SoftEther is a free and open-source VPN client and VPN server software developed as part of a master's thesis research at the University of Tsukuba in Japan.
By default, SoftEther uses the SoftEther protocol - an SSL VPN protocol that its developers claim includes several improvements over OpenVPN (also an SSL VPN protocol).
SoftEther servers can accept connections from a wide range of VPN protocols, so use of the SoftEther client is not necessary. You can, for example, connect to a SoftEther server using the L2TP/IPsec client built into most modern operating systems, or via any OpenVPN client.
In this guide, we show you how to set up your own SoftEther VPN service.
A home VPN setup
SoftEther supports many VPN configurations, including remote access of your LAN resources over a VPN connection. This guide, however, covers how to turn your home PC into a personal VPN server.
Running a personal VPN server is great for bypassing censorship when abroad and for ensuring privacy when using public WiFi hotspots. It's also a great way to access your regular streaming services, as you will do so using your own home IP address which will not be blocked, as the IPs belonging to many commercial VPN services are.
The main downside of running your own VPN server is that it does not hide your real IP address from the outside world. Running your own VPN server (whether at home or using rented server space) therefore loses some key privacy benefits of using a third-party VPN service.
In Windows
The big advantage of setting up a home SoftEther VPN server in Windows is that the SoftEther VPN server software for Windows features a user-friendly GUI interface. The Linux and macOS server software is command-line only and must first be compiled from the source.

For this reason, even macOS and Linux users may prefer to set up a SoftEther VPN server inside a Windows Virtual Machine (VM) using software such as the free Oracle VM VirtualBox.
If, however, you prefer to set up a much more lightweight VPN server, if you want to set up a VPN on rented remote server space or if you just have a thing for the command-line, then keep your eyes open for our upcoming guide on How to set up a SoftEther VPN server in Linux.
How to set up a home SoftEther VPN server in Windows
-
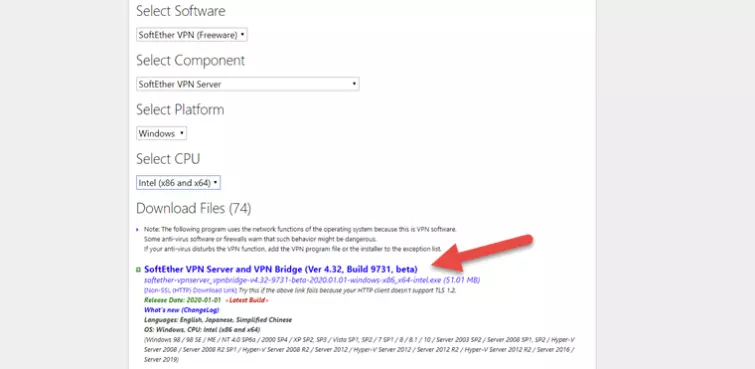
Download and install the software. Visit the SoftEther Download Center and select the software we’ll need using the drop-down menus. The Component is SoftEther VPN Server, and the Platform is Windows. Intel (x86 and x96) is the only CPU option available for Windows.
![SoftEther Download]()
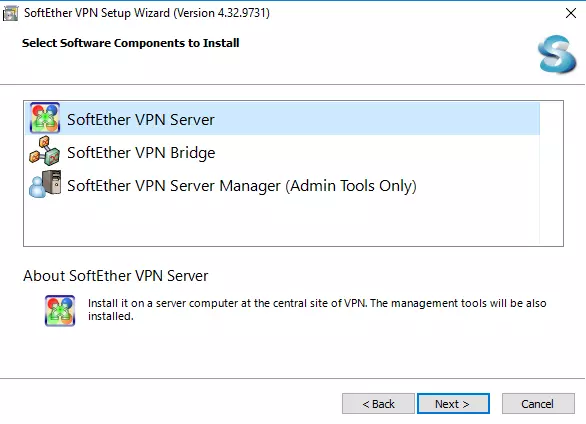
Download the latest version of the software and install it in the usual way. The only component you need to select for our current purpose is SoftEther Server.
![SoftEther Setup Wizard]()
-
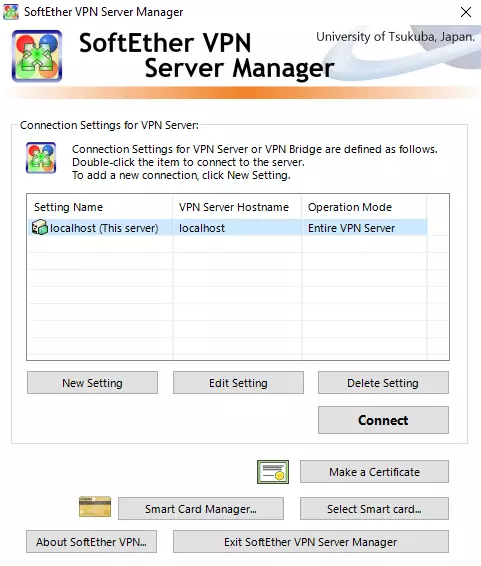
Once the software is installed, the Server Manager window will open. Select localhost (This server) and hit Connect.
![SoftEther VPN Server Manager]()
You will be prompted to create a new Administrator password for localhost.
-
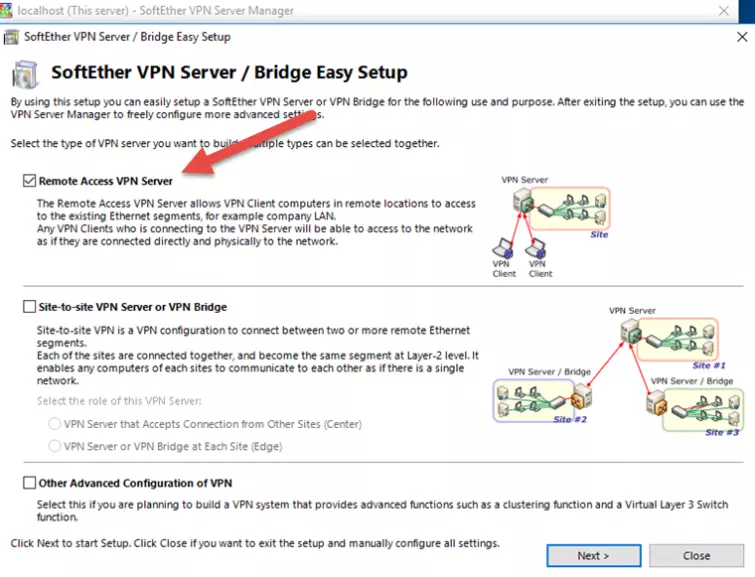
Select the Remote Access Server checkbox then click Next.
![SoftEther VPN Remote Access]()
-
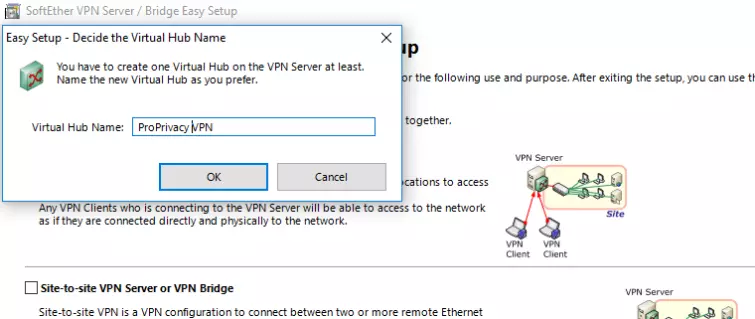
Name your new Virtual Hub anything you like, then click OK.
![SoftEtherVPN Virtual Hub]()
-
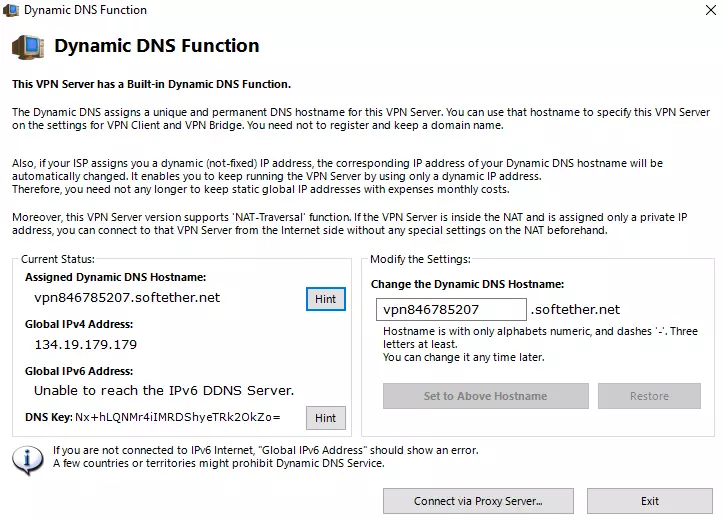
The Dynamic DNS Function dialog window will appear. Dynamic DNS ensures your VPN server can be reached behind firewalls or if your ISP assigned you a dynamic IP address.
![VPN SoftEther DNS]()
Just stick with the default settings and Exit, although you may want to make a note of the Global IPv4 and Global IPv4 Address settings as they are not easy to find later.
-
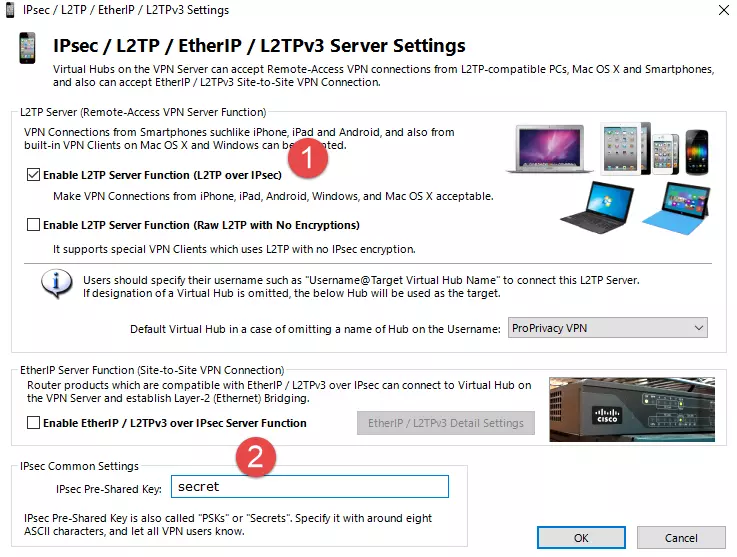
On the next screen, Enable L2TP Server Function (L2TP over IPsec) and choose a shared secret. Make sure you pick a strong one, as this secures your network for L2TP/IPsec connections. Click OK.
![SoftEther VPN IPsec L2TP]()
-
We are not using VPN Azure Cloud here, so check the Disable VPN Azure radio button and then click OK.
![SoftEther VPN Azure Cloud]()
-
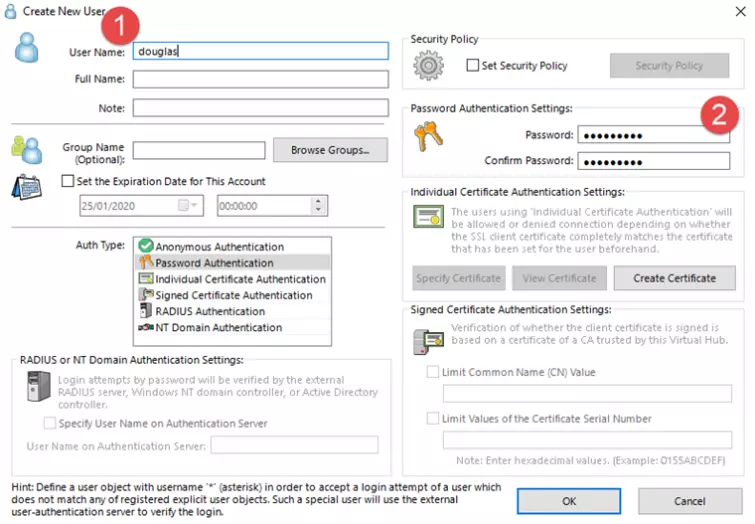
Next up is the VPN Easy Setup Tasks window. Clicking the Create Users button.
![SoftEther VPN Create New User]()
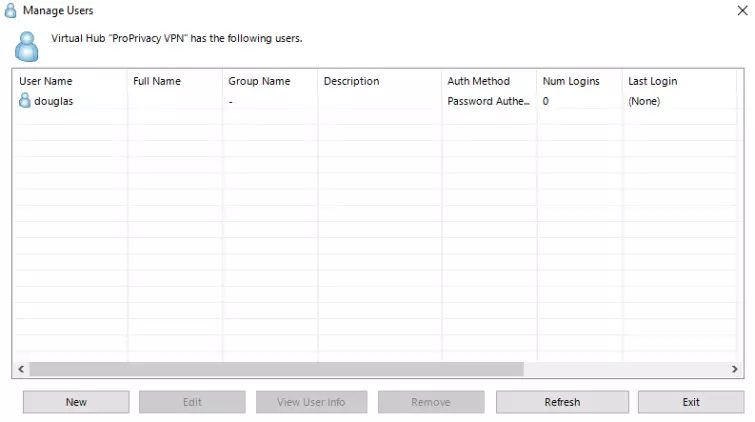
Give your new user a username and password. You can add additional details, create groups, and more, but they are optional. Leave Auth type at its default "Password Authentication” and hit OK.
![SoftEther VPN Manage Users]()
This will take you to Manage Users hub. You can add as many users as you like or skip this step for now and come back to it later. Press Exit when you’re done. You can also Close the VPN Easy Setup Tasks window as a Local Bridge is not required for simple VPN access.
-
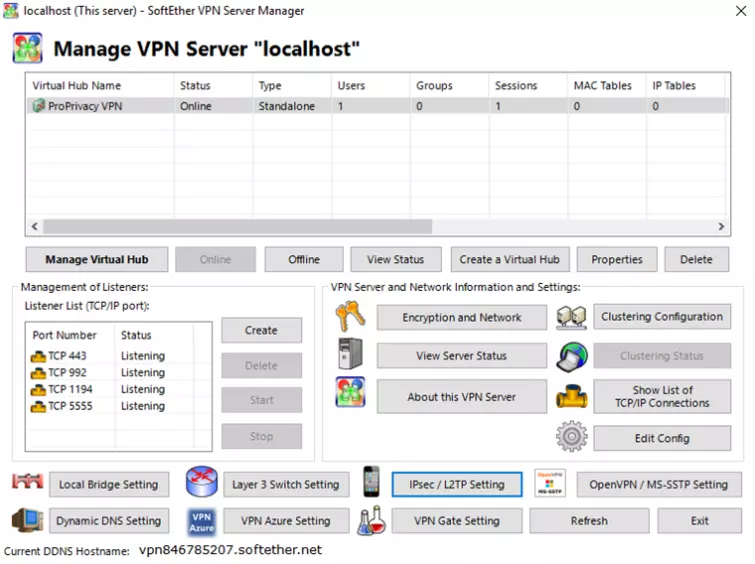
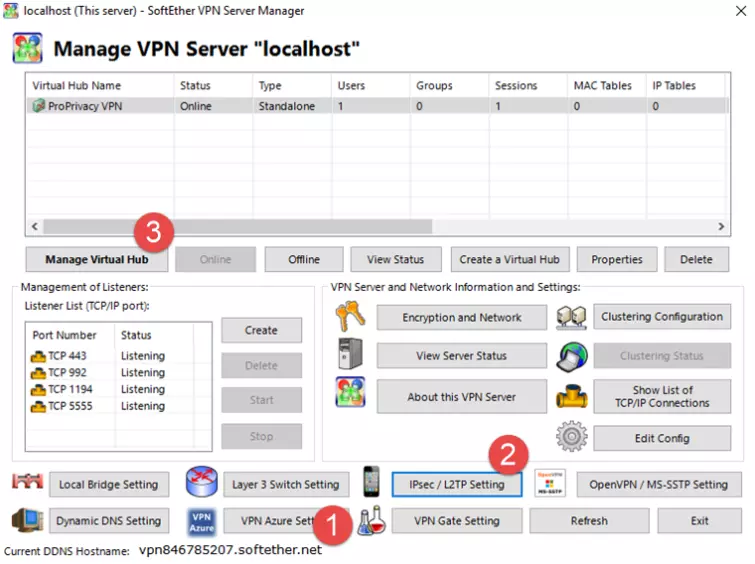
This brings you to the Manage VPN Server "localhost” window. Note that you can access this Window by launching the SoftEther VPN Server Manager (see Step 2) and selecting localhost -> Connect.
![SoftEther VPN Localhost]()
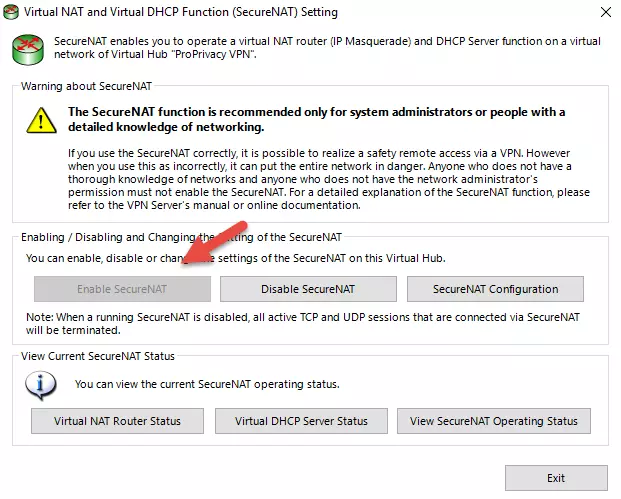
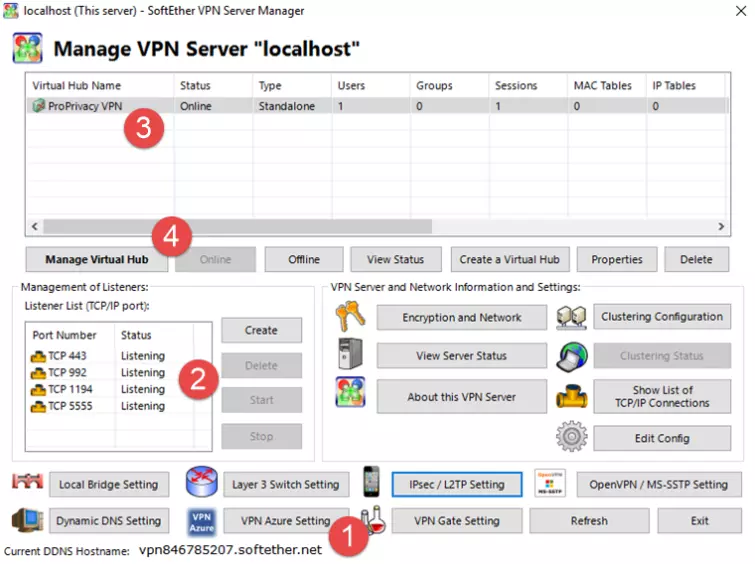
The next step is optional but recommended. It ensures that connected users can use the VPN as an access point for the internet but cannot access your local LAN network.
Click Manage Virtual Hub -> Virtual NAT and Virtual DHCP (SecureNAT) -> Enable SecureNAT.
![SoftEther NAT]()
And that’s it. Your VPN server is now ready.
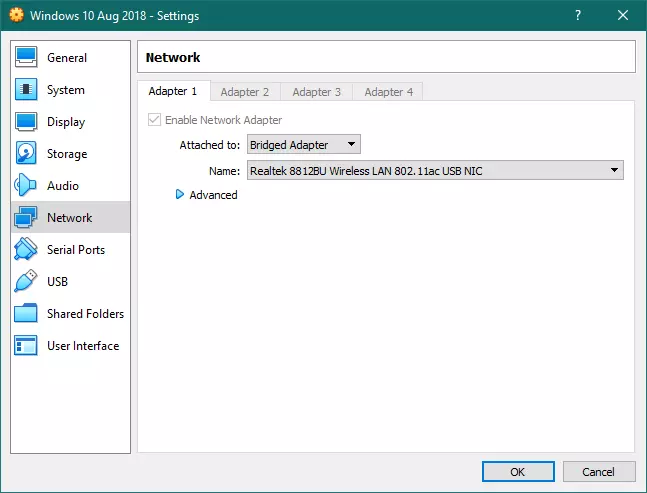
Tip for VM users
If setting up a VPN server inside a Virtual Machine, you will need to change the VM’s Network settings to Bridged Adapter -> adapter used by host machine to access the internet.
Set up VPN Clients
We look at setting up VPN clients for your new SoftEther network in How to install and configure SoftEther VPN on your device. In order to connect to your SoftEther server, you will need to supply users with the necessary settings.
SoftEther connections
People using the Windows SoftEther client to your server will need to know:
-
Host name or host server IP address (see Step 5 above). Note that we had more luck establishing connections using the host IP address.
-
Port number. Port 443 is the default used by the SoftEther Windows, but your server can accept incoming connections on any of the listed ports.
-
Virtual Hub Name
All this information (except host IP address) is available in the Manage VPN Server "localhost” window.
-
Username and password. These can be managed by going to Manage Virtual Hub -> Manage Users (as per Step 8 above).
![VPN SoftEther Manager Server]()
Those using the SoftEther command-line utility (vpncmd) will also need to know the name of the vpn interface ("VPN” by default).
L2TP/IPsec connections
L2TP/IPec is the officially recommended way for all non-Windows users to connect to SoftEther servers. Anyone that does will need to know:
-
Host name or host server IP address (see Step 5 above). Note that we had more luck establishing connections using the host IP address.
-
IPSec Secret / Pre-Shared keys (PSK).
All this information (except host IP address) is available in the Manage VPN Server "localhost” window.
-
Username and password. These can be managed by going to Manage Virtual Hub -> Manage Users (as per Step 8 above).
![SoftEther VPN Server Manager]()
Note that Android users should also add "0.0.0.0/0" to the "Forwarding routes" field in their L2TP/IPSec settings.
OpenVPN connections
You will need to generate at least one.ovpn file, which you must distribute to each user.
To do this, go back to the Manage VPN Server "localhost” window -> OpenVPN /MS-SSTP settings -> Generate a Sample Configuration File for OpenVPN clients.
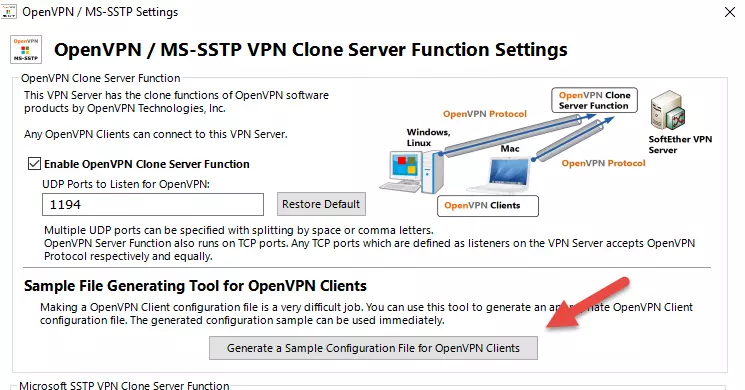
Open the generated ZIP file and extract the xxxx.remote_access_l3.ovpn file. The generated ZIP file also contains a readme document with advice on how to further configure the.ovpn file should you wish to.
You can, for example, send each user a personalized.ovpn config file with their username and password pre-configured so they don’t need to enter these manually each time they connect to your VPN server.
Users will also need a Username and password. These can be managed by going to Manage Virtual Hub -> Manage Users (as per Step 8 above).