Pretty Good Privacy (PGP) remains the gold standard of email encryption despite the growing number of decent privacy-focused webmail services – but how do you set it up on a Mac device? We'll guide you through the process in this guide, explain how PGP works, and delve into just how secure it really is.
PGP has its issues (which we'll discuss below), but it's still the most widely used email encryption system, and therefore the most interoperable. As well as working in tandem with other system, regardless of the platform, PGP can also be used to sign and encryption all sorts of other stuff – though it's primarily used to secure emails.
How does PGP work?
The details of how PGP works are, to be honest, rather complicated. The important thing to remember is that PGP uses public-key cryptography.
Each user has a private key and a public key. The private key should be kept secret, seeing as it's also used to decrypt incoming emails, and these emails are sent to the user via their public key. The public key can therefore be shared freely – because it's what allows other people to send the user those encrypted emails.
- Private key – kept secret and used to decrypt own mail
- Public key – distributed so that others can use it to encrypt mail for sending to you
For this tutorial, we’ll stick to how to use PGP for encrypting emails, but PGP keypairs are also useful for signing and verifying digital signatures.
PGP vs OpenPGP
When discussing PGP these days we almost always mean OpenPGP. This is an open-source, 100% compatible clone of the now closed-source original PGP software, now owned by Symantec.
Issues with PGP
When PGP is used to secure emails, the metadata - such as email addresses of both the sender and recipient, date and time of sending, and e-mail’s subject line - is not encrypted. Just the body text and any attachments.
Another problem with PGP is that it does not use Perfect Forward Secrecy (PFS). So, once keys for one encrypted email are broken, all other emails encrypted using the same keys will also be compromised.
Arguably the biggest problem with PGP, though, is that it's just not very easy to use – which means that most people simply don't use it. But we don't believe in giving up here at ProPrivacy, and will walk you through two easy ways you can use PGP on your Mac.
Method 1: Malivelope
Mailvelope is a free and open-source browser extension for Chrome and Firefox that makes using PGP on your Mac about as easy as PGP is ever likely to get. Please check out our full Mailvelope How-to guide for a detailed look at how it works.
Method 2: GPGTools with GPG Mail
The most common implementation of OpenPGP is Privacy Guard (also known as GnuPG or just GPG). GPG on its own is a basic command-line tool, but GPGTools for macOS provides a GUI interface and advanced features.
It is worth noting that, in 2018, GPGTools make headlines due its vulnerability to the EFAIL attack which affected all versions of PGP at the time. Since GPGTools 2018.2, however, this vulnerability has been patched.
GPGTools is free, but the GPG Mail plugin for Apple Mail is designed to help fund the open-source project and costs $22. This is a one-off fee, but you do need to pay again for new versions as they are released.
-
Download and install the GPG Suite.
Do please make sure to verify the download before installing it. During installation, stick with all the default settings.
-
Create a new keypair
.
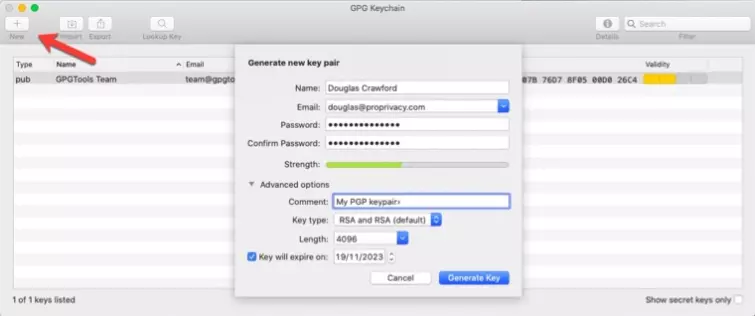
Open the GPG Keychain app, select New (the + sign) and fill in the relevant details. You can leave the Advanced options alone or play with them as you please.
![creating a GPG Keychain]()
-
Upload your public key to a keyserver.
This will allow others to find it using your email address so that they can send you secure PGP-encrypted emails.
But remember; once a public key is uploaded to a keyserver it cannot be deleted. The keyserver will send you an email asking you to confirm the upload.
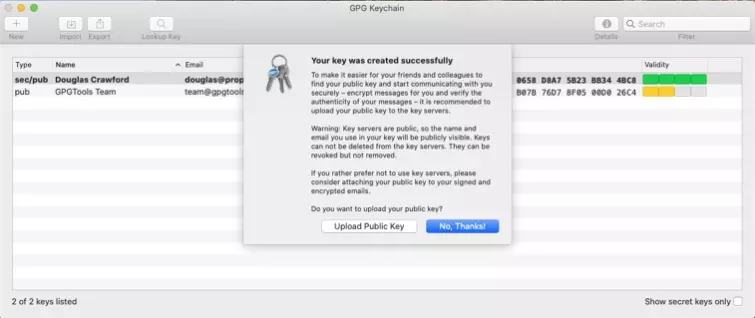
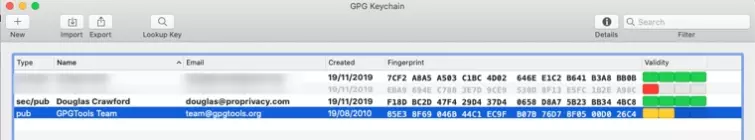
You will see your newly created key in the GPG Keychain.
![key successful message]()
If you already have a keypair then you can import it by clicking the Import button. You can then right-click on it -> Send Public Key to Keyserver.
-
Send an encrypted email.
In order to send a PGP-encrypted email, you will need the recipient's public key. If they have already sent it to you (as an email attachment, for example) then you can import it using GPG Keychain.
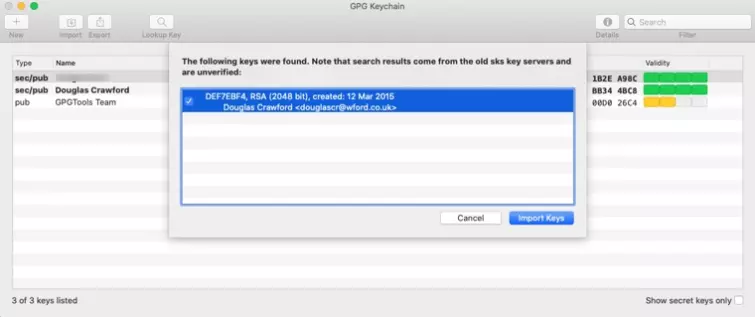
If you already have it, then you can search by email address for public keys that have been uploaded to a key server. Once you have found the key you want, simply import it into your GPG Keychain.
![GPG keychain import]()
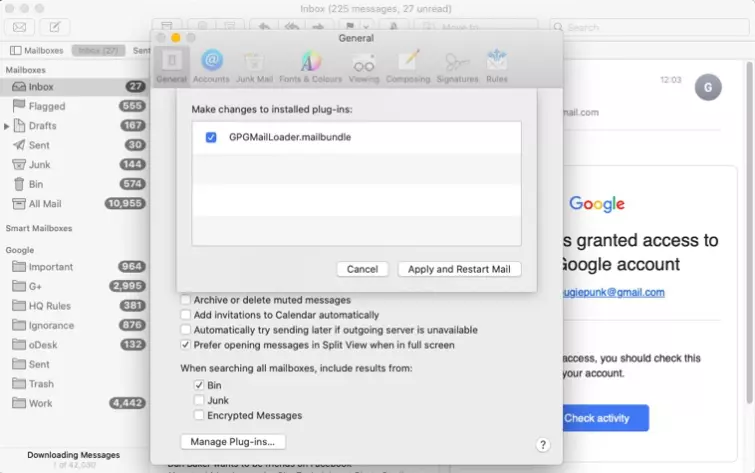
Open the Apple Mail app. If you're using an up-to-date version of macOS (10.14 Mojave+), you will need to enable GPG in Mail. To do this, Go to Preferences -> General -> Manage Plug-ins and enable the GPGMailLoader.mailbundle plug-in.
![changing installed plug ins]()
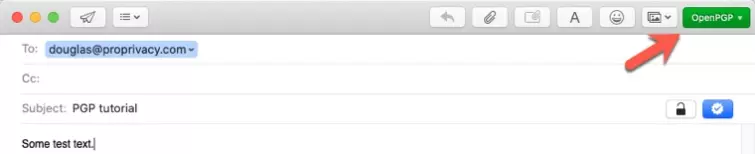
Then simply compose an email as normal, ensuring that OpenPGP is selected in the new green drop-down button to the top right of the compose screen.
![OpenPGP]()
When you have finished writing your message, you can sign and/or encrypt it using the two buttons to the right of the Subject line:
A) Sign - this verifies that the email was sent by yourself. When GPG Mail is installed, all messages are signed by default (button is blue). Click on the button to turn signing off.
B) Encrypt - encrypts the content of the message plus any attachments. It does not encrypt the subject line or hide any other metadata. Click the lock icon (turning it blue) to encrypt your email.
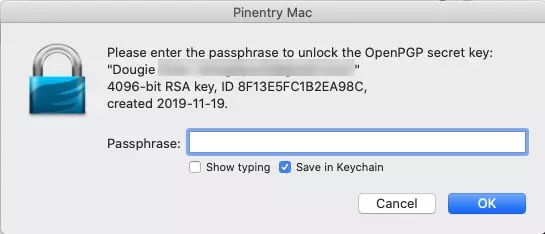
Hit Send, and you will be asked for the password to your PGP key. If you are worried that an adversary may gain physical access to your Mac, then you should untick "Save in Keychain.”
![PinEntry Mac]()
-
Receive encrypted messages
When you receive PGP email that has been encrypted and/or signed with your public key, GPG Mail will automatically decrypt it and/or verify the signature using your private key.
![Received encrypted message]()
-
Verify and sign keys
For maximum security, you should verify and sign keys. You verify a key by comparing the fingerprint you have of the key with the fingerprint owned by the sender to ensure they are identical. Ideally, this is done face-to-face, but a secure communication channel such as Signal Messenger will suffice.
Each imported key’s fingerprint is prominently displayed in GPG Keychain.
![GPG Keychain finger printing]()
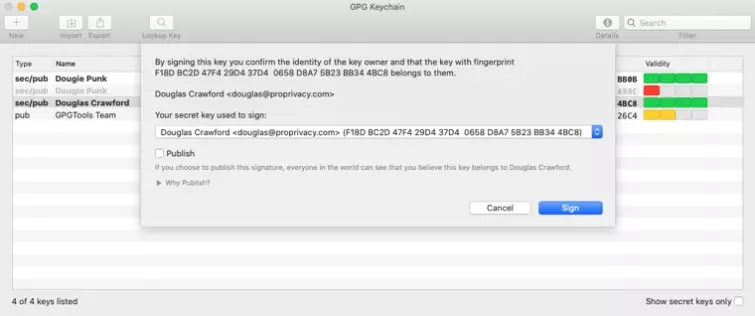
Once you are satisfied with the authenticity of a key, you can sign-it to confirm that you consider it valid. PGP works on a chain of trust, so you can opt to publish your signature in order to help others decide if the key is authentic.
![publishing signature]()
And that’s the basic outline of how to use GPGTools to send and receive PGP emails in macOS. GPGTools has more tricks up its sleeve, however, which we may explore in future articles.
Alternatives to PGP
Although PGP sets the bar when it comes to email encryption, it's not exactly user-friendly – and you might wind up looking for an alternative that's easier to implement. The good news is that there's a long list of secure email providers out there that already use PGP encryption and will work harder than most mainstream webmail services (like Google Mail) to keep your messages and documents away from prying eyes.
These secure services come with plenty of other benefits, too! For a start, you'll get a sleek UI to play with and apps for all of your devices, which makes sending and receiving encrypted emails a lot easier (especially if you're on the go). Secure services also typically encrypt your email headers and subject lines, too, and some even secure your contacts! The best email providers also offer multi-factor authentication, giving your account an extra layer of protection, the option to set email expiry dates, and (sometimes) the ability to create disposable email addresses.
All these measures ensure that the confidential details in your emails are only ever seen by your chosen recipient. Plus, PGP-friendly providers can communicate effortlessly with other services that support PGP – and keep any communication to and from non-PGP users or services secure, too.
If you're interested in learning more about our top secure email picks, or want to compare providers, check out our in-depth guide as well as the table below.

From $1.13/month
The best budget-friendly alternative email service. A green provider with an inexpensive subscription, as well as two-factor authentication, anonymous payment options, and its own PGP key directory. With a 14-day trial period.
- ProPrivacy TrustScore:
- 9.8 out of 10
- Encrypted messages to non-users
- No
- Calendar
- Yes
- 24/7 live chat
- No

From $0.00/month
The best secure alternative email service. Uses end-to-end encryption, and perfect forward secrecy, to protect your emails regardless of who you send them to. Includes a forever free plan.
- ProPrivacy TrustScore:
- 9.7 out of 10
- Encrypted messages to non-users
- Yes
- Calendar
- Yes
- 24/7 live chat
- No