When I consider the real-life chances that an individual will get hacked in a given year, I find it impossible not to think of something I've heard so many computer users say to me in the past: "It won't happen to me."
Well, actually, it really might, and my intention with this article is to demonstrate why.
Before I look at the actual chances that you'll get hacked in a typical year, I should really pose the question of whether it's happened to you already? If you include being hacked on Facebook in some way, or having a Web-based email account compromised, the chances are that if it's not happened to you by now, you at least know plenty of people who have experienced it.
So what ARE the chances you'll get hacked?
There's no definitive answer to this question, and recent statistics are rather thin on the ground. However, there are plenty of studies out there that suggest different probabilities, all of which are quite worrying. By amalgamating them together we can make an informed statement on how likely you are to get hacked.
For example:
- A couple of years ago the National Cyber Security Alliance estimated the chances of a small business being hacked at 20% each year, according to this report.
- A Ponemon Institute study referenced here delivered an even more worrying verdict - that nearly half of the US population were hacked in some way in the space of one year. Given these figures were calculated using the entire adult population, it seems reasonable to surmise hacks affected more than half of active US Internet users.
- A study by the National Small Business Association produced a figure of 43% of SMEs being hacked in a given year.
- More figures from the UK show that there were 2.5 Million recorded cyber-crimes in Britain in 2014. Despite this accounting for ten of the population, KPMG commented on the release of the study that due to so many incidents being unreported, the true figure was probably far higher.
So let's average these out: The first study seems to suggest a 20% chance of getting hacked in a year; the second, we'll generously put at 50%; the third at 43%; and the forth (again generously) at 10%.
This suggests that compiling a range of studies places the annual percentage of getting hacked (in some way) at just below 31% - around a 1 in 3 chance. Yes, one could be pedantic about the sample sizes, but these studies are often rather subjective anyway. We still arrive at around a 1 in 3 chance of being hacked, even after being cautious with the numbers.

Proof, as if it were needed, that it can happen to anyone, came along right on time while I was researching this article. Despite being a long-term techie who charges for consultancy and possesses qualifications from both Apple and Microsoft, I have to shamefully admit I nearly fell for a "phishing" attempt just this week.
I listed a couple of items on Gumtree and after a few days received both (SMS) message and email, indicating someone wanted to buy one of them. It was the use of a simultaneous text message that caught me off guard and caused me to drop my usual careful approach. Thankfully, when I clicked through from the email, the antivirus software on my Mac stopped me in my tracks, but I have to admit I'd been had. The two lessons here are:
- Some hacking / phishing attempts are so sophisticated and/or convincing that they can catch you out even if you're "on your guard."
- Antivirus software on an Apple Mac does have some value, even if plenty of people consider it unnecessary!
HOW could I get hacked?
You may be wondering how exactly you could get hacked? The first thing to know is that the days where all you had to worry about were pesky Windows viruses are long gone.
If you've watched the fantastic Mr Robot on Amazon Prime, you may recall the protagonist referring to "hacking people." A lot of hacking nowadays starts with a little social engineering and before the actual techie stuff starts.
So, with that in mind, I'll begin my round-up of some of the key flavours of hacking with the activity I almost fell victim to recently: Phishing.
Phishing
Phishing is all about trickery. A typical approach is for a cyber-criminal to create a replica of a legitimate website's login and then use convincing looking emails to lure unsuspecting Internet users to it. People then enter their login details and - hey presto - they've handed them to the hackers.
Unsurprisingly, a lot of phishing attempts focus on sites where money is involved. PayPal is a common target, as are Internet banking websites. While the emails often look convincing at first sight, it's generally quite easy to expose them as fake. For example, they will usually come from a domain that's similar to the genuine article, but not quite right.
The image below shows one of these phishing emails, purportedly coming from Apple.
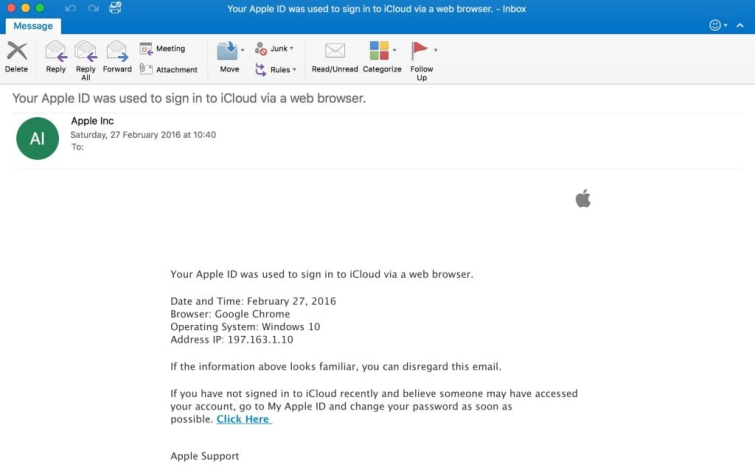
On the surface, this looks reasonably legit. There's an Apple logo, and it says it comes from Apple Inc. With millions of people using iCloud, there's a fair chance an unsuspicious user could think it applies to them.
Furthermore, it delivers the worrying news that someone has signed into your iCloud from somewhere, and encourages you to click the link to visit the Apple site to change your password. When you click the link, you're taken to a legit looking "Apple" site that requests your login details. If you provide them, you provide them to the hackers - not to Apple.
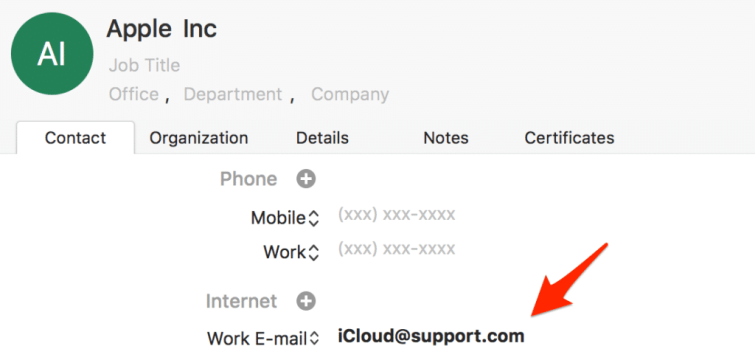
A little investigation easily reveals that this email is a phishing email. If I look at the properties of the email address (see image below), it's not even at Apple! Instead, it's from a very suspect looking "support.com" address.
Many of these phishing attempts are very clumsy, to the point they're sometimes riddled with spelling mistakes. The fake sites are often shut down very quickly. But it's all a numbers games for the hackers. They send out thousands or millions of these emails, and only need a small proportion of people to bite to earn themselves lots of personal info to play around with.
It gets worse too. The next stage of phishing is what's known as "spear phishing." Often targeting small businesses, the hackers will aim to get just enough information to find a way into a corporate system - sometimes by being audacious enough to call a staff member pretending to be the IT department! Once they have a route into the IT system they get as far as they can, often targeting the payroll system, rerouting all the wage payments to their own account.
Does this all sound a little far-fetched? Well, how's this? A study last year found that 23% of people open phishing emails, with 10% even opening suspicious attachments. When hackers launch a new phishing campaign it usually takes just 82 seconds before the first victim succumbs.
Ransomware
Ransomware is a huge growth area at the and another way you could get hacked in 2016.
Five years ago, a common form of ransomware was fake antivirus programs. They would arrive as email or install themselves along with legitimate looking downloads from the web. They would then tell the user their computer was infected, requesting a fee to upgrade to the full version of the "software" in order to urgently remove the thousands of "viruses."
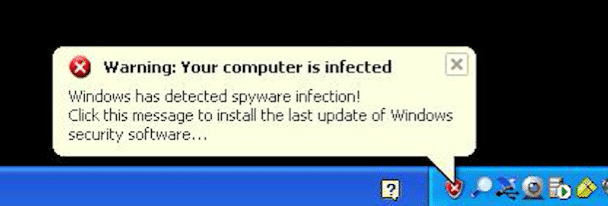
Needless to say, plenty of unsuspecting non-techies were caught out and handed over the cash. Furthermore, even for someone with technical skill, removing the fake programs often took hours of detailed work, frequently making it more time and cost-effective to wipe the PC and start again.
Nowadays, ransomware producers have become brazen in their activities, using sophisticated malware to encrypt people's data and insisting (quite literally) on a financial "ransom" to unlock it. In many cases, people and organizations have needed the data back so badly they've had no option but to cough up.
Want another scary statistic? The FBI that since April 2014, victims of CryptoWall, just one piece of ransomware that works as described above, have paid out in excess of $18 Million to unlock their data. Whoever said crime doesn't pay?
Viruses and Trojans
Although a traditional antivirus product is still commonly seen as the first line of in computer security, "old school" viruses and trojans seem (subjectively) to be falling out of somewhat with cyber-criminals. Antivirus software, email software and even operating systems themselves have toughened up against these "traditional" threats in recent years, leading many criminals to move into the more lucrative phishing and ransomware activities described above.

Does this mean that these viruses are something you needn't worry about? Sadly, you really DO still need to worry about them. New viruses are still discovered every day and can do all sorts of scary things like your keystrokes to steal your personal information. Often, a virus is part of a larger criminal strategy that ties in with phishing and ransomware. You should still use antivirus software at all times, be very suspicious of unsolicited email attachments, and be very cautious of any executable files you download from the Internet.
How big's the problem? Well, Kaspersky alone (one of the world's leading antivirus vendors) found over 121 Million "malicious objects" like this on the Web last year.
"Nuisance" Hacks
I'll end my (far from exhaustive) round-up of ways you could get hacked in 2016 with what I'd describe as "nuisance hacks."
You'll no doubt have seen these before when you suddenly start to receive strange emails from a friend's old Hotmail account, or when someone tells you you've been posting unusual Facebook updates.
While these hacks don't always seem as serious, they have a distinctly dark side to them. Often, they're linked to phishing or other kinds of threats, with the emails or updates coming complete with a link to a malicious site. If someone tells you they're getting strange emails from your account, then you have quite possibly been hacked, and it's time to change your passwords, as your account could be used to further a cybercriminal's objectives.
What to do if you DON'T want to get hacked?
While my frightening one in three may cause you to think that it's an inevitability that you'll get hacked eventually, there is plenty you can do to protect yourself and increase your chances of remaining in the "lucky" 69%
Here are a few pointers for starters:
- Be deeply suspicious while you're online! If you get an email from a company telling you to change your password, don't click the link, go directly to what you know is their legitimate website.
- NEVER download attachments from sources you're unfamiliar with, even if you've been convinced you've won $1000!
- Use a VPN service for all your online activity, to increase your security and privacy, and make it harder for people to learn about you and what you do online - it could be used against you by a criminal or provide some extra clues for a phishing attack. You'll find a list of recommended VPNs for Windows here and for Mac here.
- Use antivirus software and keep it up to date - and yes that does apply to Mac users!
- Never reveal anything to do with your online life to anyone who calls you on the phone. Microsoft will never phone you because they've discovered a problem on your computer.
If you want to find out more about IT security and privacy check out our Ultimate Privacy Guide or our extensive VPN for Beginners . Be careful out there, and try not to get hacked!
IMAGE CREDITS: Flickr, Wikipedia
