The Marriott hack is the latest example of a massive cyber attack affecting a large international firm. 500 million customers had their data accessed including names, addresses, emails, date of birth, gender, passport numbers, and financial details.
While the enormity of the hack is shocking, the reality is, that this kind of attack is happening regularly. In the last few years Wendy’s, Chipotle, Target, eBay, Home Depot, Sonic, Under Armor, KMart, Sears have all fallen victim to massive cyber attacks by those keen to get their hands on stolen credit card details.
Perhaps the most frightening thing about the Marriott hack, is the fact that it stretched on for four years before anybody noticed. So, why is it important that firms notice quickly when they get hacked? What happens to all those credit card details when they get stolen? And, how is it affecting the people that get hit?
The dark truth
You have probably heard that stolen credit or debit cards end up on the Deep or Dark Web. For most people who have never been on the Dark Web this concept may seem foreign and removed. Unfortunately, this knowledge gap can cause people to be more easily victimized.
The Deep Web is the part of the internet that is not listed on regular search engines like Google or Firefox. It is vast, and it has a large number of eBay-like retail stores that sell all kinds of illegal drugs, weapons, services, and, you guessed it, stolen credit and debit card details.
The moment that a cybercriminal steals huge amounts of credit card details from a firm, that hacker will either put them on a Dark Web store under his or her control or sell them to a third party. So what do those stores do with the card details and how do they make them available to customers?
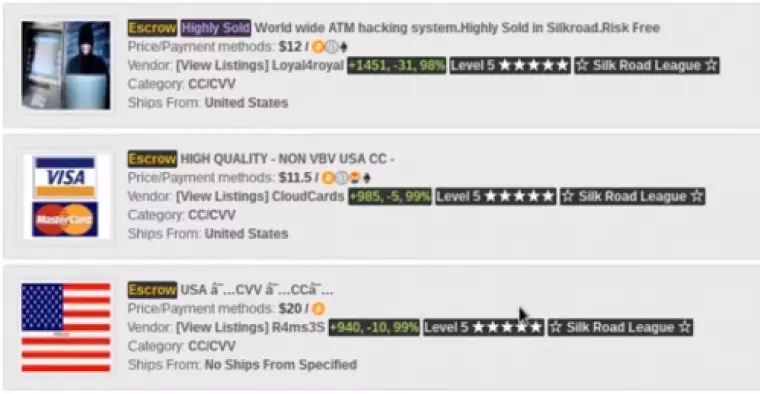
Card numbers - CC and CVV
These numbers can be purchased on the Deep Web for just about any country. The card details are sold with the corresponding details necessary to make a purchase. They are stolen from people using either phishing techniques, keylogging malware, or via hacking firms that legitimately hold the information.
This includes the name and address of the victim. Due to the fact these card details do not come with a physical card, they can be purchased much more cheaply. However, they are riskier and require some background knowledge in order to be used successfully.
Purchasing something online and having it sent to your home would make it extremely easy for law enforcement to track the user down. For this reason, most customers who purchase this kind of card information are usually purchasing and downloading software directly from online stores. These purchases are made using a proxy service to conceal their real IP address.
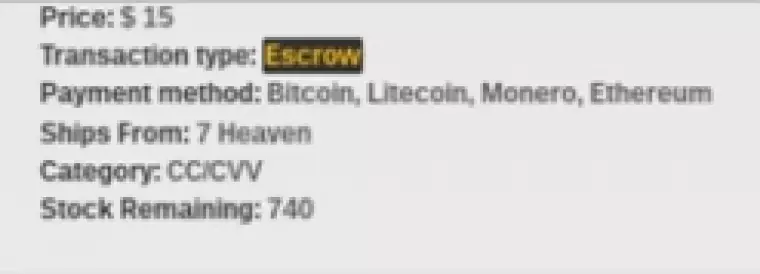
I discovered a listing by a seller on Silk Road 3.1 that claimed to have 740 US Credit Card CVV numbers for sale.
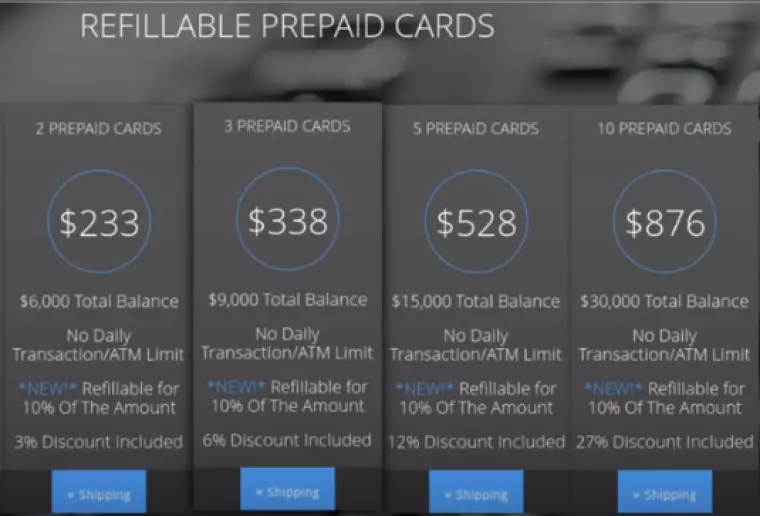
Prepaid cards
Many hackers use stolen debit and credit card numbers on the Dark Web in order to purchase prepaid cards and gift cards. Other cybercriminals may purchase stolen debit and credit card numbers, in order to buy hundreds of prepaid cards to sell on online and produce laundered cryptocurrency funds for themselves. If your card is hacked or phished you must ensure that you cancel it at once or your account could be fleeced in this way.
Prepaid cards can be sold on to consumers worldwide via the Dark Web. Customers evil enough to purchase these kinds of prepaid cards can get them with varying amounts of stolen funds. As they aren’t connected to the original victim’s bank account, they are considered a much safer option.
During my research, I discovered a Deep Web store called Fusion Cards. Its Dark Web website has a large number of prepaid cards available that can be purchased with varying amounts of funds.
Cloned cards
A cloned card is a physical fake version of a debit or credit card that has been created using the stolen details. These are usually created not just from the numbers on the card but also by "skimming” the magnetic strip of the card as it passes through a retailer’s point of sale.
These skimming attacks can happen at ATM machines or the ticket machines at train stations. However, skimming can also happen at point of sale terminals infected with malware or Trojans that send the sensitive data back to a Command and Control (CnC) server.
For a long time, chip and pin cards were thought to be a foolproof new way of avoiding skimming. That is why the US recently shifted all people onto this type of card, which is regulated by EMV standard. Unfortunately, however, the cybersecurity firm Kaspersky this year presented research findings that reveal that a criminal gang in Brazil has discovered a way to skim details from chip and pin cards. That means even this more secure kind of card can be cloned.
What does the customer get?
When purchased online from the Dark Web, these cloned cards are shipped with the corresponding name, date of birth, Address, Card Number, CVV, Expiry date, and even the skimmed pin number.
Cloned cards are considered much riskier than prepaid cards that have been topped up with stolen funds.
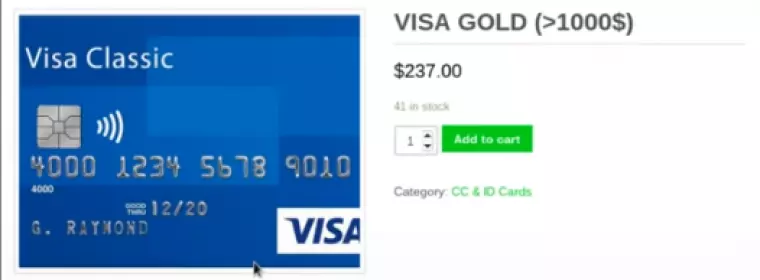
AltBay is a popular Deep Web retail outlet. On it, we discovered a listing for a card that costs $237 dollars. It comes with $1000 of spending credit available on the card. The vendor claims to have 41 of the cards in stock.
For Dark Web customers that have a bit more to spend, we found a listing for a Visa business card that costs $890 and comes with $10,000 of stolen funds.
Presumably, any victim being fleeced of such a massive amount has a bank balance large enough that they do not notice the loss straight away. It makes you realize just how important it is for people to carefully track their accounts and funds at all times.
Buying money… How do people use their cards?
Anybody that has a connection to the Deep Web via Tor Browser and some Bitcoins, Litecoin, Monero, or Ethereum, can go ahead and buy funds that have been stolen from credit or debit cards. Depending on what kind of card is purchased the customer is able to buy things in real stores or online. The option to transfer funds to a PayPal account or another online store is also a possibility - or to convert the funds to cryptocurrency or buy a gift card. Finally, people may choose to get cash out at an ATM.
One of the Dark Web stores we discovered had a disclaimer section explaining that people should completely cover their face before cashing out from an ATM because they have cameras. Somewhat hilariously, it also tells potential customers to act naturally as if the card was really their own.
How do people feel about using stolen cards?
Unfortunately, it isn’t just hardcore criminals buying these kinds of stolen card products. Some people are opportunists hoping to turn a little cash into more.
We found a customer feedback page where the vast majority of comments (99%) were from happy customers. This proves just how effective these stolen card services are and just how easy they are to use.
Sad cases
During our research, we discovered evidence of New Zealand card clones being sold that belonged to old age pensioners. The cloned cards in question where found on a store called Bazaar Plastic, and they were for a bank called Heartland Bank.
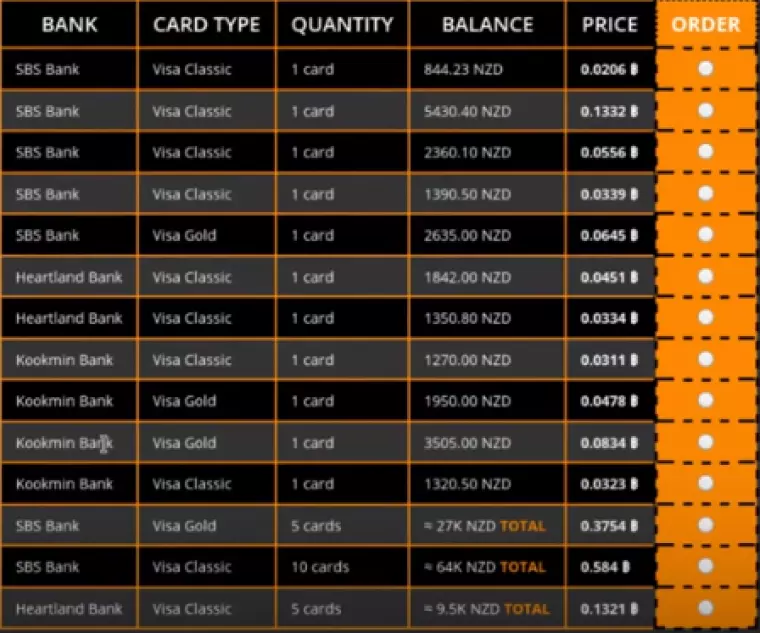
Heartland is a bank that primarily caters to old age pensioners and specializes in reverse mortgages. Thus, it is likely that some of these funds are being stolen from old people living in retirement homes.
This is the very real human cost of this trade, and anybody who ever considers purchasing a card like this should be reminded that there is always a real life victim. Purchasing a card on the Dark Web might be easy - and it might not feel like a crime - but it is a very serious offense that anybody with a shred of decency should avoid.
Future fraud prevention
The good news is that banks and tech companies are working hard to try and create solutions to identity theft and card fraud. This week, Mastercard and Microsoft announced a joint venture that aims to give people "a secure, instant way to verify their digital identity with whomever they want, whenever they want.”
According to the two firms, the service will allow people to "enter, control, and share their identity data their way–on the devices they use every day.” For the time being, the idea is still in the concept stage, with the firms promising more information. Joy Chik, corporate vice president of Identity at Microsoft said:
"We believe people should be in control of their digital identity and data, and we’re thrilled to first work with Mastercard to bring new decentralized identity innovations to life.”
In the meantime, people are reminded to keep a close watch on the media for hacking stories and remember to check their email accounts for alerts about hacks being made available by retailers, hotels, and other firms. Additionally customers should always watch for unusual spending on their accounts, as this should be reported to the fraud investigation team at the bank or card company immediately.
We hope knowing a bit more about how card numbers are stolen and used will inspire more people to take precautions. If you think you have been affected by the Marriott hack please check out our informative guide about what you should do next.
To stay secure when using Tor browser and to stop hackers from accessing your data, we would recommend using a VPN service. Check out our VPN services pages for more information and a list of the best VPNs around.
Image credits: Antonio Guillem/Shutterstock.com, RedHanded/Shutterstock.com,
