NordVPN, one of the most prominent and respected consumer VPN providers, has confirmed that one of its servers was accessed without authorisation.
The story broke after NordVPN posted a rather impulsive and foolhardy statement on Twitter.
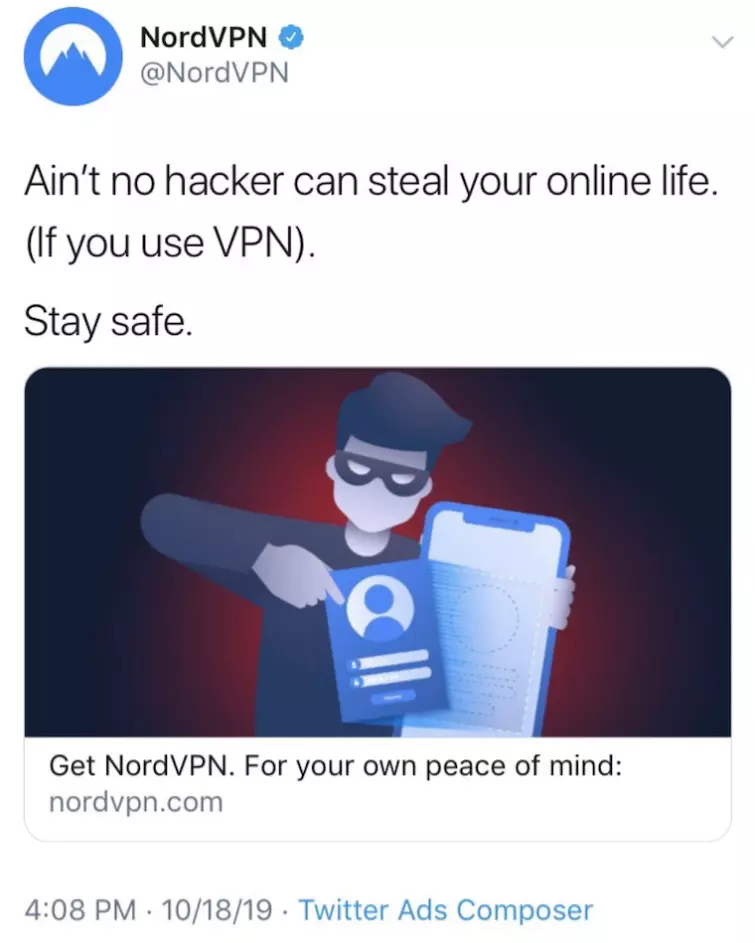
Rather than a statement of fact, the twitterverse saw this as a challenge and it wasn’t long before a group calling itself KekSec revealed that hackers had accessed a server and leaked Nord’s OpenVPN configuration and associated private key as well as TLS certificates.
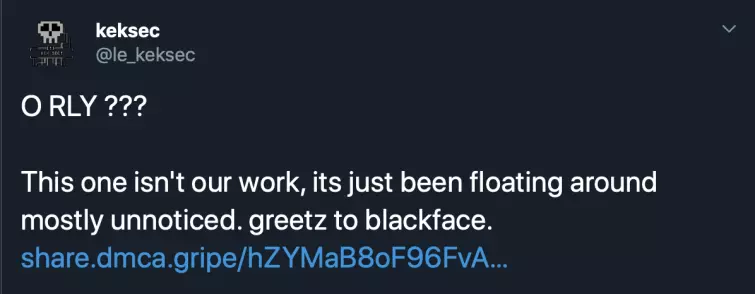
NordVPN has now acknowledged the breach, stating that an attacker gained access to a rented server in Finland by exploiting an insecure remote management system left by the datacenter provider.
Background
In March 2018, TLS certificates belonging to NordVPN, VikingVPN, and TorGuard web servers were posted on 8chan. These certificates have now expired but were current at the time of posting. Despite NordVPN’s efforts to downplay the breach, the publication proves without a doubt that NordVPN has been compromised at some point in the past.
Whoever obtained these certificates must have had root access to the affected servers’ web container and would therefore have had full control over the servers, including the ability to sniff and tamper with data passing through them.
In theory, this also means that anyone could have setup a dummy website purporting to belong NordVPN, VikingVPN, or TorGuard, which your browser would have accepted as being genuine. Indeed, someone has even posted an example of such an attack in action:
NordVPN, however, told us that such a MitM attack would not be possible unless an attacker was able to hack into a user’s person's computer or to intercept and modify their network traffic.
The bigger issue
It has also become apparent that the private SSL keys for NordVPN’s OpenVPN certificates "have also just been floating around mostly unnoticed” for some time now. Yikes! This has fueled speculation that an attacker could decrypt users’ VPN sessions, including past VPN sessions, allowing them to see what NordVPN customers got up to online.
Again, NordVPN was keen to pour cold water on this idea. "Neither TLS Certificate or VPN Keys can be used to decrypt regular VPN traffic or previously recorded VPN session,” they told ProPrivacy.
It’s worth remembering, NordVPN’s OpenVPN sessions use perfect forward secrecy (ephemeral encryption keys) via DHE-2096 Diffie-Hellman keys during the TLS key exchange. So even if a VPN session was brute forced at huge cost in money, effort and computing power, only one hour of the VPN session would be compromised before the key was changed.
Although this point may be moot since the attacker clearly had root access to the VPN server.
The blame game
NordVPN has published an official statement on the incident, in which it explains that only a single server located in Finland was affected. It also says that fault lies with the server center staff:
"The attacker gained access to the server by exploiting an insecure remote management system left by the datacenter provider. We were unaware that such a system existed.”
We have to say, though, that we feel a company as large as NordVPN should be sending out its own technicians to setup its own bare-metal VPN servers, rather than relying on potentially untrustworthy third-party server staff to setup their VPN servers.
In our view, a VPN service should have complete control over its servers. Doing this would go a long way towards hardening a VPN server network against all threats. Interestingly, this is also a view held by Niko Viskari, CEO of the server center in question:
"Yes, we can confirm [Nord] were our clients," Viskari told The Register. "And they had a problem with their security because they did not take care of it themselves.
...they had a problem with their security because they did not take care of it themselves
"We have many clients, and some large VPN service providers among them, who take care of their security very strongly,” he said, adding: "NordVPN seems it did not pay more attention to security by themselves, and somehow try to put this on our shoulders."
In his statement, Viskari goes on the explain that all servers provided by his company use the iLO or iDRAC remote access tools. These have known security issues from time to time, but the server center keeps them patched with the latest firmware updates from HP and Dell.
Unlike other its other customers, NordVPN did not ask for these tools to be restricted by placing them "inside private nets or shutting down ports until they are needed.”
NordVPN, for its part, claims it didn’t even know these tools existed; but if it had setup its own servers the problem would have never arisen.
"We did not disclose the exploit immediately because we had to make sure that none of our infrastructure could be prone to similar issues.”
Which does not explain why the issue took some 18 months to come to light, with NordVPN only finally admitting to it in the wake of a Twitterstorm which saw damning evidence widely published on the internet.
At the end of the day, though, more damage has been done to NordVPN’s reputation than to its users’ privacy.
"Even though only 1 of more than 3000 servers we had at the time was affected, we are not trying to undermine the severity of the issue" the provider said in its statement.
"We failed by contracting an unreliable server provider and should have done better to ensure the security of our customers. We are taking all the necessary means to enhance our security. We have undergone an application security audit, are working on a second no-logs audit right now, and are preparing a bug bounty program. We will give our all to maximize the security of every aspect of our service, and next year we will launch an independent external audit all of our infrastructure to make sure we did not miss anything else."
ProPrivacy statement
ProPrivacy is dedicated to providing its users with advice they can trust. We regularly include NordVPN in our recommendations because of the fantastic service they offer. In light of this breaking story, we will be removing NordVPN from our security and privacy related articles until such time as we are confident that their service meets our expectations and those of our readers.
