Security researchers, backed up the EFF, have issued a warning over PGP and S/MIME encryption. You should stop using these standards to secure your emails immediately.
PGP has long been considered the gold standard for sending secure encrypted emails. It does not encrypt metadata and is very far from easy to use, but it is nevertheless widely regarded as by far the safest way to send secure emails.
Professor of computer security at Münster University of Applied Sciences, Sebastian Schinzel, however, tweeted on Sunday 14 May that:
"We'll publish critical vulnerabilities in PGP/GPG and S/MIME email encryption on 2018-05-15 07:00 UTC. They might reveal the plaintext of encrypted emails, including encrypted emails sent in the past.”
We'll publish critical vulnerabilities in PGP/GPG and S/MIME email encryption on 2018-05-15 07:00 UTC. They might reveal the plaintext of encrypted emails, including encrypted emails sent in the past. #efail 1/4
— Sebastian Schinzel (@seecurity) May 14, 2018
Professor Schinzel is a member of a research team consisting of a long list of respected security researchers, and which has been responsible for uncovering a number of cryptographic vulnerabilities. The most notable of these is the 2016 DROWN attack which put 33% of all HTTPS servers in the world at risk.
The Electronic Frontier Association (EFF) has confirmed the vulnerability:
"A group of European security researchers have released a warning about a set of vulnerabilities affecting users of PGP and S/MIME. EFF has been in communication with the research team, and can confirm that these vulnerabilities pose an immediate risk to those using these tools for email communication, including the potential exposure of the contents of past messages.”
ProPrivacy advice: Uninstall PGP immediately (at least for now)!
In line with all expert cryptographic advice to date, ProPrivacy.com recommends the use of PGP in a number of our core articles. Given that this warning is backed by the EFF, however, we strongly recommend following the EFF’s advice:
"Our advice, which mirrors that of the researchers, is to immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email. Until the flaws described in the paper are more widely understood and fixed, users should arrange for the use of alternative end-to-end secure channels, such as Signal, and temporarily stop sending and especially reading PGP-encrypted email.”
The article then provides links to guides on how to temporally disable PGP plug-ins in Thunderbird with Enigmail, Apple Mail with GPGTools, and Outlook with Gpg4win.
No mention is made of removing stand-alone PGP apps such as Gpg4win or PGP browser add-ons such as Mailvelope.
It is probably safe to assume that once more details about the vulnerability are disclosed, the enthusiastic open source PGP community will work hard to patch the problem in as short a time as possible. ProPrivacy.com is monitoring the situation and will update articles that recommend using PGP if and as necessary.
S/MIME
All advice published so far concentrates on PGP. This is not surprising as PGP encryption has so far been considered rock solid. That the vulnerability also affects S/MIME, however, may be more significant because S/MIME is much more widely deployed by businesses to secure their email communications.
S/MIME is very similar to PGP except that instead of users defining their own encryption methods and web of trust (how to share their private encryption keys), S/MIME uses predefined encryption standards and public-private keypairs distributed by a trusted authority.
This makes S/MIME much more transparent in use and easier for companies to deploy. Its reliance on a "trusted authority” to distribute the encryption keys is why privacy fanatics prefer PGP.
Conclusion
Until this issue is fully understood and (hopefully) fixed, you should avoid using PGP and S/MIME to encrypt emails. To communicate securely and privately over the internet, use Signal instead.
Image credit: By arka38/Shutterstock.
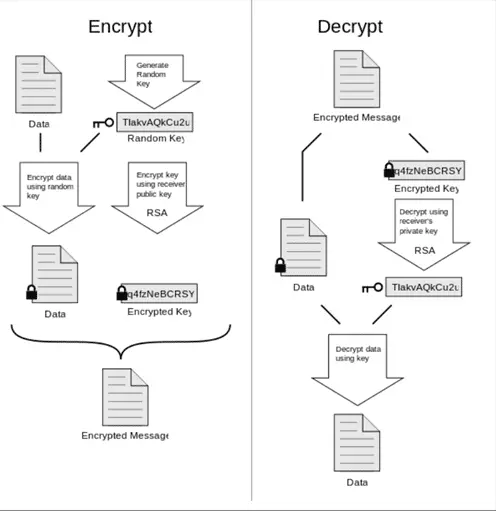
Image credit: xaedes jfreax Acdx, PGP diagram, CC BY-SA 3.0.
