Websites and advertising companies love to know who you are and what you get up to on the web. The more they can find out about you and what you like, the better they can target ads at you. Of course, most internet users are none too keen on providing them with such intimate and privacy-invasive information. This results in an escalating arms race between advertisers keen to uniquely identify website visitors and track them as they surf the web, and ordinary internet users keen to protect their privacy. An increasingly prominent weapon in advertisers arsenal is fingerprinting…
I have discussed browser fingerprinting before. This invasive technique uses attributes that make your web browser different from others users’ browsers (such as browser name, operating system, and exact version number of the browser, installed fonts and plugins, supported data types (so-called MIME types), screen resolution, system colors and more) to uniquely identify you when you visit a website. And once uniquely identified, you can be tracked as you visit other websites.
I have also discussed canvas fingerprinting, a special form of browser fingerprinting that uses a script that asks your browser to draw a hidden image, and then uses tiny variations in how the image is drawn to generate a unique ID code, which can then be used to track you.
Audio (or AudioContext) fingerprinting
Researchers at Princeton University have found (.pdf) that use of a new variation on this idea, audio fingerprinting, is becoming increasingly common. This technique leverages the JavaScript AudioContect API in order to help uniquely identify users,
“Audio signals processed on different machines or browsers may have slight differences due to hardware or software differences between the machines, while the same combination of machine and browser will produce the same output… Using the AudioContext API to fingerprint does not collect sound played or recorded by your machine. An AudioContext fingerprint is a property of your machine's audio stack itself.”
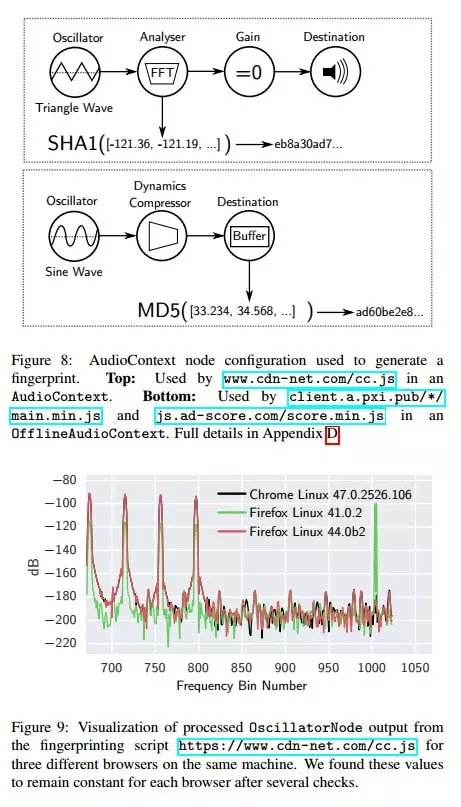
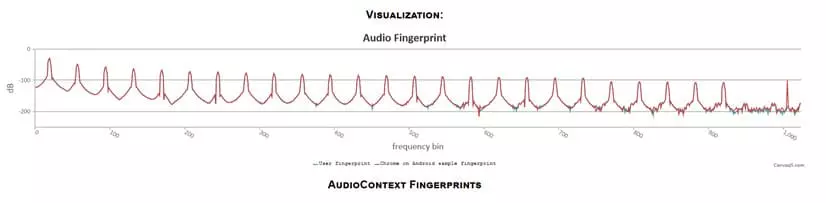
If you would like to see your audio fingerprint, the researchers have created the AudioContext Fingerprint Test Page, which provides a visualisation your fingerprint based on information collected using the AudioContext and Canvas APIs installed on your system.
Battery (Status API) Fingerprinting
This technique uses a little-known HTML5 “feature” called the Battery Status API to detect how much battery power is left your laptop, tablet, or smart phone when you visit a website.
The official World Wide Web Consortium (W3C, the organisation that oversees the development of the web’s standards) specification states that this API has a minimal impact on privacy. A paper (.pdf) by French and Belgian security researchers, however, found that,
“A third-party script that is present across multiple websites can link users’ visits in a short time interval by exploiting the battery information provided to Web scripts. In order to do that, scripts can use the values of battery level, dischargingTime and chargingTime. The readings will be consistent on each of the sites, because of the fact that the update intervals (and their times) are identical. This could enable the third-party script to link these concurrent visits. Moreover, in case the user leaves these sites but then, shortly afterwards, visits another site with the same third-party script, the readings would likely be utilized to help in linking the current visit with the preceding ones.”
The researchers also noted that in addition to tracking website visitors using their battery level, battery capacity could also be used as a tracking vector. Battery fingerprinting is mentioned Princeton paper too, although those researchers found only two scripts that exploited it.
Tip: My thanks to reader Pogue, who sent in the following tip to disable the Battery Status API in Firefox. In about:config set dom.battery.enabled = false
Combined tracking techniques
Perhaps the most interesting finding in the Princeton paper is that websites and ad analytics companies deploy a range of techniques, which in combination are able to defeat users’ ever more vigorous attempts to prevent such tracking,
“Ghostery and a combination of EasyList and EasyPrivacy both perform similarly in their block rate. The privacy tools block canvas fingerprinting on over 80% of sites, and block canvas font fingerprinting on over 90%. However, only a fraction of the total number of scripts utilizing the techniques are blocked (between 8% and 25%) showing that less popular third parties are missed. Lesser-known techniques, like WebRTC IP discovery and Audio fingerprinting have even lower rates of detection.”
Canvas font fingerprinting is a feature of “regular” browser fingerprinting (using a browsers font list to help identify a user), and WebRTC IP discovery is the same “feature” that allows websites to users' true IP address even when using a VPN (the WebRTC “bug”).
Conclusion
It is precisely because of the widespread use of such invasive and downright sneaky tactics by advertisers that ever increasing numbers of internet users are turning to adblockers. Web sites and advertising companies bemoan the loss of revenue, but it their own fault.
We did not give them permission to spy us, building up ever more accurate and creepy profiles of us as we surf the internet, in order to better flog us stuff. When we took explicit measures to prevent this happening (such as learning to manage our cookies), websites effectively went to war against their own visitors (and customers).
More and more underhanded methods to spy on interest users have been developed, despite being against both our best interests and our wishes (in fact, they have been developed exactly because of our attempts to evade such tracking).
Websites do need to make money out of the often great content or services they provide, but until they do so honestly, transparently, and using a model that does not invade our privacy against our wishes, the rise of consumers voting with their adblockers will only rise.
