For all the internet's merits, one of its major pitfalls is the ease at which scams and fraud can be committed.
There are so many different types it's vital you get clued up before heading online because they're becoming more convincing by the day.
This guide will show you how to identify a fake website by reading the URL, so you don't fall for the scammer's tricks.
What is a URL?
Every website has a Uniform Resource Locator, acronymized to URL. This is a unique identifier for the page, and every website's URL is different; it's sometimes called a web address for this reason.
URLs, when you type them into the address bar, command whatever browser you're using to source that specific page. Although every website has an IP address, this is just a sequence of numbers and it would be impossible to remember even one or two addresses, so URLs help give these sites much more relevant signifiers.
Before you continue reading...
All the URLs in this article (apart from the ones in pictures) have been created/invented to make some sort of point about URL scamming. We have to do this, or else showing what to watch out for would prove confusing. Although none of the URLs in this article should be fraudulent or lead you to scammers – they are just examples made up on the spot – it is still advised to not type any of them into your address bar as they are not actual web addresses. Legitimate URLs used are labeled.
Breaking down a URL: four sections
Before discussing how scammers utilize URLs, it's useful to understand their constituent parts. This will allow you to spot a fake website before visiting it. Let's take a basic, legitimate URL as an example:
https://www.bbc.co.uk/sport/football
| https:// – This is the 'scheme', which dictates the protocol the request is made across. Usually, this is either HTTP or HTTPS – the one with the 'S' is the secure version. There are others too, such as file-transferring protocols like 'ftp:' |
| www. – stands for 'World Wide Web'. This is a URL prefix that has always been used for years and still forms part of URLs. Nowadays, it's entirely superfluous – you don't even need it. |
| bbc – This is the second-level domain name. This is the website's name' and is the part of the URL used to identify which brand's website it is. |
| .co.uk – This is the top-level domain. It signifies what type of entity the website belongs to. In this case, it shows the site is based in the United Kingdom (UK). The 'co' is an abbreviation of commercial. |
| /sport/football – this is the 'subdirectory' part of the URL (and in this case, sub-subdirectory). It lets visitors know which part or page of the website they are on. Typing in '/sport' on the end of the BBC's main web address will always take you to the BBC's Sport page. |
How to identify fake URLs
Fake URLs are a vital component of 'phishing' – a scam that involves fraudulently obtaining a person's data by posing a legitimate, trustworthy entity. This is often referred to as 'URL spoofing'. Criminals will go after login details and financial information or attempt to install malware on the device.
URL scams appear in any part of a person's digital world where they can receive the information they haven't consciously requested: social media apps, forums, email accounts, text messages and, of course, browser search suggestions.
There are several ways scammers utilize URLs to kick off their insidious activities, so it's good to know what to look for. The first two are more commonly found in emails and on social media, the second two in browsers.
Shortened URLs
One widely-used way to spoof URLs is to shorten them. Shortened URLs are a way to create a simpler URL that is still unique, and there are sites like Tinyurl and Bitly that do this for customers. Google has a great example here:

Shortened URLs will usually include the address of the shortening site used, like bit.ly. They became much more popular after Twitter emerged in the early 2000s with their Tweet character limit – normal-sized URLs took up too much space.
This method is expedient for scammers largely because URL content filters don't recognize the link, and it can thus bypass the filter easily. Importantly, shortened URLs often don't 'look' fraudulent to both untrained eyes and those well-versed in online scams – so they can target anyone.
These types of URLs may be included on the landing pages of other sites, or appear in scam emails sent to your email address as well as social media platforms.
Most people who use the internet regularly will click shortened URLs every day, making them all the more perfect for bad-faith actors.
Fake buttons
One other way to spoof a URL is to hide it in a button inside an email or on a website – 'book now' buttons are often used to do this in scam airline emails.
Sometimes just clicking on one of these links can be enough to ping some malware into your device, but often they take you to a landing page designed to look indistinguishable from the real thing and try to coerce you into clicking more. Treat buttons on emails and sites you don't recognize with extreme caution!
Typosquatting
Some scammers will take over domains that are only one or two letters different to a popular website thousands of people will likely be trying to reach on a daily basis. Essentially, the scammers are looking to target the people who type in the domain incorrectly and get directed to their page instead. 'www.sainsbury.co.uk' instead of 'www.sainsburys.co.uk', for example.
This tactic is commonly called Typosquatting or brand hijacking. There are various tactics scammers use for this – spelling the brand name with a typo is one, or a common foreign language spelling of the same word, or adding in a new piece of punctuation. However, there are also cases of people doing this with the top-level domain part of the URL – .com is replaced with .cm, for example.
Unfortunately, non-Latin characters can be used in homographic URLs, rendering spotting scam websites a more difficult process than beforehand. Some non-Latin letters are extremely similar to their Latin counterparts, so look closely.
Combosquatting
An offshoot of the typosquatting method is 'combosquatting', which involves taking a related, legitimate-looking word and adding it to a genuine URL. So, using the example above, instead of 'www.bbc.co.uk/sport' it might be edited to read 'www.bbc-TV.co.uk/sport'. Sometimes this is used to convey a sense of urgency.
Below is an example of some real, malicious combosquatting domains found by Georgia Tech School of Electrical and Computer Engineering in 2017:
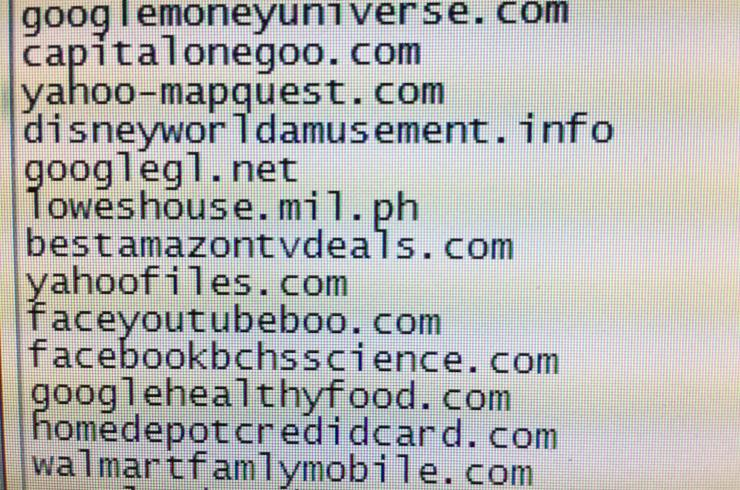
Combosquatting functions in much the same way as typosquatting, but if anything is harder to spot, especially if you're not terribly familiar with a given site. According to Georgia Tech, between 2011 and 2016, there were 2.7 million combosquatting domains found for the 268 most popular trademarks.
It's vital to remember that very few brands have websites with URLs that stray from the exact spelling of their brand name. For example, news channel CNN is not in control of any URLs that read 'www.cnn-reporting.com' – in reality it has been, and likely always will be, www.cnn.com.
Precautionary measures
There are also some simple precautions you can take and some things to be aware of that go a long way to protecting yourself from these sorts of scams.
Here are some easy steps to take that still work if you want to give yourself the best chance of avoiding these scam attempts:
- If you don't recognize a URL, don't click on it.
- Don't click links from unrecognized email addresses/accounts.
- Plug dodgy URLs into a URL-checking website like CheckShortURL.
- Contact the legit organization or entity the URL claims to be from.
- Never click a link with a typo or a misspelled word.
- Make sure your computer/browser software is up to date.
- Make sure you have up-to-date antivirus software installed.
- Vary your passwords and login details.
These are all measures to be taken simultaneously – you should never rely on just one precautionary practice. Googling the brand with the phrase/s 'scam' or 'fake URL' or 'typosquatting' after it is a good example of this – finding nothing doesn't mean the URL in question isn't a scam and shouldn't be taken as so, but it might give you an answer straight away.
What do I do if I click on a link to a fake website?
If you've accidentally clicked a scam link, there are two golden rules. First, don't enter any details into the website and close it as quickly as possible. Secondly, disconnect from the internet. These may stop the phisherman in their tracks.
However, if you think it's too late for that and someone or something now has access to your computer, turn off your WiFi connection, anyway. This will stop any malware from traveling further through your network.
Next, perform an anti-virus scan of your computer and change all your passwords, and make sure you back up all the sensitive information currently housed on your device. Then, contact organizations like your bank in case any suspicious activity takes place.
What if the site has a green padlock?
It used to be possible for us to instruct users to avoid all sites that don't use the secure scheme (https://), also known as an SSL certificate, as a first principle of protection.
However, APWG (Anti-Phishing Working Group) says that 77.6% of the phishing sites they detected in the second quarter of 2020 used SSL as their URL, a number that rose to 80% in the third quarter. This is no longer a good criterion for determining the authenticity of any given website.
In simple terms, this means that seeing https:// or a green padlock in a URL is only an indicator that your connection to a website is secure, it is not a guarantee that the site itself is safe!
Not surprisingly, most SSL certificates used by phishers were Domain-Validated ("DV"), which is the weakest form of certificate validation.
According to the report, approximately 40% of phishing sites have SSL validation from a certificate authority that offered free certificates: Let's Encrypt. In simple terms, this means that the vast majority of phishing websites have green padlocks and HTTPS URLs, so you cannot determine whether a website is safe just by looking for the padlock. To determine the validity of a website, do some digging online, look at reviews on search engines, look for scam warnings, and if the site is asking for personal information, ask yourself why it needs it.
Scams to look out for in 2025
Although many of the same scammers, scams, and techniques duping users in 2020 will likely be carried over into this year, there are some new ones to look out for. Some are simply reiterations of old scams, whereas others, like sim-swapping, are relatively new phenomena. Here's a couple to keep an eye out for:
| Vaccine Scams – In a similar vein to the fake furlough phishing texts that emerged in the spring of last year, there have been reports of both emails and texts invoking this topic as scammer look to improve their click-through rates |
| Impersonation scams – Victims are phoned, and the scammer relies on social engineering techniques to convince them of their legitimacy. Instances of such calls rose 84% between January and June of 2020 compared to the previous year. |
| Sim-swap scams – Banks, as well as many other organizations and websites, use phone numbers as part of their authentication processes. Scammers will move your phone number to a new Sim and thus get your authentication texts. Instances of this type of activity have risen 400% in the last five years. |
| University-themed scams – There were reports towards the end of last year of students receiving digital correspondence purporting to be from their university, but in fact, it's a phishing scam stealing their Microsoft365 details. |
What does the future hold?
Scamming and phishing strategies are becoming more and more sophisticated as each year passes. In 2025, although some will persist, it's likely we may see some new scams never seen before. This makes staying vigilant and knowing how to spot a fake URL of paramount importance.
Unfortunately, tightening security measures and developing better defense systems are the only ways to combat fraudulent activity, but this often seems to just raise the bar for hackers, who are more than happy to meet it. Stringent security measures also push hackers to exploit the only non-technological vulnerability in the equation: the victims themselves. Polishing up the 'social engineering' aspects of their scams will likely be top of their priorities.
Cybersecurity provider Kaspersky predicts, for example, that hackers will continue to exploit the covid-19 pandemic for personal gain – this has been a particularly fruitful endeavor for phishermen and will likely continue as countries around the world still struggle to contain outbreaks. As aforementioned, Vaccine-themed scams are already circulating.
They also suggest that thanks to the trend towards improving organizational security, hackers will be more inclined to attempt to exploit vulnerabilities like network appliances and VPN gateways. This involves scammers recreating company VPN login pages and extracting victims' details to access a whole network. 'Vishing' is the term emerging for this practice.
Conclusion
After reading this guide, you'll hopefully be a bit more clued up on fake URLs and exactly what to look for when you're deciding whether to click on a link you've been sent or seen.
But knowing how to spot websites isn't the only way to keep yourself safe and secure online – there are plenty of other handy tools too.
One of them is a VPN. VPNs reroute all your traffic through private servers, masking your IP address and enhancing your online privacy. They have a multitude of other benefits too, and there are lots of options – so check out our in-depth provider analysis to see what the best VPNs for 2025 are.
