In the first of this two-part guide we looked at PGP encryption, its open source iteration GnuPG, and the Windows version of GnuPG, Gpg4win. We showed you how to install Gpg4win, use it to create key pairs, and to encrypt and decrypt files and folders.
In this part of the guide we’ll look at how to use Gpg4win with the popular free and open source email client Thunderbird (from Mozilla, the makers of Firefox), making use of the Enigmail extension for Thunderbird (and SeaMonkey). For this to work then, you will need:
- Gpg4win
- Mozilla Thunderbird
- Enigmail extension
We have to warn you that setting up your email to use PGP is not a simple task, but the good news is that once set up, it is easy and fairly transparent in use. Hopefully this guide will make the setup process as painless as possible.
Install everything
1. Download and install GpG4win (this is covered in detail in Part 1 of this guide).
2. Download, install, and setup Mozilla Thunderbird for any accounts you wish to use. Thunderbird recognizes most popular email services, and will automatically apply the correct settings when you enter your email address and password – just follow the setup Wizard. If you need to enter your account settings manually, then click on the Menu icon (with 3 horizontal lines at the top right of the Thunderbird window) and select Options -> Account Settings -> Server Settings.
3. Download and install the Enigmail extension for Thunderbird. To do this:
a. Click on Menu -> Add-ons.
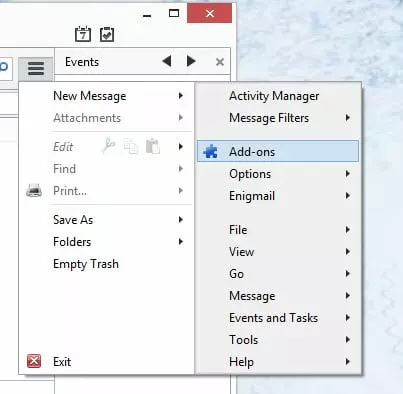
b. Type ‘enigmail [enter]’ into the search box and then click the ‘Install’ button.
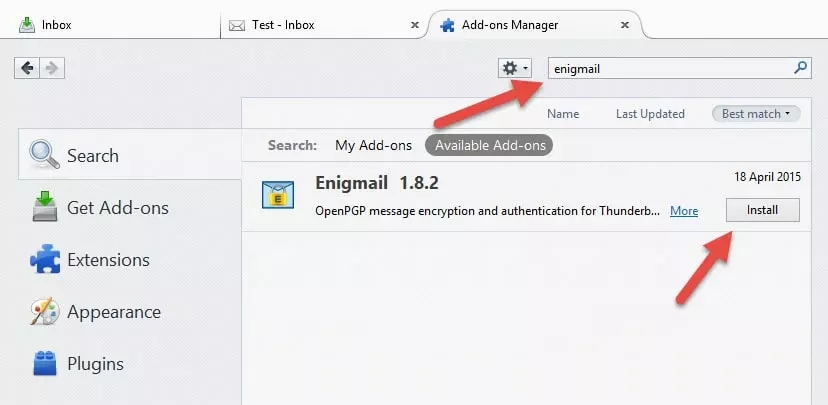
Restart Thunderbird..
4. Confirm that Enigmail and GnuPG are working by going to Add-ons -> Extensions -> Enigmail Options. Under Basic Settings / Files and Directories you should see ‘GnuPG was found in C:\Program Files\Gnu\GnuPG\pub\gpg.exe’.
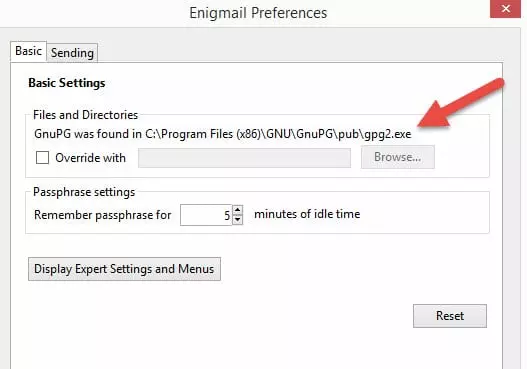
5. If you instead see ‘Could not find GnuPG’, tick the ‘Override with’ box and Browse to where the GnuPG program is installed (‘C:\Program Files (x86)\GNU\GnuPG\gpg2.exe' by default.)
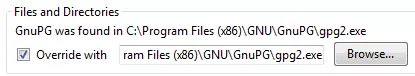
Click OK to return to Thunderbird.
Generate a key pair
The next step is to generate a key pair. Enigmail provides two ways to do this, using the OpenPGP Setup Wizard or the Key Management screen.
Using the Setup Wizard
1. Go to Menu -> Enigmail -> Setup Wizard. Ensure 'I prefer a standard configuration (recommended for beginners) is selected and hit 'Next >'.
2. If you followed our tutorial in Part 1 of this guide, then you will already have generated a key pair which you can select to use here. For the purposes of this tutorial, however, we will generate a new key pair. To do this, select 'I want to create a new key pair for signing and encrypting my email.'
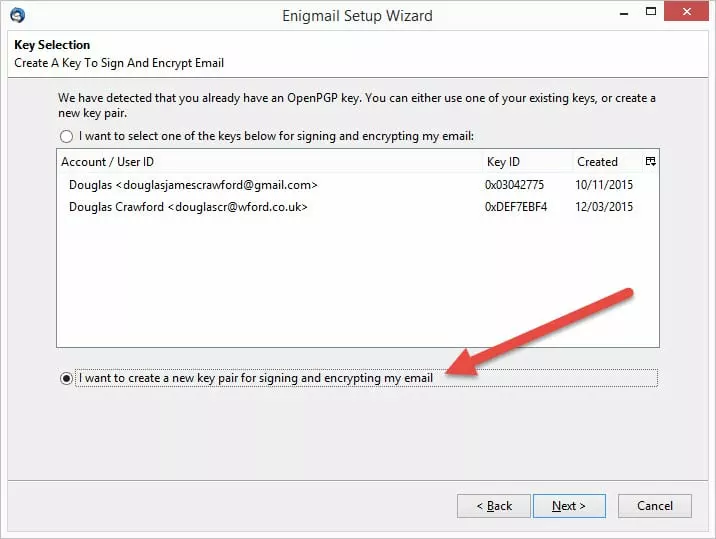
3. Choose a secure pass phrase which is used to protect your private key (try to aim for one that is at least 20 characters long, using non-sequential words). You will use this to decrypt emails sent to you using your public key. If this ever becomes compromised you should immediately revoke the matching public key, and generate a new key pair (and then publish it.)
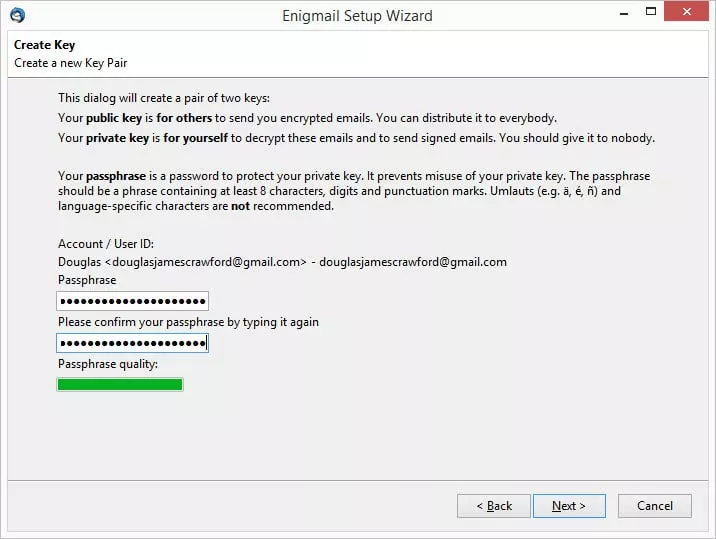
4. Wait while a key is generated. It is then a good idea to create a revocation certificate (just follow the Wizard).
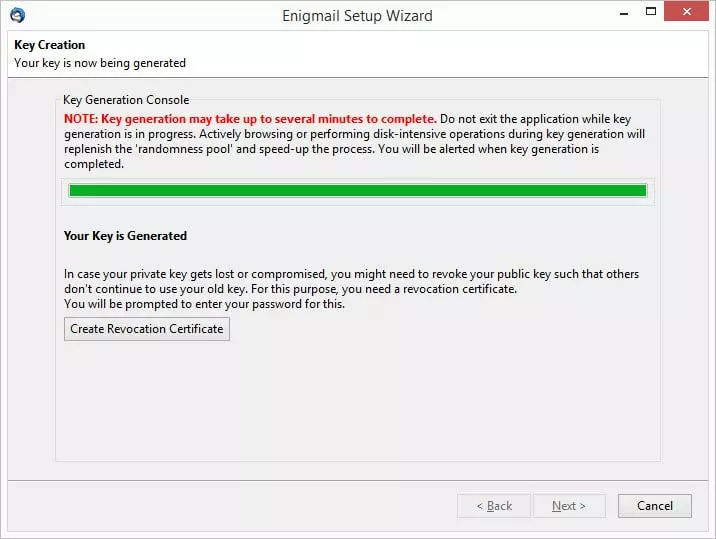
5. Once done, click ‘Finish’, and your new key pair is created!
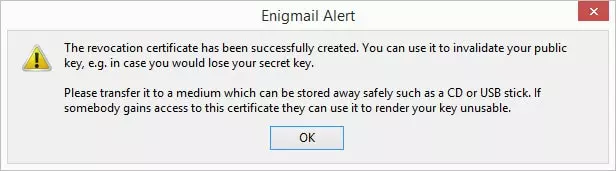
All keys generated using this method are secured with 2048-bit RCA encryption and expire after 5 years.
Using Enigmail Key Management
Once you are comfortable with the process of generating a key pair, you can perform the task quickly and easily by going to Menu -> Enigmail -> Key Management, then Generate -> New Key Pair, and simply enter the required information.
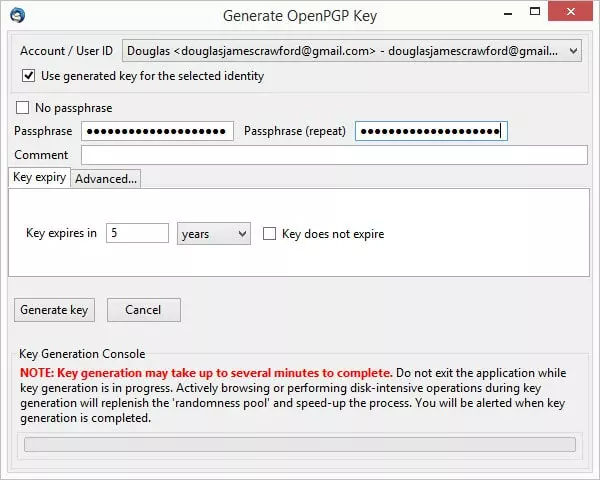
This method lets you choose how long a key will last before expiring and, under the ‘Advanced’ tab, what kind of encryption is used.
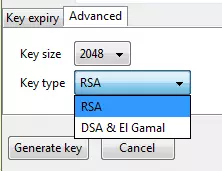
It is normal practice to generate a new key pair for each email account you have.
Configure Enigmail for use with your email account
To make sure that everything is set up properly, go to your email account settings (Menu -> Options -> Account settings) and click on OpenPGP security. Ensure that ‘Enable OpenPGP support (Enigmail) for this identity’ is checked, and that the settings are as you want them.
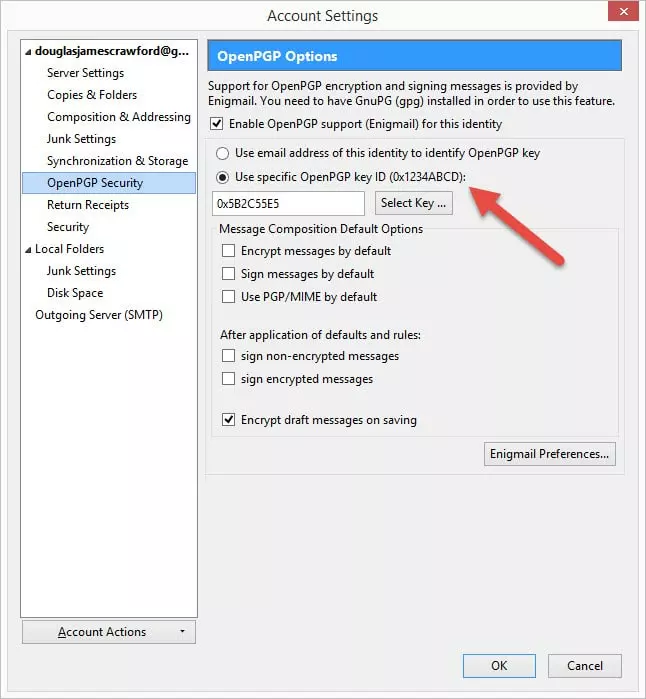
Exchanging public keys
Okay, so now you are set up and have a key pair. The next step is to share your public key (or keys) so that others can send encrypted emails to you.
For you to send encrypted emails you require your recipients' public keys. Remember that your public key is designed to be public, and the more people who have access to it, the more people who can send you encrypted emails.
How to send a public key to your contacts
1. Directly
In Thunderbird click ‘Write' to start a new message. Write the email and select the recipient(s) as normal, then select 'Attach My Public Key' (the paperclip icon will turn yellow to show this is enabled.) When you are ready, hit 'Send'.
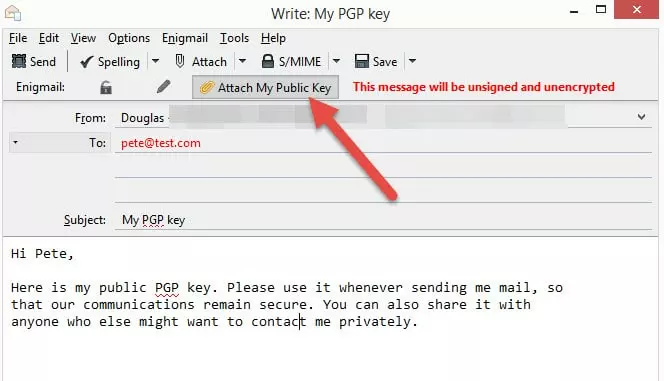
Note that the red lettering in the 'To:' field alerts us the fact that we do not have the public OpenPGP keys for this recipient
2. Using a keyserver
A better way to share your public key is via a keyserver (basically, a server that stores public OpenPGP keys, so that they can be accessed by anyone.) A big advantage to using a keyserver is that if for any reason you need to revoke your public key (for example your if your private key is compromised), this can be easily done just once by deleting the old key and uploading a new one to the key server (rather than sending out new keys to all your contacts.)
This also makes it easy for anyone to send you secure email without having to ask you to send them your public key to them first.
To upload your public key to a keyserver go to Menu -> Enigmail -> Key Management. Select the key that you would like to upload, then go to Keyserver -> Upload Public Keys.
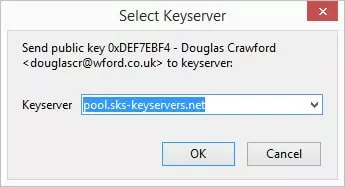
Select a keyserver from the dropdown list
You can now include the name of your keyserver address and Key ID in your signature to advertise the fact that you have a public key available.
How to import a public key
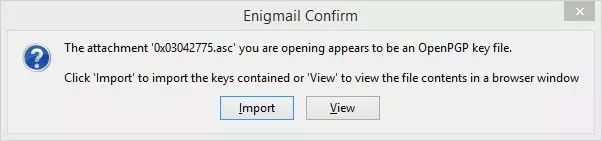
1. When you receive an encrypted message that contains a public key, double-click on the attached .asc file, and Enigmail will offer to import the key for you.
2. To find a public key uploaded to a keyserver, go to Menu -> Enigmail -> Key Management -> Keyserver -> Search for Keys.
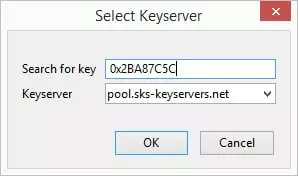
You can search by Key ID or by email address (always prefix the Key ID with 0x...).
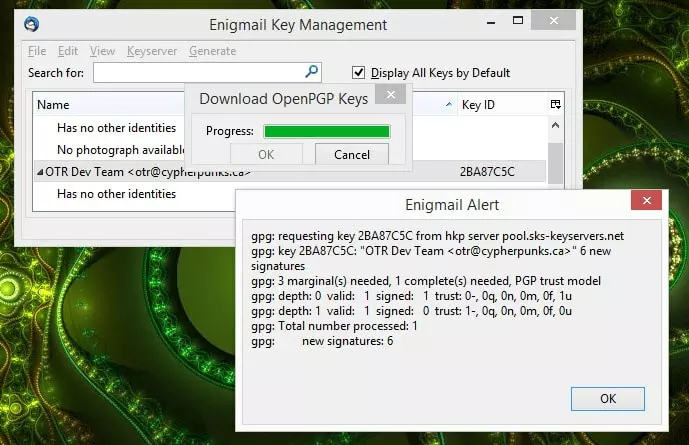
Knowing the name of the keyserver is good, by Enigmail does a good job of finding keys anyway
You can also tell Enigmail to 'Find keys for all contacts'.
How to validate a key pair
An important final security step is to validate and sign a key pair, which should be done using a method other than email. Face-to-face is best, although encrypted VoIP is also a good option (remembering that telephone conversations cannot be considered secure in this age of blanket government surveillance). Be very careful to make sure that you are talking to the right person!
What you both need to do is verify the public fingerprints of the keys that you have exchanged. To do this, you should both go to Menu -> OpenPGP -> Key Management (you may need to check the ‘Display All Keys by Default’ box). Right-click on a particular key (both of you selecting the same key of course), and select ‘Key Properties’.
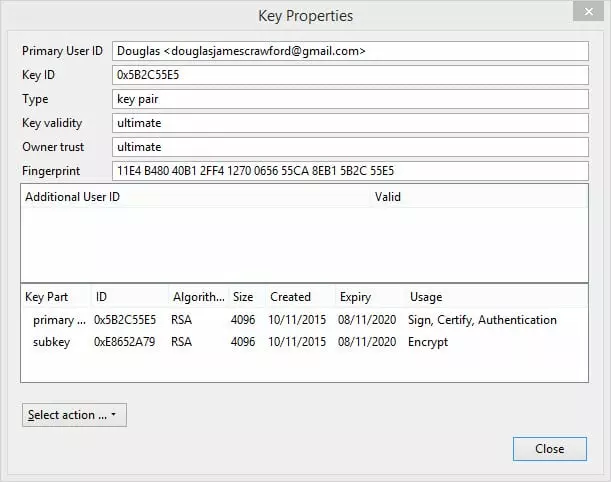
Both of you should confirm that the Fingerprint for each key you have matches the sender’s original.
Signing a validated key
Once you have validated a public key, you must sign it to confirm that you consider it valid. Choose Select action -> Sign Key.
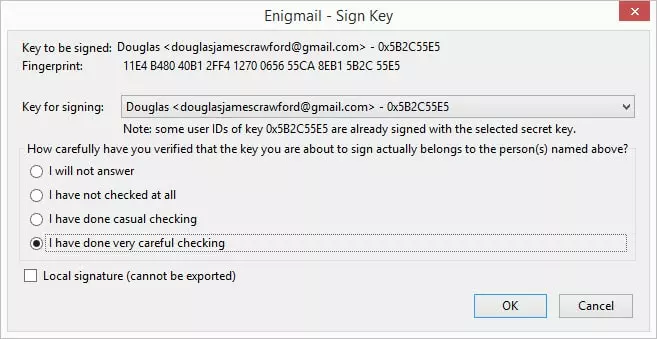
Click on the ‘I have done very careful checking’ button, and then 'OK'.
Hurray! You have now ready to start sending and receiving encrypted email! Phew! We did say it was a bit complicated…
Encrypting and decrypting emails
To ensure the highest level of security, the following precautions should be followed when sending encrypted emails:
- Use non-descriptive Subjects for your emails as the headers of an email message (Subject, To, CC and BBC fields) are not encrypted
- BCC is better than CC when sending messages to a group (so they can’t see who else is in the group)
- Use PGP/MIME when encrypting messages with attachments, so that the attachments are also be encrypted
Encrypting an email
Click ‘Write’ to start an email. You can only send encrypted emails to recipients for which you have public keys (if you do have a public key for the recipient their name will display in black, if not it show in red.) You can add any attachments, and specify that you want to improve security by adding a signature (which shows that someone trusts your key.). When you are ready, hit 'Send.'
If the message contains attachments, you will be asked how you want them handled before the message is sent. For most purposes the default settings are fine.
Decrypting an email
Thunderbird will automatically try to decrypt an encrypted email when you open it. You will be asked for the OpenPGP passphrase (your private key), and that’s it!
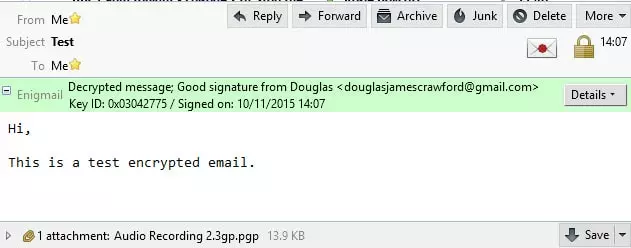
A notification at the top of the message window will let you know the message been decrypted (including any attachments), and the signature authenticated.
Conclusion
As you can see if you have followed this tutorial, despite being a pain to set up, once done, sending and receiving securely encrypted emails between trusted contacts is fairly easy. Probably the biggest difficulty will be getting your contacts to bother using secure email at all, and helping them tackle the somewhat steep learning curve involved in setting it up.
When it comes to securing your email against prying eyes, however, there really is no substitute for PGP encryption, and this combination of Gpg4win, Thunderbird and Enigmail is among the most user-friendly (and once in place, elegant) solutions available for Windows users. It should be noted that the Firefox OpenPGP add-on Mailvelope is easier to use, but because it works within the browser, it cannot be considered as secure.
Note (10 November 2015): This is a completely revamped and improved version of an older article. I would like to thank our reader Dicko for helping to clear up some confusions in the original.
For more information about keeping secure online with Windows, take a look at our best VPN for windows 7 & 10 page.
