That any volunteer can run a Tor exit node, and that such a volunteer might have malicious intent, has long been known as a potential weakness of the Tor anonymity network. Fortunately the network is set up in such a way, with data being relayed between a number of different ‘nodes’ between the user and the exit node, that the potential for harm is minimized.
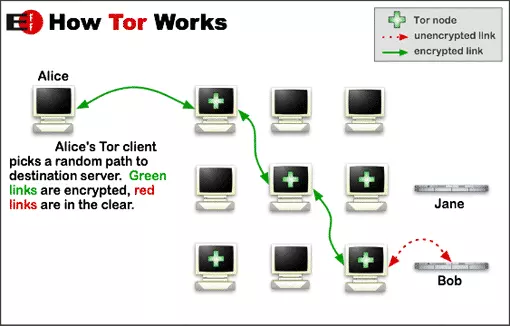
It has nevertheless always been generally presumed that some people run such ‘spoiled onion’ nodes, which can see all traffic entering and exiting the internet through them, with NSA style spying agencies enjoying particular suspicion.
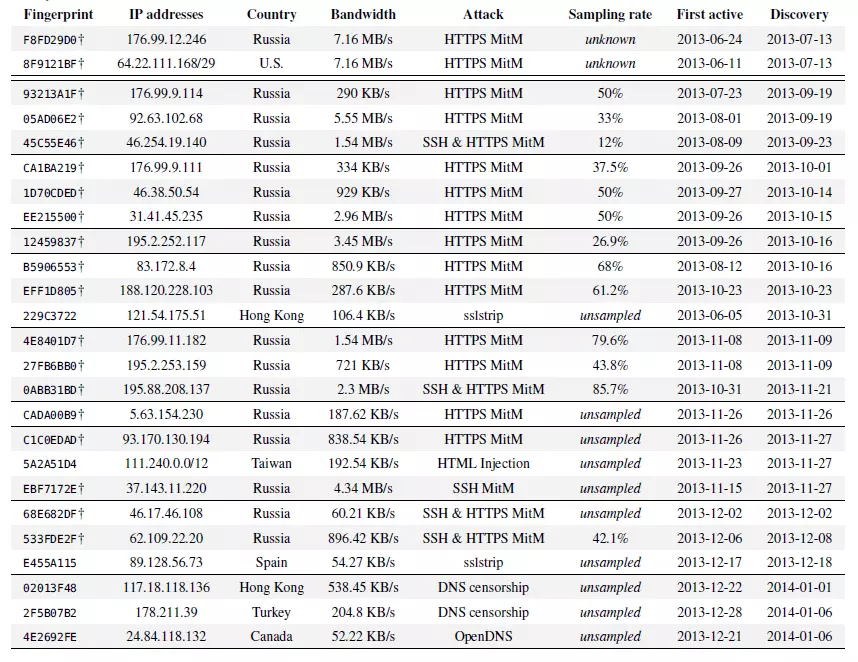
A new paper entitled ‘Spoiled Onions: Exposing Malicious Tor Exit Relays’ broadly confirms the findings an older paper, ‘Detecting Traffic Snooping in Tor Using Decoys’ in finding that 25 of the roughly 1000 Tor exit nodes operating at any one time have been misconfigured, or are outright malicious. Interestingly, the paper finds it doubtful that most people’s prime suspect for this, the NSA, is to blame.
Of the 25 servers identified, two redirected traffic away for porn sites - it is thought these are nodes run in counties with restrictive censorship laws, one suffered from what the researchers describe as a configuration error in the OpenDNS server, and the other twenty-two ran man-in-the-middle (MitM) attacks using Moxie Marlinspike's sslstrip method.
‘All the remaining relays engaged in HTTPS and/or SSH MitM attacks. Upon establishing a connection to the decoy destination, these relays exchanged the destination’s certificate with their own, self-signed version. Since these certificates were not issued by a trusted authority contained in TorBrowser’s certificate store, a user falling prey to such a MitM attack would be redirected to the about:certerror warning page.’
Perhaps the most interesting thing about the results is that the attacker on nineteen of these servers appears to be the same person (or group of people), as can be determined by the fact that almost identical forged certificates were used, that almost all the servers used a very outdated version of Tor (version 0.2.2.37), and that all but one of them was located on the same VPS network in Russia.
As for the NSA, co-writer of the report Philipp Winter observed that it would have no need for such a crude attack as running malicious nodes,
‘Organizations like the NSA have read/write access to large parts of the Internet backbone. They simply do not need to run Tor relays. We believe that the attacks we discovered are mostly done by independent individuals who want to experiment.’
