Email Security Protocols are hugely important because they add security to your digital communications. Without this extra security, anybody could intercept the contents of your emails.

Email Security Protocols are designed to secure your communications as they pass between webmail services over the internet. In this blog, we will take a look at each of the commonly used security protocols, and explain what each of them does to keep your emails safe.
In addition, we will highlight which kind of security protocol you should seek to employ if you want the most secure end-to-end-encryption for your emails.
Why not check out our Email security guide for more information on different aspects of email security.
Transfer Protocol – What is SMTP?
You would be forgiven for assuming that Simple Mail Transfer Protocol (SMTP) is an email security protocol. It is not.

SMTP is a communication protocol for electronic mail transmission that does not contain any native security. Thus, the use of SMTP alone leaves your emails completely vulnerable to eavesdroppers.
As a result, it is vital to use some kind of email security protocol on top of SMTP if you want to communicate electronically without the content of emails being easily accessible to your ISP and anybody else who intercepts them.
The good news is that there are various security protocols available that work on top of SMTP, so you can send emails without them being open to the entire world.
Email Security Protocols
Transport Layer Security

Transport Layer Security (TLS) is the most common protocol used to secure emails as they pass over the internet. It is an application layer protocol that works on top of SMTP to provide security for your emails. It is the predominant protocol used by web clients and servers to encrypt emails.
TLS functions by providing a set of rules (known as a security framework) to secure your SMTP messages. TLS consists of two layers:
- The TLS handshake layer (which initiates and validates the connection).
- The TLS record layer (which secures application data using the keys created during the Handshake).
Below, we have briefly outlined how the process works:
The Transmission Control Protocol (TCP) is used to establish a secure handshake between the email client and the email server. This validates those two endpoints so that the process of sending a message securely can begin.
Once the handshake has occurred, the email server responds by sending back the TLS Digital Certificate and the server's public encryption key to the email client.
At this point, the client verifies the certificate and generates a Shared Secret Key (SSK) using the public key, which is sent back to the server. The server then decrypts the SSK allowing for the client and the server to begin transmitting your private emails.
Opportunistic TLS vs Forced TLS
- Opportunistic TLS allows an email client to upgrade from an insecure plain text connection to an encrypted connection on the fly. STARTTLS is the email protocol command used by the email client to ask the email server for this upgraded connection. In this setup, if the command fails, the email will still be sent without encryption.
- Forced TLS is a protocol configuration that insists on a TLS connection being established before an email is sent. In this instance, if an encrypted tunnel between the email client and the server cannot be established, the email will not be sent to the recipient.
Digital Certificates
Digital certificates are a type of public-key cryptography that can be used to sign and encrypt emails to send them securely. Digital certificates work by allowing people to communicate data with each other using a pre-defined public key.

Digital certificates are installed directly onto your computer where they reside to validate the identity of your machine during the sending of encrypted electronic data (in this case, an email).
When you have a digital certificate, the public key is available to anybody who wants to send you an email. When you receive the email, you decrypt it with your private key. This type of cryptography is called asymmetric encryption.
S/MIME
Secure/Multipurpose Internet Mail Extensions (S/MIME) is a common protocol used to send secure emails with end-to-end-encryption. It is supported by the vast majority of email services and clients.
S/MIME leverages signatures known as digital certificates to authenticate and send encrypted emails that cannot be read by anybody but the authorized recipient. This makes the emails secure against eavesdroppers while in transit.
S/MIME always encrypts the contents of your email messages before they are sent over the internet. However, metadata contained within the header (such as details about the sender, recipient – and any other parts of the email header) remain unencrypted.
This results in that metadata potentially being harvested by ISPs, email providers, or the government. If you want to prevent this layer of tracking, you will need to subscribe to an email service like Tutanota.
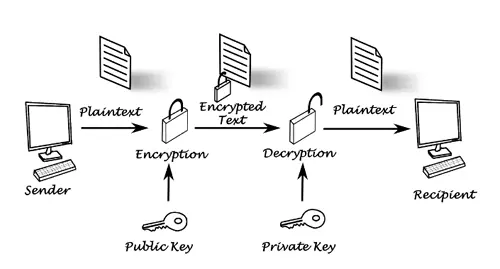
Pretty Good Privacy (PGP) and OpenPGP
PGP – and its more commonly used open source variation OpenPGP – is an encryption protocol used for sending highly secure end-to-end-encrypted (E2EE) emails.
It is widely regarded as the most secure E2EE for emails and is the best way for sending completely private emails that cannot be accessed by anybody but the intended recipient.
Setting up and using OpenPGP is sometimes considered techy by beginners due to the need to create a personal OpenPGP key pair (the public and private keys needed for this kind of asymmetric encryption). However, creating this key pair and storing/sharing the public key is actually one of the easiest ways to gain much better security for your emails.
As with S/MIME protected emails, it is worth noting that OpenPGP encrypted emails still allow third parties such as ISPs, email providers, and government agencies to snoop on email metadata contained within the header (such as the identity of the sender and recipient).
Sender Policy Framework (SPF)
Sender Policy Framework (SPF) is an email authentication method used to prevent the forging of a sender's address during the transmission of an email.
This stops spammers from sending messages that appear to come from somebody else's domain and helps to protect people against phishing and malicious attachments (which are inevitably more successful when a cybercriminal can spoof a legitimate domain).
The Sender Policy Framework has three core components:
- The framework
- An authentication method
- An email header – used to convey the information
When an email is sent, the DNS record in the header ("envelope from") can be verified to detect whether the originating IP address was authorized to send the email. If it was not, the email client knows to treat the email as suspicious and reject it.

DomainKeys Identified Mail (DKIM)
DKIM is another authentication method used to detect forged sender addresses. As with SPF, DKIM allows an email server to validate that the sender of an email is actually who they claim to be. This allows DKIM to prevent spam and phishing.
DKIM works by giving an email a digital signature, which is verified to ensure it came from the right domain. DKIM also helps to check that the sender was authorized to send an email from the domain in question (to prevent spoofing).
DMARC
Domain-Based Message Authentication, Reporting & Conformance (DMARC) is an email authentication protocol that works on top of DKIM and SPF. It is also designed to give users the ability to protect their domain against email spoofing.
DMARC can only be used for authentication if both SPF and DKIM have been setup. Once implemented correctly, the DMARC Analyzer tool can be used to access DMARC reports that contain information about who is sending emails from a domain.
DMARC does this by comparing the "header from" domain name to the "envelope from" domain name defined during the previous SPF check. Used in combination, these three security elements provide more reliable protection against the sending of unauthorized emails from your domain.
Why Are Email Security Protocols Important?
Anybody who emails without leveraging email security protocols it exposing their data. As a result, their emails could be intercepted and the sensitive data they contain could be stolen.
In addition to securing the data contained within emails, security protocols exist that prevent cybercriminals from sending emails that appear to come from your domain.
To ensure that this doesn't happen, we recommend that you setup SPF, DKIM, and DMARK authentication for your personal email domain. And, if you want strong E2EE for your messages, we recommend opting for a secure email service that provides OpenPGP compatibility.
