A new “feature” in Windows 10 means that DNS requests are directed not just through your VPN tunnel, but also through your ISP and local network interface. This is because by default Windows 10 attempts to improve web performance by sending DNS requests in parallel to all available resources at once, and (at least in theory) using the fastest one.
This is a major issue for VPN users. It means that your ISP (and anyone listening in on your local network) will know through your DNS requests which websites and services you have visited on the internet. It also opens the way for hackers to hijack your DNS requests (DNS spoofing.) In addition to this, there are reports of Windows 10 users suffering slow page loading and timeouts due to this issue.
The problem has led the United States Computer Readiness Team (US-CERT), an official department of the US Department of Homeland Security, to issue an alert.
Smart Multi-Homed Name Resolution
DNS refers to the Dynamic Name System used to translate domain names (proprivacy.com) into numerical IP addresses (216.172.189.144). This translation service is usually performed by your ISP, using its DNS servers. But when you use a VPN service, the DNS request should instead be routed through the VPN tunnel to your VPN provider’s DNS servers, rather than those of your ISP.
Under Windows 7, all DNS requests were made in a simple order of DNS server preference. But this changed in Windows 8 when Microsoft added “‘Smart Multi-Homed Name Resolution” by default. This sent out DNS requests to all available interfaces, but only used non-preferred servers if the main DNS server failed to respond.
This makes Windows 8.x systems liable to DNS leaks, but at least makes it unlikely that DNS requests will be hijacked. Windows 10, on the other hand, simply chooses whichever DNS request responds quickest, which presents a major security risk.
VPN clients that feature “DNS leak protection” should disable Smart Multi-Homed Name Resolution in earlier versions of Windows, but this may not work in Windows 10 (and may vary by individual client). Users of clients without this feature (including the generic open-source OpenVPN client,) will almost certainly be liable to DNS leaks under Windows 10.
Fixes for Smart Multi-Homed Name Resolution DNS leak
- There is now an OpenVPN plugin by ValdikSS that fixes this problem. It should work with all versions of Windows, and should also work with most custom OpenVPN clients that use a standard .ovpn configuration file (i.e. most of them). This is the recommended solution.
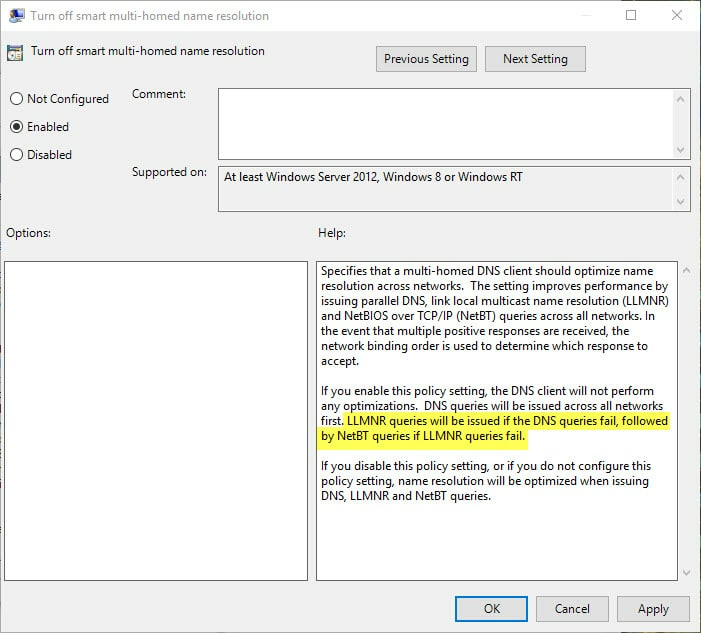
- In theory, it is possible for users of some* versions of Windows 8, Windows 8.1, (and especially!) Windows 10 to disable Smart Multi-Homed Name Resolution using the Local Group Policy Editor. Avast has published some instructionson how to do this.
![Disable Smart Multi-Homed Name Resolution DNS leak fix Disable Smart Multi-Homed Name Resolution DNS leak fix]()
*The ‘Turn off smart multi-homed name resolution’ option is not available to users of Windows Home Editions.
As reader Arthur T. has noted, however, if you look carefully at Microsoft's description of the “Turn off smart multi-homed name resolution” setting in the Group Policy Editor, Windows will still fall back to using Smart Multi-Homed Name Resolution when other DNS queries fail, even when the setting is enabled.
This means that this "solution" is a partial one at best.
Luckily, the OpenVPN plugin mentioned above should fix the problem (for most people) anyway. Whew!

