For many years, there has been a general assumption that Apple Mac computers and laptops are more secure and less vulnerable to attack by cybercriminals. Now, however, more and more evidence is emerging that those days are over.
Macs are expensive, and are generally thought of as a more ‘professional’ option than other computers. Hackers, who more often than not target people in order to extract a profit, have figured this out. This has led to an explosion in the availability of malware for Macs.
In January of this year, one particular Mac-focused variant called Fruitfly was discovered in the wild. Fruitfly can give hackers full access to a Mac computer’s files and the ability to watch screens and the built-in webcam. It also provides full executable control over the machine.
To fix the problem, Apple issued an update not long after Fruitfly was reported. However, evidence has now emerged that hackers have new versions of Fruitfly-like malware, and are actively targeting people’s machines.
What’s more, according to Patrick Wardle, a security researcher at Synack, the newer versions of the malware alert their cyber-controller when the Mac owner is using his or her machine - in order to help the cybercriminal avoid detection.
Perhaps most frightening of all is Wardle’s assertion that there is even better malware for Macs already out in the wild:
"[Fruitfly] isn't the most sophisticated Mac malware," he recently commented.

Plenty of Mac Vulnerabilities
In May, a trojan for Mac that attacks a vulnerability in the popular open-source video transcoder, HandBrake, was discovered. Proton.B is a virus for OS X that was disseminated using a hacked mirror server of the official HandBrake site. Like most remote access trojans (RATs) it communicates with a Command & Control (C&C) server under the dominion of the cybercriminal.
It gives the hacker root-access privileges, which means keylogging, uploading and downloading files, taking screenshots, full access to the webcam, and Secure Shell (SSH) protocol connectivity, as well as Virtual Network Computing connectivity via the Remote Frame Buffer (RFB) protocol. This troubling RAT wasfoundbeing sold on hacking forums in Russia, promising:
"Professional FUD surveillance and control solution, with which you can do almost everything with [a] target's Mac."
In June, researchers at Fortinet discovered another form of ransomware for Mac called OSX/MacRansom. As with other forms of ransomware, the vicious malware uses encryption (on this occasion an a symmetric cryptographic algorithm), in order to lock up people’s files.
Although the malware isn’t particularly sophisticated, it is quite worrying, because it encrypts all files over 8 Mb in size using a randomly generated key that it doesn’t communicate to the attacker. As such, it would appear that once files are encrypted using MacRansom they are lost forever (save using a brute force attack to decrypt them).
SurelyWindows Has a Much Bigger Problem?
This is a common misconception that needs to be put to bed.Mac owners who are relying on Mac’s reputation as a stable platform to avoid infection need to wake up and start taking precautions. In their blog entitled 'MacRansom: Offered as Ransomware as a Service,' Rommel Joven and Wayne Chin Yick Low, point out that in reality, Mac is just as vulnerable as its Windows counterpart:
"Many Mac OS users might assume that their computer is exempt from things like ransomware attacks and think that their system is somehow essentially "secure.” It is true that it’s less likely for a Mac OS user to be attacked or infected by malware than a Windows user, but this has nothing to do with the level of vulnerability in the operating system. It is largely caused by the fact that over 90% of personal computers run on Microsoft Windows and only around 6% on Apple Mac OS.”
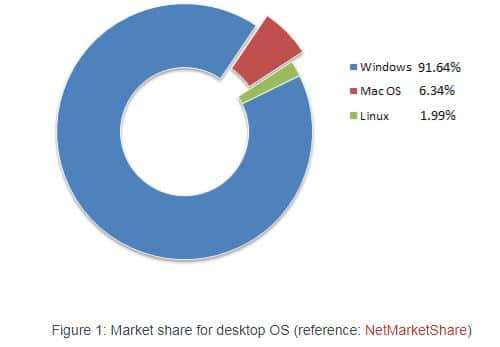
With so few computers running Mac compared to Windows, it is no wonder that there is a skewed perception of Mac’s vulnerabilities. For many years, the fact that sofew computers ran OS X actually helped to protect those users. After all, hackers whowrite malware do so because they want to make money - and with 90% of people using Windows machines, writing malware for Windows would lead to much larger infection rates and therefore profits.
Changing Times
Now, hackers have opened their eyes to the larger sums of money they can extract from professionals who rely on MacBooks. Add to that revelations like Wikileaks' Vault 7 (about government agencies using malware to target devices), and you start to realize that there is more than enough reason to protect a Mac desktop, laptop, or mobile device.

In fact, Apple has only just issued updates for iOS (10.3.3) and OS X (10.12.6)devices, which fix acritical security flawcalled Broadpwn. That vulnerability allows hackers to "execute arbitrary code on the Wi-Fi chip" in Broadcom's Wi-Fi chipsets, allowing cybercriminals to take control of infected machines via the WiFi chip on the motherboard.
If you haven’t downloaded the most recent version of your device's operating system, it is worth remembering that (like most software developers) Apple regularly issues fixes for any vulnerabilities that are discovered. For this reason, it is essential to always be on the lookout for the most recent version of Apple OS.
The Broadpwn vulnerability was also detected on Android devices (ranging from HTC, LG, and Nexus, to the entire range of flagship Samsung models). Google issued a fix on 1 July. Thus if you are an Android user you should update your version of the Android platform.
What Else Can I Do?
Other than getting the latest version of OS X or iOS, it is important to also get a good script debugger. Two popular tools (that both work to protect against the aforementioned MacRansom attack, for example) areBlockBlockandRansomWhere?
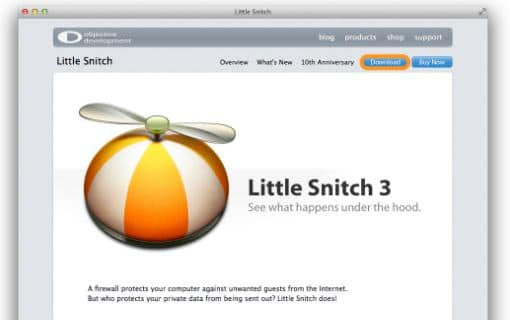
There are also firewalls on the market that alert Mac users when their computer attempts to communicate with a C&C server (as is the case in the previously mentioned Proton.B exploit). Hands Off and Little Snitch are both very popular and do the job extremely well. In fact, it is worth noting that Little Snitch was found tosuccessfullywork against Proton.B - a testament to its efficacy.
In addition, consumers are advised to get a good antivirus for Mac such as Bitdefender, if they want to be absolutely sure to keep their expensive Mac secure.
My final recommendation is that (because there is no perfect way to protect against newly emerging ransomware variants) consumers should remember to effectively backup their data. Regular backups of important files provide a way to retrieve information if the worst does happen. In addition, taking extreme precaution when opening files from unidentified sources or developers is always advisable.
Fruitfly
As for Fruitfly, Wardle was able to discover several backup domains that were hardcoded into the malware. Realizing that some of those domains were still available, Wardle registered those domains in order to discover infected IP addresses. Within days of registering the domains, he discovered 400 IP addresses of Mac computers (mainly in the US) that had been infected. He commented,
"This shows that there are people who are sick in the head who are attacking everyday Mac users for insidious goals.
A lot of Mac users are overconfident in the security of their Mac. [The discovery] just goes to reiterate to everyday users that there are people out there trying to hack their computers."
Opinions are the writer's own.
Title image credit: mama_mia/Shutterstock.com
Image credits: TheaDesign/Shutterstock.com, Kaspars Grinvalds/Shutterstock.com
