Malware has been discovered that can hack computers remotely from a router. The malware was discovered by researchers at Kaspersky Lab, it is called Slingshot ATP. The Slingshot malware is the first of its kind that has ever been discovered. The cunning design allows it to gain access to the sysadmin's machine without actually installing itself there in the first place.
The stealth malware is believed to have been in circulation for 6 years, infecting at least 100 computers in that time. The malware, which gets its name from text recovered from its code, is one of the most advanced forms of malware ever discovered. According to Kaspersky’s researchers, it is so advanced that it was likely a state-sponsored development.
Extremely Sophisticated
Describing the malware in its 25-page report (pdf), Kaspersky explains that it is likely a sophisticated tool being exploited by a nation’s intelligence agency for espionage:
"The discovery of Slingshot reveals another complex ecosystem where multiple components work together in order to provide a very flexible and well-oiled cyber-espionage platform.
"The malware is highly advanced, solving all sorts of problems from a technical perspective and often in a very elegant way, combining older and newer components in a thoroughly thought-through, long-term operation, something to expect from a top-notch well-resourced actor."
Costin Raiu, Kaspersky’s director of global research, has gone on the record to praise the ingenuity contained in the Slingshot payload. In a statement, he commented that he had "never seen this attack vector before, first hack the router and then go for sysadmin."
According to Raiu, despite being common, attempts to hack sysadmins are tricky to uncover. He says sysadmin payloads are an extremely sought after attack vector because it gives hackers "the keys to the kingdom." According to the researcher, Slingshot achieves this using a "completely new strategy."

Still a Mystery
The Slingshot router malware was discovered by accident. Kaspersky researchers are still unsure about how it gets delivered on to victims’ routers. What is known, is that whoever controls Slingshot has primarily targeted the payload at routers manufactured by the Latvian firm MikroTik.
Although the exact attack vector remains shrouded in mystery, researchers were able to ascertain that the attackers use a MikroTik config utility called Winbox to "download dynamic link library files from the router's file system." One particular file, ipv4.dll, is loaded onto the sysadmin machine’s memory from the router before being executed. In its report, Kaspersky described the loader as "technically interesting."
The loader ingeniously communicates back to the router to download the more dangerous components of the payload (the router basically acts as the hacker’s Command and Control (CnC) server).
"Following infection, Slingshot would load a number of modules onto the victim device, including two huge and powerful ones: Cahnadr, the kernel-mode module, and GollumApp, a user-mode module. The two modules are connected and able to support each other in information gathering, persistence, and data exfiltration."
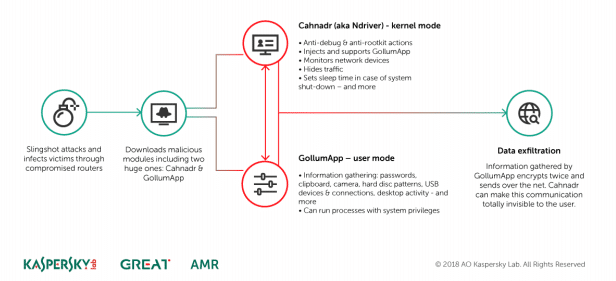
Advanced Stealth Mechanisms
Perhaps the most impressive thing about Slingshot is its ability to avoid detection. Despite being in the wild since 2012 - and still being in operation during the last month - Slingshot has, until now, avoided detection. This is because it uses an encrypted virtual file system purposefully hidden in an unused part of the victim's hard drive.
According to Kaspersky, segregating the malware files from the file system helps it to remain undetected by antivirus programs. The malware also used encryption - and shrewdly designed shut down tactics - to stop forensic tools from detecting its presence.
State Sponsored Snooping
Slingshot appears to have been employed by a nation-state to perform espionage. The malware has been linked to victims in at least 11 countries. So far, Kaspersky has discovered infected computers in Kenya, Yemen, Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia, and Tanzania.
The majority of those targets appear to have been individuals. However, Kaspersky did uncover evidence of some government organizations and institutions being targeted. For now, nobody is sure who controls the sophisticated payload. For the time being, Kaspersky has been unwilling to point fingers. However, the researchers did discover debug messages within the code that were written in perfect English.
Kaspersky has said it believes that the sophistication of Slingshot points to a state-sponsored actor. The fact that it contains perfect English may implicate the NSA, CIA, or GCHQ. Of course, it is possible for state-sponsored malware developers to frame one another by making their exploits appear to have been created elsewhere:
"Some of the techniques used by Slingshot, such as the exploitation of legitimate, yet vulnerable drivers has been seen before in other malware, such as White and Grey Lambert. However, accurate attribution is always hard, if not impossible to determine, and increasingly prone to manipulation and error."
What can users of Mikrotik routers do?
Mikrotik has been informed about the vulnerability by Kaspersky. Users of Mikrotik routers must update to the newest software version as soon as possible to ensure protection against Slingshot.
Title image credit: Yuttanas/Shutterstock.com
Image credits: Hollygraphic/Shutterstock.com, screenshot from Kaspersky report.
