Commercial VPN services are handy and convenient, bundling a privacy service into an accessible application-based package. Unfortunately, these providers can be expensive and don’t always offer servers in countries you wish to connect to. With our step-by-step guide, you can set up your own Virtual Private Server (VPS) based in a territory of your choosing, creating your own closed environment that behaves like a remotely located physical server.
While this does require some technical understanding, we have broken things down into digestible steps to help novices navigate the process with a little more confidence. Once you are comfortable with the basics, there is more to learn about OpenVPN servers here.
How to build your own VPN server
What you will need
-
A VPS server with CentOS 6 (32- or 64-bit) installed, and a minimum of 218MB RAM. We may review suitable VPS services in the future, but for this tutorial, we have chosen VPSCheap.net - mainly because it offers VPS plans from $1.99 per month. If you want a more rounded approach, take a look at these comprehensive tips on selecting a VPS hosting provider.
-
An SSH client - macOS and Linux users have one already, in the form of Terminal. Windows users can download the excellent PuTTy (which we use for this tutorial).
Installing OpenVPN Access Server on the VPS
-
Open your SSH client and connect to your VPS server using the IP address supplied by your VPS provider.
![PuTTY Configuration]()
Terminal users should enter
ssh -l user ip.address
and enter details when they get the response:
ip.address/
/username/
-
Login as root and enter the password you were given by your VPS provider. Note that in PuTTy the typed password remains hidden, so just type it and hit <enter>.
![Root server login]()
-
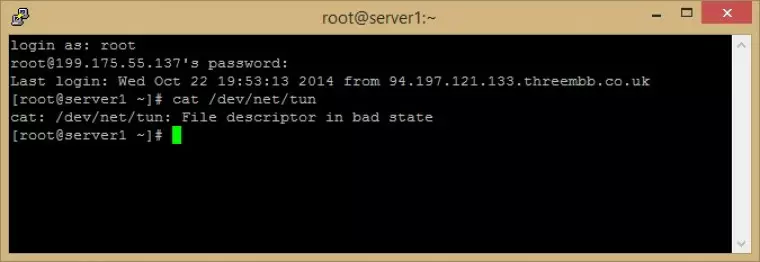
Before proceeding you should check that tap/tun is enabled. Enter (in PuTTY you can paste by right-clicking):
cat /dev/net/tun
If tap/tun is enabled, you should receive the response:
cat: /dev/net/tun: File descriptor in bad state.
Any other response means tap/tun is not enabled. We had to login to our VPS account control panel to enable it.
![login as root]()
-
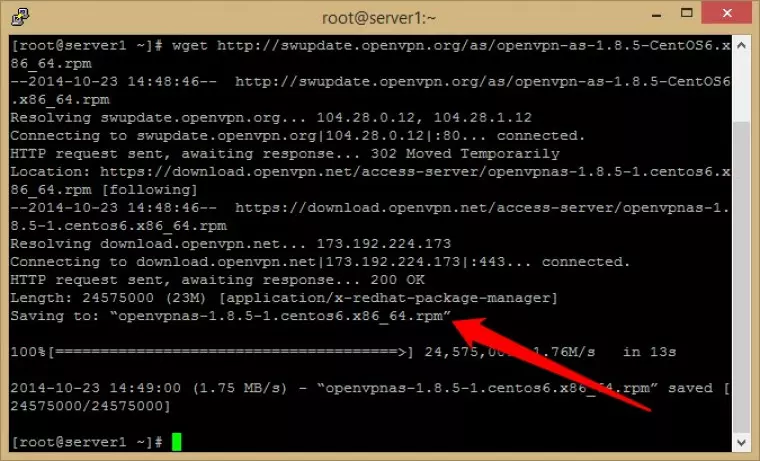
We need to download the OpenVPN Server Access package. Enter:
wget http://swupdate.openvpn.org/as/openvpn-as-1.8.5-CentOS6.i386.rpm (CentOS 6 32-bit)
or
wget http://swupdate.openvpn.org/as/openvpn-as-1.8.5-CentOS6.x86_64.rpm (CentOS 6 32-bit)
![Downloading OpenVPN server access package]()
-
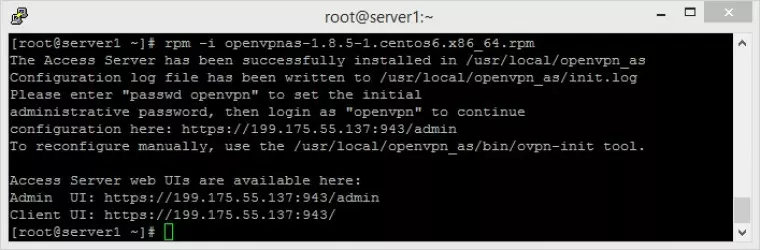
We now need to install the package using the rpm command. Check the line that says ‘Saving to’ (see arrow in above screenshot) to verify package name and enter rpm -i [package name], such as:
rpm -i openvpnas-1.8.5-1.centos6 x86_64.rpm
![install package using rpm command]()
The output should look as shown above. Make a note of the Admin UI address and Client UI addresses - you will need them in a minute!
Update 02/20: The instructions for installing OpenVPN Access Server have changed since this article was first written. The following should work, but we have not had the opportunity to test it yet:
Replace steps 4 and 5 the following commands:
yum -y install https://as-repository.openvpn.net/as-repo-centos6.rpm
yum -y install openvpn-as
Make a note of the Admin UI address and Client UI addresses - you will need them in a minute!
-
Setup a password. In PuTTy, enter password openvpn, and enter whatever password you want at the prompt (and again to confirm it).
![In PuTTY enter password]()
Oops - our password is not very strong, but it will do for the purposes of this example!
-
Paste the Admin UI address into your web browser (see step 5 above), and enter Username: ‘openvpn’ and whatever password you selected above into the Admin Login (you may need to ‘Agree to end User License Agreement’ the first time you log in).
>
![openvpn login]()
You should now see the OpenVPN Access Server configuration page.
![openvpn access server is configured]()
Congratulations, you have installed OpenVPN Access Server on your VPS!
Connect to your VPS using OpenVPN Connect
We now need to set up OpenVPN at your end. OpenVPN Connect is a VPN client that creates a simple OpenVPN connection between your PC and the VPS server, without the need for certificate authentication.
By default, the connection is protected by 128-bit Blowfish Cipher-Block Chaining (BF-CBC) encryption. The Blowfish cipher was created by Bruce Schneier, who has since recommended switching to stronger standards such as AES. However, for most purposes it is fine (and in part two of this tutorial we show you how to change encryption ciphers).
-
Paste the Client UI address into your web browser (from step 5 above), ensure ‘Connect’ is selected in the drop-down menu, and enter your Username: ‘openvpn’ and password.
![openvpn client login]()
-
You will be prompted to download OpenVPN Connect client.
![openvpn client login 2]()
-
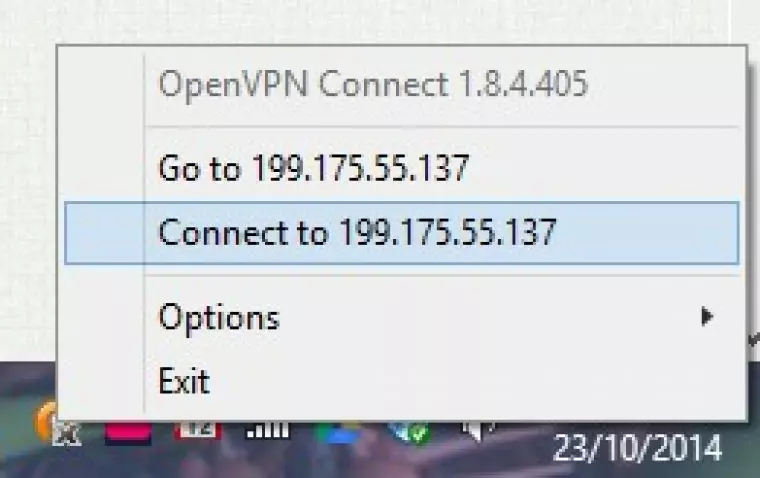
Install and run OpenVPN Connect as normal, then click the OpenVPN connect icon in the notification bar and select 'Connect to (your client UI address).
![install and run openVPN]()
-
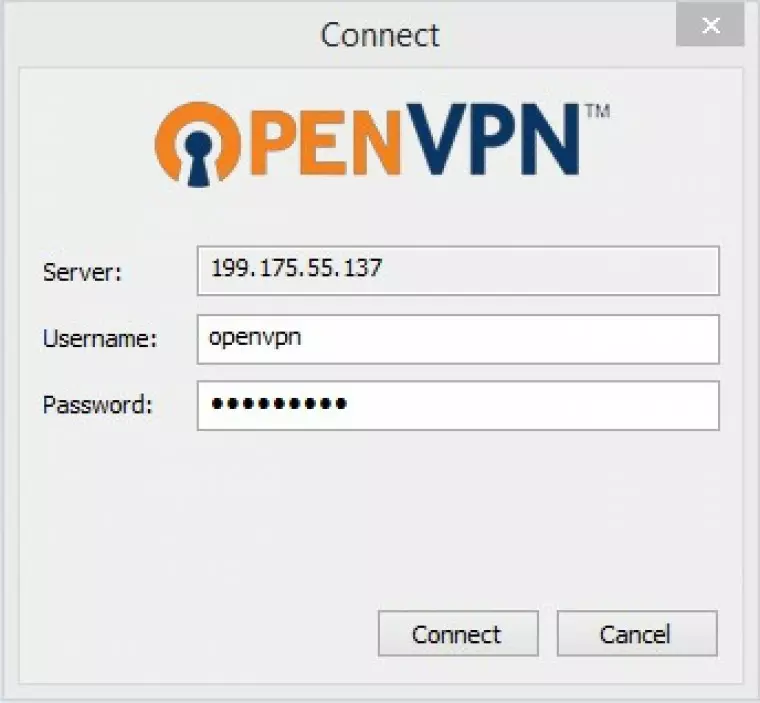
Enter username (openvpn) and password.
![openvpn username and password]()
-
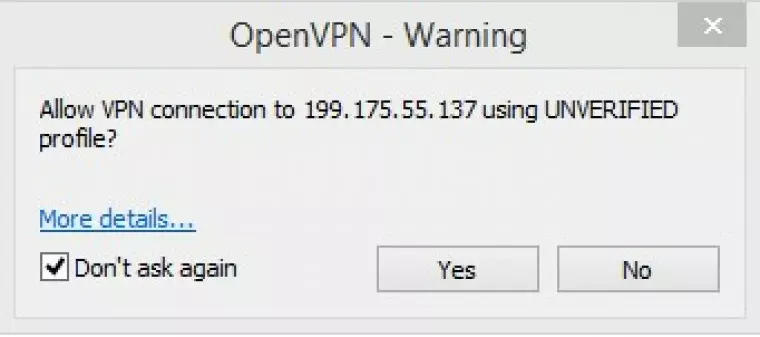
Click ‘Yes’ at the warning (you need do this only once).
![openVPN warning]()
-
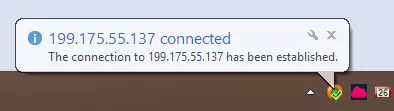
You are now connected to you your VPS via OpenVPN.
![openvpn connect 4]()
The OpenVPN connect icon turns green so you can see whether you are connected at a glance.
Check out our IP leak test to make sure that everything was working properly, and our IP appears to be that of our VPS.
The pros and cons of building your own VPN server
Pros
Choose your own server locations
Just locate the VPS in the country you wish to access.
Good for unblocking content
As with a regular VPN service, a private VPN server is great for great for accessing geo-restricted services.
Less likely to be blocked
The VPS provides a private IP address. This means the IP address is less likely to be blocked by streaming services which block IPs known to belong to VPN providers (as Netflix and iPlayer do). Do note, however, that these blocks sometimes also extend to all service providers.
Good for defeating censorship
A private IP address makes using your own VPN server a great anti-censorship option as repressive countries also often block IPs known to belong to VPN providers. Many people experience great success at overcoming the Great Firewall of China by setting up their own private VPN servers in countries outside China. Of course, simply using a private VPN server will not defend against other censorship measures such as Deep packet inspection (DPI).
Protects against hackers when using public WiFi hotspots
As with a regular VPN service, the fact that your data is encrypted between your device and the VPN server means that it is secure when using public WiFi. Even if you accidentally connect to an "evil twin” hotspot, the hackers will not be able to access your data.
Can be cheaper than a commercial VPN
Some VPS providers rent out server space for a very low monthly cost. That said, there are also some great but very cheap VPN services out there.
Cons
A big responsibility
VPN providers work hard to keep you and your digital data secure around the clock. When you take matters into your own hands, however, you'll ultimately be the one calling the shots when it comes to security. Expect to have to make time-sensitive decisions and run manual security updates.
Not for the technically faint hearted
Setting up your own VPN server on a VPS requires a fair amount of technical chops. We hope to make the setup process as painless as possible with these tutorials, but it does require a reasonable degree of technical know-how and will require getting your hands dirty with a command line.
Will your own VPN server be more secure?
Using a private VPN server encrypts the internet traffic between your device(s) and the VPN server. The VPN server also acts as a proxy, thus preventing your internet provider (ISP) from seeing what you get up to on the internet.
Unlike commercial VPN services, you control the VPN server. This means that you do not have to trust a third party with your data. This is the main reason that running your own VPN server is often recommended for privacy reasons. You can also choose your own VPN server locations.
Your IP is yours alone
With a VPN service, your IP address is shared by many other users, which makes it very hard to identify which of those users is responsible for which action associated with an IP address on the internet.
With a private VPN server, on the other hand, you have a static IP address that absolutely belongs to you and you only. This means there is no ambiguity about who did something on the internet using that IP address, which can be easily traced back directly to you.
A VPS is not secure
Virtual private servers are software servers running on shared physical server space. Someone else controls the hardware these virtual servers are installed on, which means that VPS’s should never be considered secure.
If presented with a warrant, for example (or even just an informal request), no server center staff are going to have any scruples against accessing the VPN logs stored on your VPS and handing them over to the police.
DNS
When you use a commercial VPN service, DNS requests are a sent through the VPN tunnel to be handled by your VPN provider (either using its own DNS servers, or leveraging a third party DNS provider but proxying the requests through its servers to protect your privacy).
When using a private VPN server this does not happen by default, and DNS requests will continue to be handled by your ISP. It is possible to set up your own DNS server on the VPS, but that is beyond the scope of this tutorial (although it is something we may tackle in the future).
A simpler option is to change your devices DNS settings to point towards a more privacy-friendly DNS provider such as OpenNIC, but this still requires trusting a third party.
For more information on what DNS is and how to change your DNS settings, please see A Complete Guide to Changing your DNS Settings.
Because of these issues, we reject the claim often made on the internet that a private VPN server is more secure and better for privacy than using a commercial VPN service. It depends somewhat on your threat model, but in many ways using a good no logs VPN service is much better for privacy than using a private VPN server.
Now we have the basics covered, please be sure to check out Part 2 of this guide, where we show you how to change the encryption cipher, build an OpenVPN certificate, create an .ovpn file, and add other users.
Create your own VPN server on Linux
If you are a Linux user and you want to create your own VPN, check out our how to set up a VPN server on Linux guide. We list the steps you need to take in order to create your own Linux VPN server.