Every modern processor made by Intel contains a backdoor known as the Intel Management Engine (IME). This is an isolated and protected coprocessor that is embedded in all Intel chipsets that are newer than the first quarter of 2008.
This includes all desktops, servers, ultrabooks, tablets, and laptops with the Intel Core vPro processor family. It includes the Intel Core i3, i5, i7, and Intel Xeon processor E3-1200 product family.
The Intel Management Engine is Really Rather Scary
This closed source non-auditable subsystem can:
- Access all areas of your computer's memory, without the CPU’s knowledge.
- Access every peripheral attached to your computer.
- Set up a TCP/IP server on your network interface that can send and receive traffic, regardless of whether the OS is running a firewall or not.
- Run remotely even when your computer is turned off.
- Enable a remote user to power on, power off, view information about, and otherwise manage your PC.
- ME firmware versions 4.0 and later (Intel 4 Series and later chipsets) include a DRM application called "Protected Audio Video Path" (PAVP). This allows a remote user to access everything that is shown on your screen.
If your PC uses an Intel chip, then it does not matter which operating system you run. As Brian Benchoff notes in a Hackady blog post,
“Own the ME and you own the computer.”
Terrifying as this all is, it gets worse. The AMT application (see below) has known vulnerabilities, which have already been exploited to develop rootkits and keyloggers, and to covertly gain encrypted access to the management features of a PC. As Libreboot notes in its FAQ,
“In summary, the Intel Management Engine and its applications are a backdoor with total access to and control over the rest of the PC. The ME is a threat to freedom, security, and privacy, and the libreboot project strongly recommends avoiding it entirely.”
Until now, the only way to do this has been to avoid all generations of Intel hardware newer than ten years old! Unfortunately, opting to use a non-Intel processor does not get you very far…
Non-Intel Chips are Not Safe Either!
All post-2013 AMD chips contain a Platform Security Processor (PSP). Implementation of this is very different from that of Intel’s IME, but it does a very similar thing. It also comes with all of the same basic security and freedom issues as the IM.
Android and iOS devices, on the other hand, all ship with an integrated proprietary chip known as a baseband processor. It is well known in security circles that this can effectively act as a backdoor…
So What Exactly is the Intel Management Engine?
The IME is the hardware component of Intel’s Active Management Technology (AMT). It is designed to allow system administrators to remote-access PCs in order to monitor, maintain, update, upgrade, and repair them.
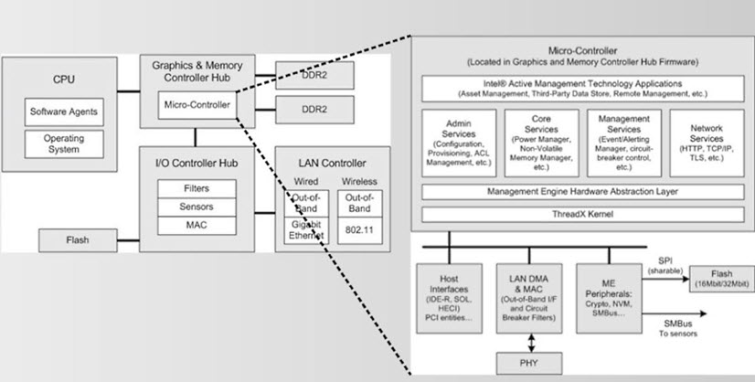
Other than its capabilities, very little is known about the IME. This is thanks to the fact that it is closed source and secured with an RSA-2048 key. As previously noted, the AMT application has known vulnerabilities, although the IME hardware component remains secure… for now. As Benchoff notes,
“There are no known vulnerabilities in the ME to exploit right now: we’re all locked out of the ME. But that is security through obscurity. Once the ME falls, everything with an Intel chip will fall. It is, by far, the scariest security threat today, and it’s one that’s made even worse by our own ignorance of how the ME works.”
With regard to criminal hackers, it is very much a case of when, not if the hardware is cracked. Furthermore, criminal hackers are only one threat to be concerned about.
System administrators gain access to AMT features using cryptographic keys. These could be stolen or handed over to the authorities on receipt of a subpoena, court order, national security letter, or suchlike.
Indeed, given what we know about its close connections with the US technology industry, it would be fair to assume that Intel has simply provided the NSA with the certificates and cryptographic keys necessary to access any and every chip it produces. Again, this is very scary!
How Do I Disable the IM?
Until very recently, it has been impossible to disable the IM on most systems that the use Intel Core 2 series of Intel chips or newer (2006 and onwards). Any attempt to disable the ME firmware on a chip that includes the IME would result in the system refusing to boot or shutting down shortly after booting.
A technique was developed for removing the ME from GM45 chipsets (Core 2 Duo, Core 2 Extreme, Celeron M). It worked, however, because the ME was located on a chip separate from the northbridge.
This technique does not work for Core i3/i5/i7 processors, as the ME is integrated to the northbridge. It is possible to disable key parts of the ME on these chips, but this has always resulted in the PC shutting down after 30 minutes, when the ME’s boot ROM (stored in an SPI Flash) failed to find a valid Intel signature.
Just recently, however, researcher Trammell Hudson found that if he erased the first page of the ME region (i.e. 'the first 4KB of its region (0x3000, starts with "$FPT"') of his ThinkPad x230, it did not shut down after 30 minutes.
This discovery led other researchers (Nicola Corna and Frederico Amedeo Izzo) to write a script that takes advantage of this exploit. Note that this script does not completely remove the ME per se, but it does in practical terms disable it. Benchoff observes,
“Effectively, ME still thinks it’s running, but it doesn’t actually do anything.”
The script is known to work on Sandy Bridge and Ivy Bridge processors, and should work on Skylake processors. It may work and Haswell and Broadwell processors, but this has not been tested.
Unfortunately, using this script requires serious tech chops. It requires the use of a Beaglebone, an SOIC-8 chip clip, and some loose wires. It also requires a lot of nerve, as there is a serious risk of bricking your processor!
Nevertheless, this is an important development that allows those determined enough to (effectively) remove the backdoor that exists in pretty much every modern processor.
