
- Connect to the appropriate configuration
- If successful, the OpenVPN icon will turn green
Removing the Certificate Authority File
In order to remain as secure as possible, our team at ProPrivacy.com recommends removing the ca.key file from your server. On the off chance that the certificate authority is compromised, you will never want to trust certificates provided by that CA in the future. Before completing the following steps, however, be sure that you have the keys/certificates for every device you want to connect.
- Select ca.key
- Instead of selecting the Download button, select Download and Delete
- Store the file in a safe location
Fixing Reboot or Maintenance Problems
If you experience problems after rebooting your PC or completing maintenance, you can set up OpenVPN as a service by typing the following commands in your command prompt. Most times, this fixes the issue.
- sudo systemctl start [email protected]
- sudo systemctl enable [email protected]
If the above commands don’t work or you seem to connect to the VPN but not the internet, try resetting your iptable settings by running the commands from earlier:
- echo 1 | sudo tee /proc/sys/net/ipv4/ip_forward
- sudo iptables -t nat -A POSTROUTING -s 10.4.0.1/2 -o eth0 -j MASQUERADE
- sudo iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
Connecting to OpenVPN via Static Encryption
While this method is easier to achieve than the easy-rsa method, it is less secure and only allows one connection to the VPN server at a time. Still, it’s a great option over other free VPN services.
- In the PuTTy Command Prompt, paste:
- cd /etc/openvpn
- sudo openvpn --genkey --secret ovpn.key
- sudo nano openvpn.conf
- When the Nano text editor pops up, type the following configuration:
port 1194
proto tcp-server
dev tun1
ifconfig 10.4.0.1 10.4.0.2
status server-tcp.log
verb 3
secret ovpn.key
- Select CTRL+O to save followed by CTRL+X to exit
- In the PuTTy Command Prompt, type:
- sudo service openvpn start
- sudo chmod 777 ovpn.key
- Download WinSCP by following default installation prompts
- A prompt will ask you to import your server authentication details from PuTTy
- Select the one you made in earlier steps and click Edit
- Under username, type in ec2-user and hit Login
- In the right panel, scroll up and navigate to etc/openvpn
- Select the ovpn.key file and drag it into a secure location
- In the PuTTy Command Prompt, type:
- sudo chmod 600 ovpn.key
- Download OpenVPN according to your system specifics
- Move your ovpn.key into OpenVPN’s configuration folder (Default is C:/Program Files/OpenVPN/config…)
- Open Notepad and paste the following:
proto tcp-client
remote yourEC2IPhere
port 1194
dev tun
secret "your pathway to OpenVPN config folder – see default above"
redirect-gateway def1
ifconfig 10.4.0.2 10.4.0.1
- Save the file in your OpvenVPN config folder as myconfig.ovpn
- In your system tray, make sure OpenVPN isn’t running – close it if it is
- On your desktop, right click on OpenVPN and select Run as administrator
- Back in your system tray, right click on OpenVPN and select Connect
- If successful, the icon will turn green
Testing Your AWS VPN is Working
Verifying your success with Amazon Web Services VPN is extremely easy!
- Disconnect from your VPN
- Navigate to a website like www.ipchicken.com
- Jot down your IP address
- Exit out of the browser
- Reconnect to your VPN
- Open your browser and navigate back to www.ipchicken.com
- Compare your IP address from step 3 to the one displayed now
- If the IP addresses are different, you’re successfully using your homemade VPN!
Create your own VPN server on Linux
If you are a Linux user and you want to create your own VPN, check out our how to set up a VPN server on Linux guide. We list the steps you need to take in order to create your own Linux VPN server.
Using Amazon Web Services to Create a VPN: A Summary
If you want the benefits of using a VPN without the monthly subscription fees, creating an Amazon VPN is a great option. Creating your own Amazon Web Service VPN is straightforward and easy – and despite being somewhat time consuming – it’s also completely worth it.