There has been some controversy of late over a recent update that quietly added 17 new root certificates to Windows (and removed 1) without alerting users to the fact, leading some to call the entire system ‘broken’.
We therefore thought it a good time to explain what root certificates are, and whether readers should be worried…
What is a root certificate?
When you visit a website, how do you know that it is the website you think you are visiting? The internet’s answer to this problem is SSL certificates (also known as HTTPS certificates).
When you visit an SSL secured website (https://), in addition to the connection being secured using SSL/TSL encryption, the website will present your browser with an SSL certificate showing that it (or more accurately ownership of the website’s public key) has been authenticated by a recognized Certificate Authority (CA). There are some 1200 such CAs in existence.
If a browser is presented with a valid certificate then it will assume a website is genuine, initiate a secure connection, and display a locked padlock in its URL bar to alert users that it considers the website genuine and secure.
This system, which is the cornerstone of security on the internet, and is used just about every secure website that handles sensitive information (including banks, webmail services, payment processors and so on,) therefore relies on trusting the CAs.
Certificate Authorities issue certificates based on a chain of trust, issuing multiple certificates in the form of a tree structure to less authoritative CAs. A root Certificate Authority is therefore the trust anchor upon which trust in all less authoritative CAs are based. A root certificate is used to authenticate a root Certificate Authority.
So who issues the root certificates?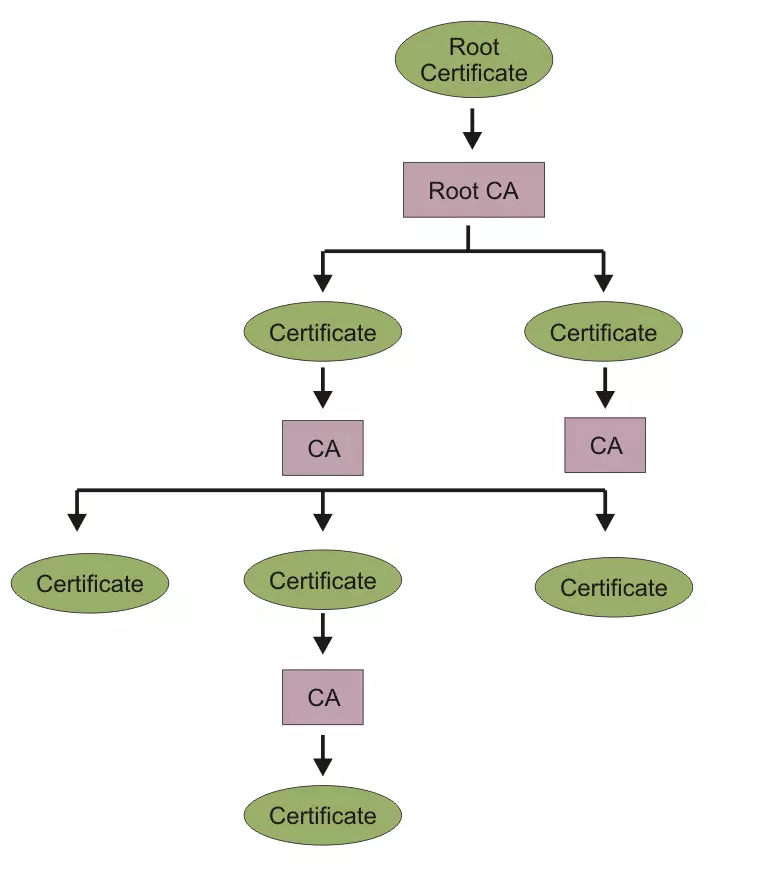
Generally speaking, root certificates are distributed by OS developers such as Microsoft and Apple. Most third party apps and browsers (such as Chrome) use the system’s root certificates, but some developers use their own, most notably Mozilla (Firefox), Adobe, Opera, and Oracle, which are used by their products.
Problems with the CA system
The whole CA system therefore relies on trust, so how do you know these certificates can be trusted? Well, at the end of day you have to trust someone, and if you trust the developers of the software you use, then you sort of have to trust their certs.
At least that is the theory. As a recent Google warning over fake SSL certificates demonstrates, just one ‘rogue’ CA issuing unreliable certificates can cause havoc , and unfortunately Certificate Authorities can (and have been known to) issue fake certificates . The usual culprit for this is unscrupulous Governments putting pressure on CA companies, but criminals can also strong-arm CAs, and hackers can compromise their systems.
The Electronic Frontier Foundation (EFF) did start an SSL Observatory project with the aim of investigating all certificates used to secure the internet, inviting the public to send it certificates for analysis. As far as we are aware, however, this project never really got off the ground, and has lain dormant for years.
So why all the fuss about Microsoft ‘sneakily’ adding root certificates?
Some commentators have got themselves into a tizz over Microsoft adding new root certificates without alerting users or asking their permission. We have to note, however, that the vast majority of users (including us) have no reliable way to determine whether a given a root Certificate Authority is trustworthy or not, which makes this whole dispute rather pointless in our view…
If you do not trust Microsoft, then do not use Windows. Of course, if you are serious about security then you really should not trust Microsoft anyway, and it is very likely that some of the root certificates already shipped with Windows allow the NSA to perform MitM attacks on your computer should they so choose. These could in theory direct you to bogus websites that look genuine to your browser thanks to fake SSL certificates.
Those serious about security should use Linux (and preferably a hardened distro at that). It should also be stressed that no mobile OS can be considered in the slightest bit secure.
For what it’s worth, the list of new Certificate Authorities recently added to the Microsoft Certificate Trust List looks pretty harmless to us (many are simply upgrades to older certificates,) but who knows?
How to remove a root certificate
If you really do not like a particular root Certificate Authority, then you can remove its root certificate. Be warned that doing so makes all certificates that are issued by that Certificate Authority untrusted, as well as all those of any of the ‘lesser’ CAs it has authorised. Removing these can have a very negative impact on your internet experience.
In the wake of the recent Google fake certificates fiasco, some people recommend removing Chinese CA’s. We stress, however, that doing so is entirely at your own risk.
Windows
We are using Windows 8.1, but the process should be pretty much the same on all versions of Windows.
1. Right-click Internet Explorer icon -> Run as administrator
2. Go to Tools (gear icon on top right) -> Internet Options -> Content tab -> Certificates -> Trusted Root Certification Authorities
3. Select the certificate you wish to remove, and hit ‘Remove’. Note that it is probably a very good idea to ‘Export’ a certificate for backup first so that you can ‘Restore’ it again later if needed.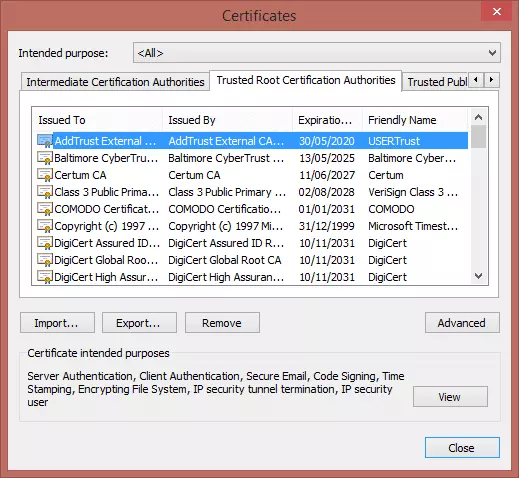
Firefox (desktop versions only)
1. Open Firefox and go to Open Menu -> Options -> Advanced -> Certificates -> View Certificates
2. In the Certificates Manager window, click on the ‘Authorities’ tab, and you will see the list of authorized root CAs, together with the certificate(s) they have authorized below them
3. Click on a certificate that you don’t like, and hit ‘Delete or Distrust’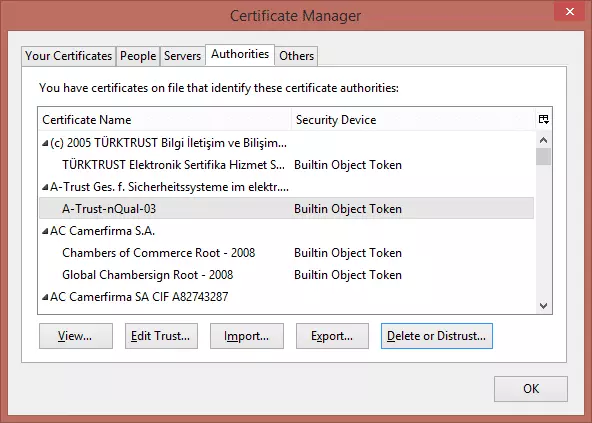
Hit OK if you are sure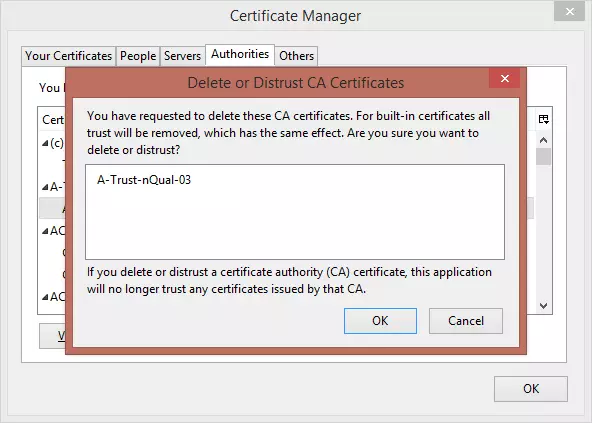
To completely remove a given root CA, you must ‘Delete or Distrust’ all certificates it has authorized. As with removing Windows root certificates, we strongly advise backing up removed certificates first.
Mac OSX
I am not a Mac user, but as I understand it Apple does not allow users to remove root certificates, even when using root privileges. Non-root certificates can be removed using Keychain Access.
Android (5.1 Lollipop, but similar on all versions)
1. Go to Settings -> Security -> Trusted Credentials -> System tab. Touch the green tick next to the certificate you don’t like
2. Scroll down through certificate details to the bottom, and select ‘Disable’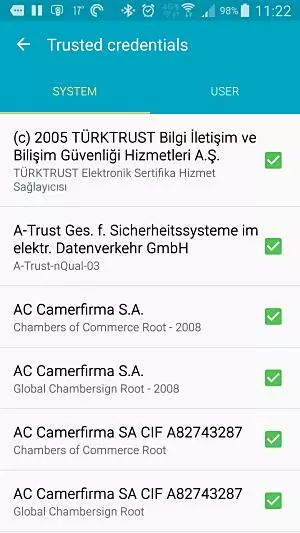
iOS
Root certificates cannot be removed in iOS (personal certificates can be removed using the iPhone Configuration Utility).
Ubuntu (will be similar for most versions of Linux)
The simplest way to deselect CA’s is to open Terminal and run:
sudo dpkg-reconfigure ca-certificates
Press space to deselect a certificate.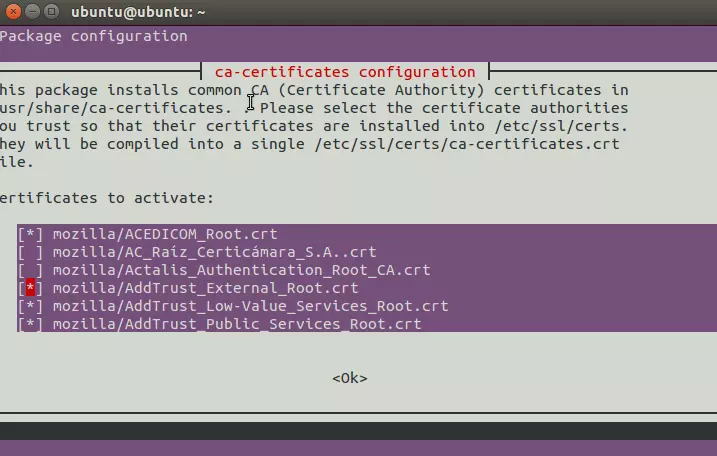
The list of CAs is stored in the file /etc/ca-certificates.conf. This can be edited manually by entering:
nano /etc/ca-certificates.conf
If you edit this file manually then you need to run the following command to update the actual certificates in /etc/ssl/certs/: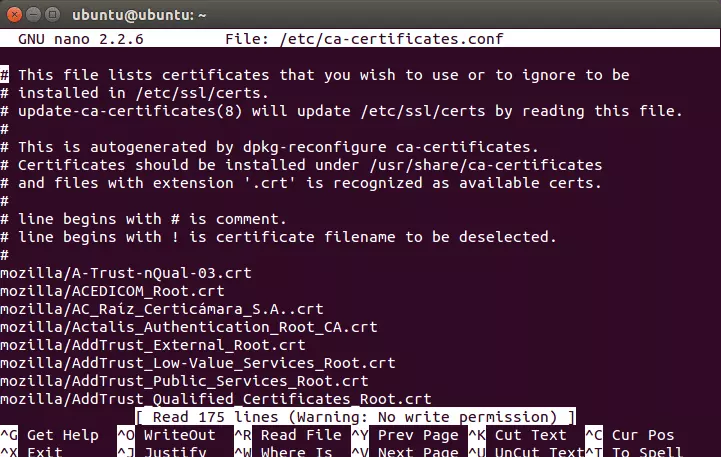
sudo update-ca-certificates
(If you use dpkg-reconfigure this is done automatically).
