The malicious Telegram Installer was found to drop the Purple Fox malware, executed in multiple stages and, therefore, very difficult to detect.
According to the Minerva Labs research team, the trojanized Telegram installer differs from the usual cyber threats, mainly in its ability to break up its payload into multiple parts to evade anti-virus scanners. Also, it disperses to further spread malicious payloads on infected devices – once again staying under the radar.
The current chain of attack
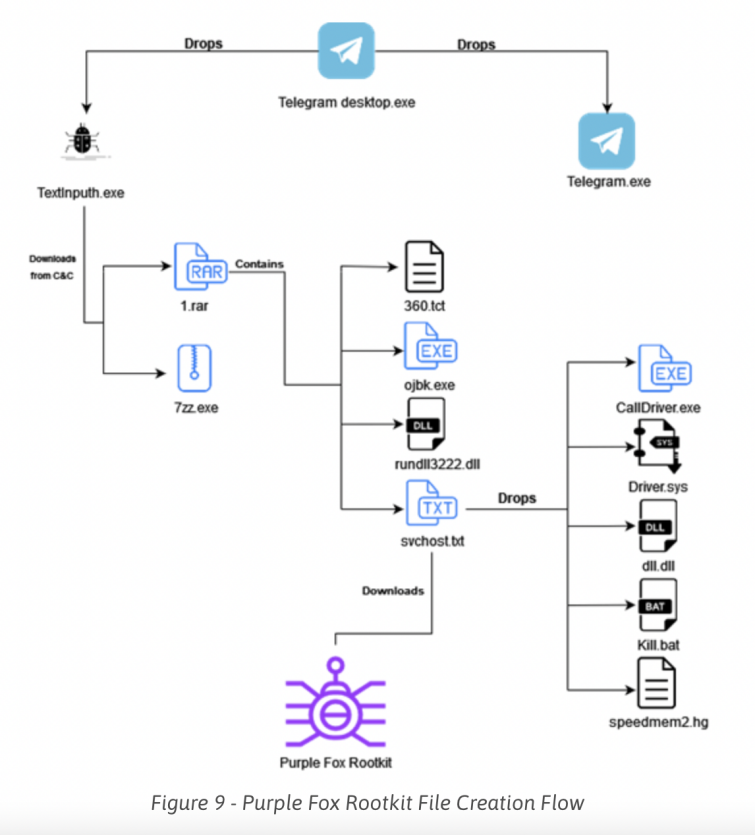
The most recent chain of attack starts with an AutoIt (a freeware scripting language made for automating Windows GUI and general scripting) script file called Telegram Desktop.exe, in most cases delivered via email or from fishing websites. The AutoIt script then creates a new folder called TextInputh under C:\Users\Username\AppData\Local\Temp\ and downloads a genuine Telegram installer (not executed) and a malicious downloader – TextInputh.exe.
TextInputh.exe is then executed and retrieves the next-stage malware from a command-and-control (C2) server. From there, the attack flow continues as the files create blockers for different antivirus engines, before reaching the final stage, resulting in the download and execution of the Purple Fox rootkit. In the meantime, the remote server responsible for the execution of Purple Fox gets shut down.
As soon as Purple Fox is executed, the infected device will restart and allow the newly installed settings to take over, disabling the User Account Control (UAC) and giving the malware administrator privileges. Afterwards, Purple Fox is free to perform malicious operations like file search and exfiltration, deletion of data, downloading and running code, process killing, and similar.
The beauty of this attack is that every stage is separated to a different file which are useless without the entire file set.
According to Minerva Labs researcher, Zargarov, a large number of malicious installers are seen delivering the identical Purple Fox rootkit using the same infection flow. What makes this rootkit even more challenging to detect is that every stage is separated into different files, which are all completely useless individually, without the whole file set.
More about Purple Fox
Purple Fox was first discovered and described in 2018 as an active trojan malware campaign attacking Windows devices. That year, the malware infected over 30,000 Windows machines and was beyond the reach of contemporary detection mechanisms and security solutions. Initially, Purple Fox’s operations spread through exploit kits and phishing emails but, soon after, they evolved to breaches via brute forcing insecure SMB passwords.
In March 2021, Purple Fox already showed advanced worm-like propagation characteristics, allowing much faster advancement of the malware. In October same year, Trend Micro detected new suspicious activities concerning Purple Fox – a new backdoor written as a .NET implant that utilizes WebSockets to help establish more secure means of communications. The new rootkit capabilities of Purple Fox allowed it "to persist on affected systems as well as deliver further payloads to affected systems" as stated by Trend Micro researchers.
The latest upgrade occurred in December 2021, when Purple Fox started targeting SQL databases by inserting a malicious SQL common language runtime (CLR) module to execute even sneakier and more relentless attacks and ultimately illicit cryptocurrency mining through the abuse of SQL servers.
Reminder to our readers
Purple Fox rootkit is an intrusive malware that is extraordinarily hard to detect, and, as such, is a hot topic within the cyber security world. But its full scope, unfortunately, is yet to be seen. One thing is for sure, however; it’s an extremely dangerous malware with carefully developed mechanisms to create major damage to your privacy.
That’s why we would like to remind our readers not to open suspicious emails or files and especially not to download software from unknown sources. Keep your security protection active at all times, and if your antivirus suggests anything like "discover Trojan risk”, clean up your PC right away.
