Pricing and models
Prices start at $79.99 for the Original model, ranging up to $119.99 for the Pro. All versions except The Original (which uses a wired Ethernet connection) are WiFi routers.
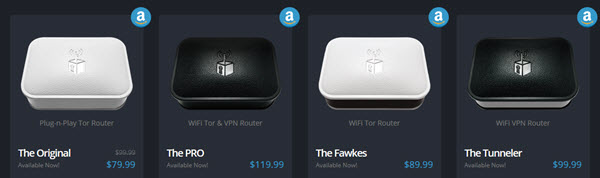
All models except the Pro feature a 400mhz CPU, 64mb DDR2 RAM, and 16mb Flash RAM, while The Pro model sports noticeably beefier specs with a 650mhz CPU, 128mhz DDR2 RAM, and 64mb Flash RAM. Anonabox explains that the Pro’s higher specs are required for it to run VPN and Tor together smoothly. The chipset used in all models is the Atheros AR9331 MIPS 24k.
All WiFi routers support up to the 802.11n wireless standard at 300Mbps, rather than the newer (and much faster) 802.11ac standard, and all routers sport 1x 1Gb LAN and 1x 1Gb WAN ports.
I have been sent the Pro (WiFi & VPN router) and the Tunneler (WiFi VPN router) for this review. Because both models are very similar except that the Pro has more functionality, I will concentrate on examining the Pro, although I shall also perform speed tests using the Tunneler. As this has the same specs as the rest of the Anonabox line except the Pro, these tests should give us a good idea of how the other models perform.
First Impressions
The routers are well packaged, and come with a glossy and professionally laid-out Startup Guide. The first thing that struck me when opening the box was how small and light the actual routers are. Measuring 64mm x 44.5mm x 22.3mm (L X W X H) and weighing just 28 grams (1oz), these devices are truly portable (the Pro in fact weighed 31.5 grams by my measurements, but really is just quibbling).

First impressions were very favourable (lighter included to indicate scale)
Another fairly minor quibble is that Anonabox recommends you carry an Ethernet cable around when traveling in order to configure the router should a problem occur with the WiFi connection. I will just note that even a short Ethernet cable is likelier bulkier and heavier than the Anonabox itself…
The device is powered using a 1A USB cable.
Features
The Pro model claims to support the following features:
- Embedded Tor Client
- HMA VPN Integration
- Webserver (.onion hosting)
- WiFi Uplink and range extender
- USB file sharing
- Use any third party VPN service
Other models have a reduced feature set (Original and Fawkes have no VPN functionality, while Tunneler has no Tor functionality). Only the Pro features a USB 2.0 port for file sharing.
As we shall see, however, many of these features (proudly proclaimed on the website and product packaging) are not in fact supported, and may never be…
The Website
The Anonabox website looks very smart, and clearly explains the claimed features of Anonabox products. The FAQ is aimed at non-techies, and the support tab mainly links to .pdf copies of the setup guides included with the routers. I am sure this content will expand over time, and will hopefully provide documentation for at least some of the features that Anonabox advertises (see later).
Support
Live chat support is available during California office hours, but more technical queries had to be referred to Anonabox’s technical support staff, who contacted me the next day via email. A ticket system and email support are also available.
Unfortunately, what support I did receive left me unimpressed. I was mostly informed that advertised features were not available, and even the rough outline guides promised to me when I told staff that I was reviewing their product never arrived (probably because, as I found out later, no such guides exist in even rough form).
The Process
Basic setup
Before an Anonabox can be used, a number of preliminary setup tasks need to be performed using the web interface (over either WiFi or LAN cable):
- Set admin password for the router via a web interface
- Configure WFi (if used)
- Connect to the internet
- Configure VPN (if used)
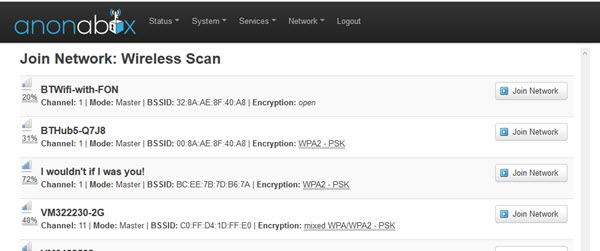
None of this is hard, and everything is well explained in the included Startup Guide, which also covers setting up Tor and VPN. I think this does, however, fall short of the claim made on the Anonabox website that “No configuration, installation or download needed.”
Anonabox uses a custom OpenWRT build for its firmware (and interface). This is no-doubt highly capable, but does mean that no instructions are available for configuring the router other than those supplied by Anonabox.
As we shall see, this becomes very problematic, because apart from the preconfigured Tor client and HMA VPN service, setting anything else up on the router is all but impossible without a degree in Linux and networking.
Tor setup
The Original, Fawkes, and Pro models have a Tor client built-in. Starting this up is super-easy – just go to Services -> Tor and Start Tor. It can take a couple of minutes for a Tor Connection to be established, but after that, away we go!
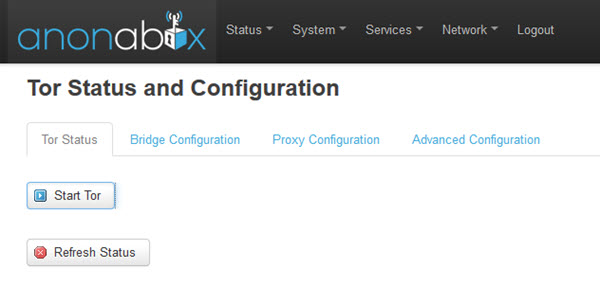
Unfortunately, a Tor connection does not persist if the device is powered off and then on again, and so needs to be manually started from within the web interface. This does detract a little from the plug-and-play functionality of the router, but is a fairly minor annoyance.
When Tor is started, all internet connections of all connected devices are routed through the Tor anonymity network (not just those of the Tor browser). It should be noted, however, that the Tor browser is a hardened environment designed to protect your privacy, and is therefore a much more secure way to access the internet than through an Anonabox.
When connected to the Tor network you can access Tor Hidden Services (.onion) websites. In theory (and as advertised) Tor routers can be configured as .onion servers, but this has not been pre-configured and no guides are available, making this “feature” effectively useless.
One of the few things that instructions are available for on the website to is how limit Tor connections to a specified country, which is very useful.
HMA! VPN setup
VPN models are preconfigured to connect to the Hide My Ass! (HMA!) VPN service using a built-in OpenVPN client. BestVPN has an HMA! review, but I will note that for a product whose very name suggests that it provides users with anonymity, Anonabox’s choice to partner with HMA! is frankly baffling, and is a decision that badly undermines our confidence in the company’s commitment to privacy.
Anyone who knows anything about the VPN industry will immediately recognise HMA! as being one of (if not the) worst providers when it comes to privacy. It is, for a start, based in the UK, and is therefore required to keep extensive logs about what its users get up to (a problem only likely to get worse when the upcoming Investigatory Powers Bill, aka the “Snoopers Charter”, comes to force).
HMA! is also one of the few VPN providers to be actually caught with its pants down, actively handing over internet records and personal details of one of its customers to the police (resulting in a prison term).
Basically, anyone who cares about privacy (i.e. the entire target market for these devices) should stay well clear of HMA!
Responding to my criticism over the use of HMA!, I was informed that,
“As to the privacy and trustworthiness of our VPN partners, we recognize that certain services are going to be better fits for different people. Again, this is why we are looking to expand our fully integrated offerings. I will point out that the intent of our product is to remain private and anonymous online, which all of our VPN partners are capable of offering. Log files and metadata retention is of biggest concern to users doing illicit activities because of the power a subpoena, or other government equivalent, can carry in demanding this information from the providers. We are not condoning illicit behavior.”
Uh... yeah... ok, anonymous my ASS (sorry for the pun)! Furthermore, according to our readers, HMA! blocks the accounts of users who receive DMCA-style notices for copyright infringement...
So with that out of the way, it has be said that using HMA! VPN on an Anonabox is very easy. Included in the box is an access code giving you 30 days free subscription to the Hide My Ass! Pro service (worth $11.52).
Simply visit a custom landing page, enter some basic details and the activation key, and ta da! You have an HMA! account. In the router’s web interface you can now go to Services -> Hide My Ass!, enter your username and password, choose a VPN server location , check enable, hit Save and Apply, and off you go!
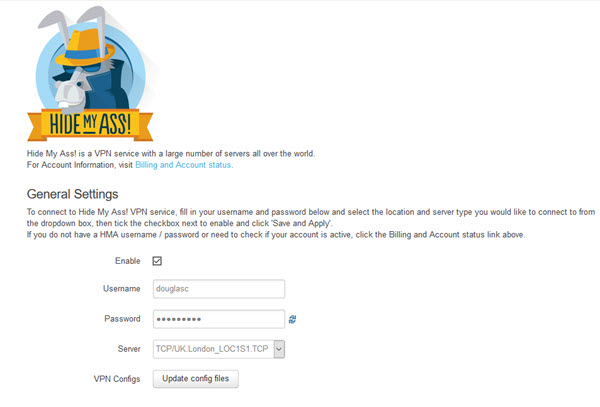
This is all very smooth, and unlike a Tor connection, will stay setup until you disable it (even if you turn the router off between uses). It is a crying shame, then, that the service you are connecting to is Hide My Ass!
VPN and Tor together
With the Pro model it is possible to use VPN and Tor together (in Tor through VPN configuration). This works well, and has all the pros and cons discussed here – namely that it does provide useful security and privacy benefits, but (as with using Tor on its own through an Anonabox), this not as secure as using the Tor Browser, and is generally considered not as advantageous as the VPN through Tor configuration.
It is also worth noting that using VPN and Tor together results in the combined speed hit of both (see speed results below).
Connecting to other VPN services
Ok… so HMA is a terrible VPN service from a privacy standpoint, but no problem! The blurb for the Pro proudly advertises that you can “use any other third party VPN service".
I was rather disconcerted, therefore, that the promised “3rd Party VPN Interface” does not exist, and when I asked support about how to configure a third party VPN I was told that,
“Regarding the current difficulty of configuring other VPN providers on our devices. While we provide OpenVPN on OpenWRT, which makes it in theory capable of being configured with most any VPN service, it is admittedly a very manual process currently. We are working on updates to the firmware that will help make integrations with additional VPN partners easier, but that doesn't solve any of the immediate issues.
We try as best as we can to address these on a one-on one-basis, unfortunately, with other development priorities and limited resources this is not always something we can support in a timely and adequate manner, which you're well aware of. We, like the consumer, are dependent upon the support documentation any given service provides, which in some cases is scant or nonexistent. There are simply instances where the resources required for us and/or the consumer to make a integration possible is not something that can be overcome.”
So no… it’s not really possible to use a service other than HMA! This was, to be honest, something of a wtf? moment for me, and if I had actually paid for these routers I would demand a full refund on this point alone.
Anonabox did inform me that,
“Addressing the varied preferences of VPN services, we have been working extensively behind the scenes to build additional partnerships for VPN integration into our GUI. This is a much more user friendly approach than providing manual configuration documentation as neither setup or use is especially straight forward. OFF the record, we have partnered with VyprVPN and SecureVPN and will be launching integrations beginning the first week of April.”
VyprVPN is a US-based company known for keeping extensive connection (metadata) logs and prohibiting P2P (so no thanks). Despite working in the VPN industry for years, I have never heard of SecureVPN, but it is a US-based company, and its privacy policy suggest that it keeps at least some connection logs…
USB filesharing
The Pro is fitted with a USB 2.0 port that Anonabox advertises on both its website and packaging can be used for USB filesharing (i.e. as a NSA drive, allowing you to share files between connected devices).
As the Anonabox uses a custom version of OpenWRT, this should certainly be possible, but unfortunately there are no currently no instructions on how to do so (and this is not supported by the existing interface). Unlike some other missing features, it does appear that Anonabox plans to address this issue in the near future,
“Guides will be made available for all users regarding filesharing; however, we've delayed this until mid April to take advantage of some ease-of-use features being released in the next firmware update. We advise filesharing through hosting and .Onion domain for privacy and security reasons which makes filesharing a rather complicated process at the moment. It can be done, and if you want a rough outline of what we'd compiled for this current firmware, I can send it, but it's by no means polished and would be greatly improved with the new firmware.”
WiFi Uplink and Range Extender
As a portable router, an Anonabox can extend your WiFi range simply by connecting to it. This can be done with both VPN and Tor services turned off.
I assumed, however, that the advertised “range extender” functionality referred to the possibility of using it being a “true” range extender i.e. that it could act as a repeater, boosting your primary router’s WiFi signal using the same network SSID. Unfortunately this is not the case,
“We have no documentation or plans to document use as a repeater.”
My disappointment here may be the result of over-high expectations on my part, rather than deliberately misleading advertising by Anonabox, but I do expect something that prominently advertises itself as a WiFi “range extender” to be capable of functioning as a repeater.
Performance
Pro
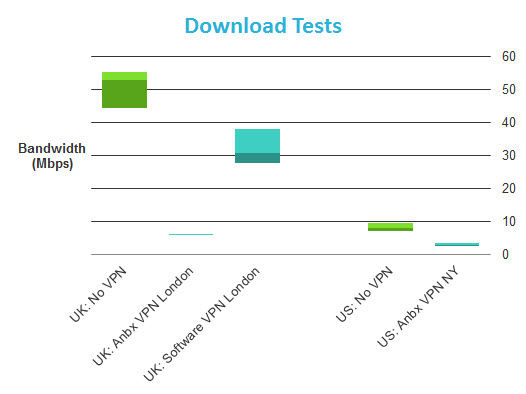
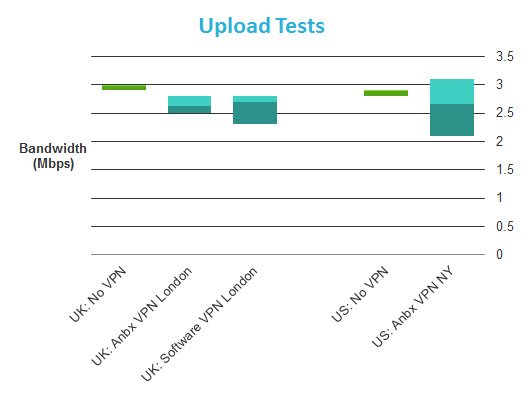
Speed tests were performed on a 50Mbps/3Mbps UK broadband connection. In addition to testing with no VPN and while connected to HMA! through the Anonabox, I also tested using the HMA! Windows software client (using the same VPN server). This was in order to separate any speed issues relating to the Anonabox (Anbx) hardware from those of the HMA! VPN service. All tests were performed using a WiFi connection in order to reflect normal usage.
HMA VPN
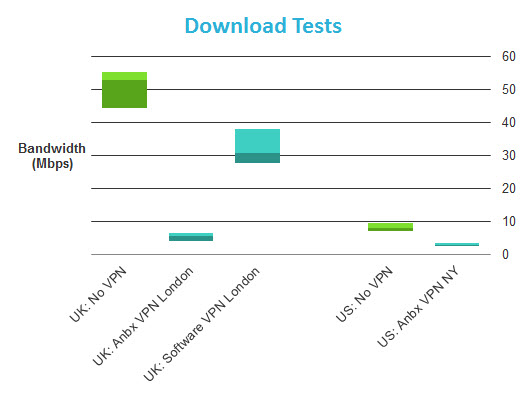
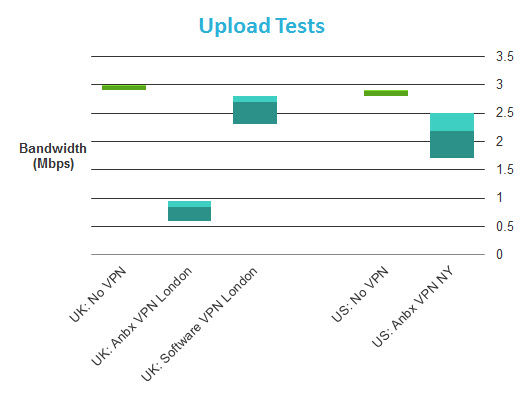
(Average HMA! software results for US tests were 24.3/2.4 Mbps)
So using an Anonobox connected to HMA! results in an 85-90% download speed loss! As we can see, this is not the fault of HMA!, which returned decent (if not specular results) when using its Windows client.
My initial reaction was to suspect the hardware of being not up the job of handling VPN encryption/decryption, but as we shall see from our Tuneler speed tests, which sports a much less powerful processor/RAM combo than the Pro, this may not be the case. The results are nevertheless disappointing.
I detected no DNS leaks while connected to HMA! using the Anonabox. WebRTC detection listed the HMA! server as my external IP address (good), but successfully detected my local IP address (bad). For more information about DNS leaks and WebRTC, please see here.
Tor
I was not, initially, going to perform speed tests using the Tor network, as the results would likely be too random to be useful. This is because when using Tor you connect to the internet via at least three random nodes which could run on servers of any speed, and be located anywhere in the world.
On reflection I decided that tests might prove useful to readers as a general guide to how much using Tor on an Anonobox will impact connection speeds, but please use caution when reading the results, and understand that most of the slowdown is a result of how Tor works, and is beyond the control of the Anonabox devs.
I refreshed the Tor circuit between each test, and used a UK test server. I did not, however, restrict which Tor nodes I could connect to, as I believe this best reflects normal Tor use and best practise. When testing Tor + VPN I used a London HMA! server.
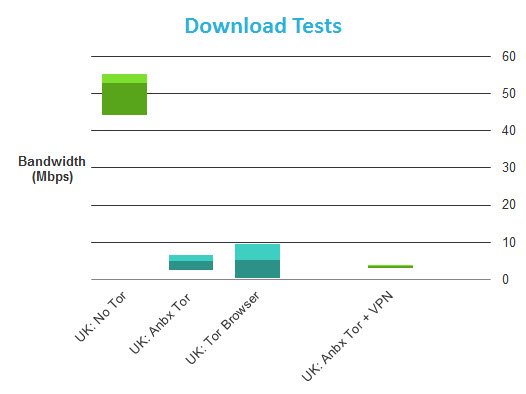
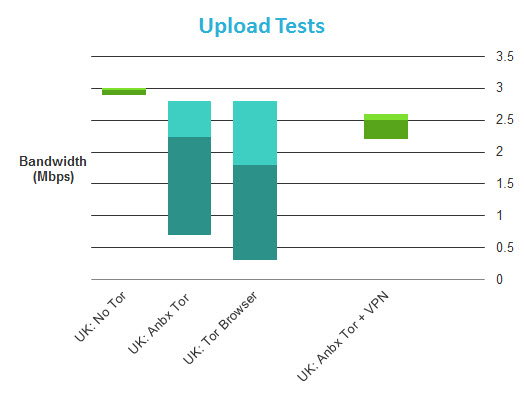
Average download speeds for the Tor Browser and Anonabox are very close, although the Tor Browser was able to hit much higher top speeds. This could indicate that the Anonabox processor struggles to cope with higher speeds, or could just be the vagaries of using Tor. Interestingly, combining Tor with VPN does not seem to slow things down much further.
Tunneler (HMA! VPN)
The Anonabox Tunneler uses a less powerful processor and has less RAM than the Pro, but has identical specs to the rest of the Anonabox line. These results should therefore be a good indicator of how the other Anonabox models perform. Setup is identical to that above.
(Average HMA! software results for US tests were 24.3/2.4 Mbps)
Interestingly, these results are very similar to those of the Pro. This suggests that the reason for these disappointing speeds across the range may be more complicated than simply having underpowered hardware.
As with the Pro, I detected no DNS leaks while connected to HMA! using the Anonabox Tunneler. WebRTC detection listed the HMA! server as my external IP address (good), but successfully detected my local IP address (bad).
Anonabox Review Conclusion
I liked
- Physical products are amazingly compact and lightweight
- Well packaged with great setup guides (but only cover very basic setup – not additional features)
- Setup is fairly straightforward
- Pretty much plug-and-play after setup
- Tor performance is ok
I wasn’t’ so sure about
- Support was of limited help at best (even after I revealed that I was reviewing its product)
- No support for USB filesharing on Pro as advertised (but at least this appears to be coming)
- Tor connection works fine, but is not as secure as using the Tor Browser
- Cannot be used as a repeater (despite advertised “range extender” functionality)
- 802.11n wireless standard is last generation
I Hated
- HMA! is the worst choice of partner possible in terms of privacy (and choice of other future VPN partners seems almost as bad)
- Not possible to use with other VPN providers (despite advertising to the contrary)
- Terrible VPN download speeds
- Advertised .Onion hosting not supported (at least for now)
As a VPN router, the Anonabox should probably be avoided at all costs. The bizarre decision to partner with HMA! means that using an Anonabox for VPN is little more private than not using one at all. This might not have been such a problem if you could simply use a provider of your choice, but much to my surprise (or is that shock?), this is to all intents and purposes not possible (despite being a prominently advertised feature, and the only reason I might have considered buying this device).
The fact that other advertised features are not yet available or are much more limited than the advertising suggests does not help the situation.
As a simple Tor router (its original purpose), the Anonabox fares better. Connecting to the Tor network is easy and performance is fine. The pink elephant in the room, however, is that accessing the Tor network is much secure via the hardened Tor Browser.
Why anyone would want to access Tor in a less secure way baffles me, which makes it very difficult to recommend this product even on this level. Despite this problem, when it comes to Tor functionality, the Anonabox does do what it says on the er… box.
0 User Reviews
Leave a Review
Thanks for your review!
9 Comments
Write Your Own Comment
Your comment has been sent to the queue. It will appear shortly.

Osiris
Douglas Crawford replied to Osiris
Lou
Sean Murphy
Douglas Crawford replied to Sean Murphy
Sean Murphy replied to Douglas Crawford
Craig @ UnlockWorldTV