Advantages
There are a number of KeePass ports for Android. Most of these are open source and can open and manipulate regular KeePass files. I use K2A because:
- It has much better Android integration than other Keepass ports. Or, indeed, than most commercials products we have reviewed.
- It does not rely on Android’s insecure clipboard function to work. Both of these advantages are related to K2A's custom keyboard feature (see below).
Disadvantages
The main downside of K2A is that it is only available via the Google Play Store, and is therefore updated via Google Play Services. This means that, in theory, Google could slip malicious code into an update at any time.
We are comfortable with the trade-off between this risk and the advantages listed above. For anyone who is wary of Google, I recommend using either KeePass DX or KeePass Droid instead.
Both of these apps are available from F-Droid and mitigate the clipboard problem with a clipboard timeout. This is not as secure as K2A keyboard solution but does minimize the problem.
The K2A Keyboard
Most Android password managers (including most KeePass ports) work using Android’s built-in clipboard function. This allows you to copy and paste usernames and passwords from an opened KeePass database to the app or webpage where they are needed.
“Many [password] apps completely ignore the problem of clipboard sniffing, meaning that there is no cleanup of the clipboard after credentials have been copied into it. [...] We found that, for example, auto-fill functions for applications could be abused to steal the stored secrets from the password manager application using 'hidden phishing' attacks.”
K2A solves this problem by providing its own keyboard. This can directly access the KeePass database and enter usernames and passwords into forms without the need to store data on Android’s clipboard.
The keyboard is also good for Android integration, as it works with all apps. There is no need for any form of custom integration or browser add-on. It can be installed alongside other keyboards, can be easily swapped in and out with other keyboards.
We find the K2A keyboard a little basic for day-to-day use as an Android keyboard. It features no text prediction, for example, no personalized auto-correct, or fancy swipe-input.
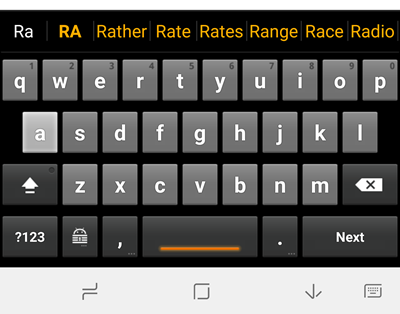
But this is not necessarily a bad thing. These features can be a serious privacy risk. The K2A keyboard, on the other hand, is completely self-contained and sends no information to anyone.
However, we are comfortable sacrificing a little privacy for convenience, and therefore only use the K2A keyboard for entering passwords. Sorry, but I am just lazy! For the seriously privacy-conscious, however, the K2A keyboard would make a great daily driver.
Cloud Syncing KeePass Files
It is easy to securely sync passwords across devices using any cloud service. This includes the likes of Dropbox and Google Drive. Before you object, I am well aware that services such as this are a privacy nightmare. The thing is, though, that it doesn’t matter.
Each .kbdx file is encrypted by yourself using rock-solid encryption. By default, K2A uses an AES-256 cipher with SHA-256 hash authentication. This is very secure, but even stronger options are available.
The only way to access the file is using a master password which should be known only to yourself. So pick a good one! There is also the option to further improve security by requiring that a key file (created by yourself) be present when opening the .kbdx file.
In other words, no-one is going to open a properly secured .kbdx file, no matter how publically it is stored.
The truly paranoid, however, can store a .kbdx file locally on their Android devices and manually synchronize it with .kdbx files stored on other devices using a USB cable or suchlike. If you do not plan on using K2A's online syncing features then you can use install the offline-only Keepass2Android Offline instead.
Passwords are synced online whenever you save changes to the database. This because all your KeePass programs on all your devices can access the .kbdx file.
Using K2A
Setting up and opening a K2A database
Please note that K2A's security policy no longer permits screenshots to be taken of open databases. In order to illustrate how KeePass2Android works, I have therefore used some screenshots from Google Play Store.
Install Keepass2Android Password Safe from the Google Play store. The only required privileges are:
- SD Card access
- Internet access (install K2A Offline if you don't want to grant this privilege)
- Vibrate
When you first open K2A you have the option to either open an existing KeePass database (.kbdx file) or create a new one.

If opening an existing .kbdx file, KeePass2Android supports a wide selection of popular cloud services, plus various self-hosting solutions (including local storage). Simply sign-in to your chosen service/personal solution if necessary, and browse to your stored .kbdx file.
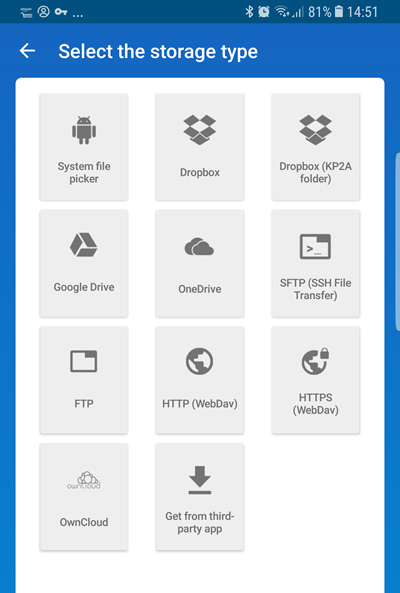
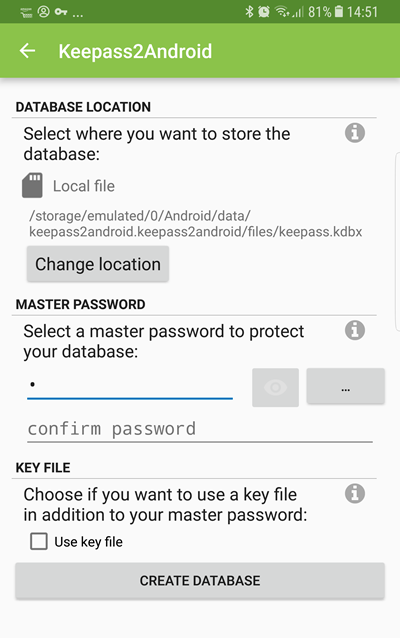
Alternatively, you can create a new KeePass database. By default, this uses an AES-265 cipher, but you can change this to a ChaCha20 or Twofish-256. Key derivation used is AES-KDF with 500000 encryption rounds by default, but can be changed to Argon2 if you prefer.
You can also create a key file to improve security. This file must be present for the database to be opened. This file should not be stored online. You should instead store copies of it locally on any device you want to open the .kbdx file with (or for the really paranoid, carry a single copy of it around with you on a USB stuck or suchlike).
For more information on creating a KeePass database, please see my full KeePass Review.
Once a .kbdx has file has been located or created, you can open it in two or three ways:
- Password unlock – simply enter the full password or passphrase you created when setting up the database.
- Quick unlock (optional) – if a database has already been opened using its full password/passphrase, then it can be quickly reopened using just the last few letters of the password/passphrase (three by default). This is, of course, not as secure as using the full password each time. But it is very convenient.
- Fingerprint unlock (optional). If your device has a fingerprint scanner, then you can use it to unlock a .kbdx file. This replaces the need to enter either the full password or just the Quick unlock password.
In all cases, the key file must be present if the .kbdx database requires one.
The database
Passwords can be organized into groups.
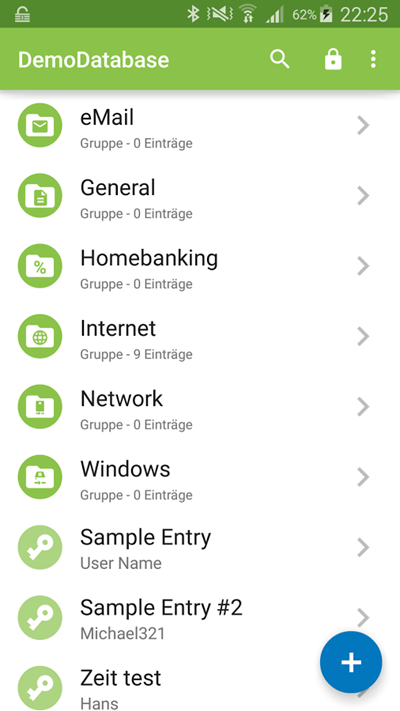
You can create new passwords, inspect, and edit password details.
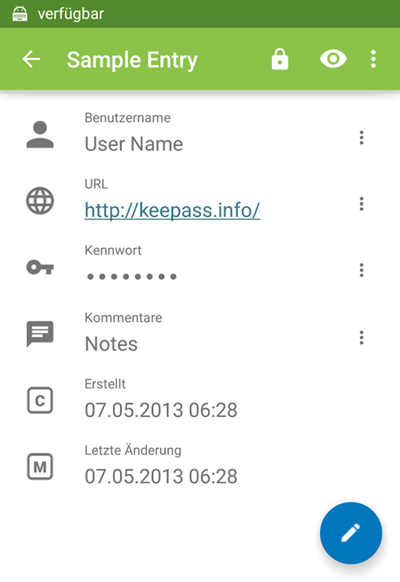
Android Integration
You can cut-and-paste usernames and the passwords from the database, but as discussed earlier, this not very secure. The problem is mitigated by a clipboard timeout (default 5 minutes, but this can be changed), but it is also rather cumbersome.
Where KeePass2Android is miles ahead of its rivals, however, is in its Android integration.
The Android Autofill Service
As of Android 8.0 Oreo, K2A can integrate with the new Android Autofill Service. In theory, this automatically offers to fill in usernames and passwords wherever you encounter them on your device – whether in your browser on in apps.
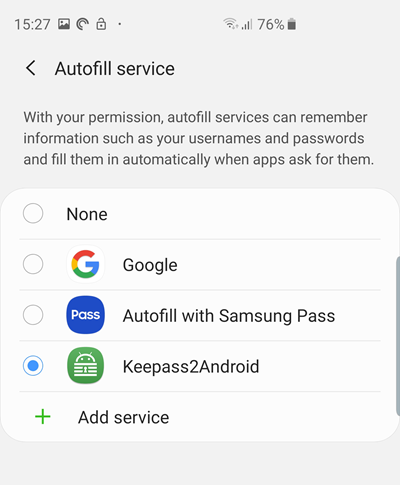
In practice, support remains a little patchy at this time. Google Chrome, for example, which offers its own password a manager, stubbornly refuses to play the game. The feature works flawlessly in many apps, however, and I have found it a godsend when signing into accounts using the Firefox for Android browser.
When it works (which is most of the time and is particularly useful in Firefox) the Android Autofill Service makes using K2A ridiculously easy.
Keyboard Input
For users of older devices and for when apps won't adopt the Android Autofill Service, the main way K2A integrates with Android is via its keyboard. This is installed alongside the main app, and can be hot-swapped with your regular keyboard if desired. It is the most secure way to input credentials and is fairly convenient. It also works with any password field in any app.
On my Samsung phone it is dead easy to switch between keyboards once they have been installed.
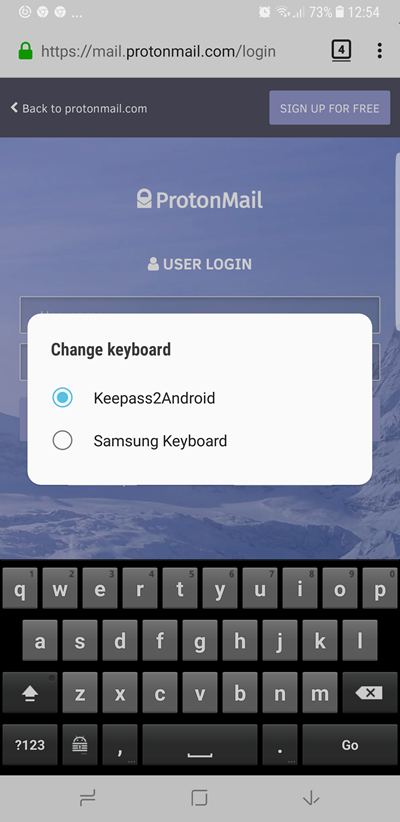
To enter usernames and passwords into any web page or Android app, select the keyboard’s special KeePass icon. This brings up the option to select an entry from your KeePass database or let K2A try to Search for the correct one for you.
I must admit that I find the search function to be a very hit and miss, so usually just opt to select an entry myself. If the .kbdx database is not already open, then you will need to open it using one of the methods outlined above.
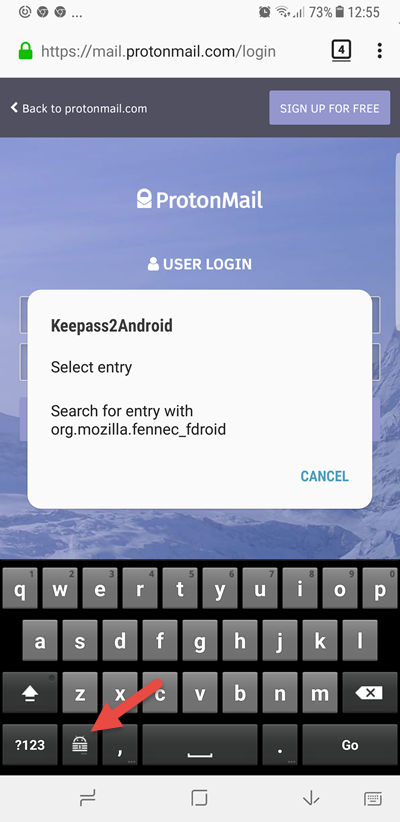
Once the correct entry is found or selected, K2A enters autofill mode. Simply select the correct entry field and choose either User or Password and the keyboard will enter the information. Easy!
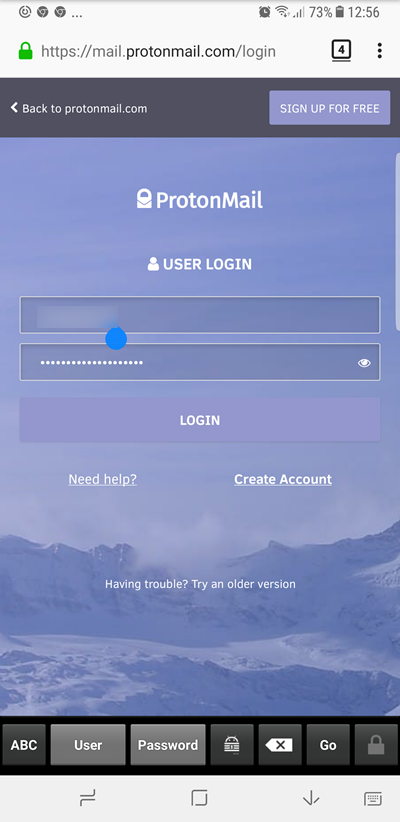
You can switch back to the conventional keyboard by touching the ABC button.
Browser integration
As already noted, K2A is insanely easy to use on newer phones in browsers which support the Android Autofill Service. Even without this, however, it works quite smoothly in any browser.
On a web page with a login, simply use your browser’s Share feature to share with K2A.
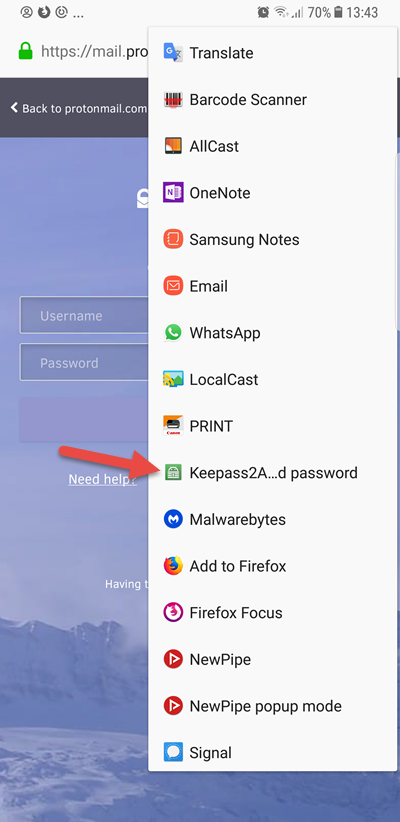
Unlock your KeePass database, and K2A should already have found the correct entry(s). I find searching for entries in this way to be more effective than using the keyboard search function.
You still need to use K2A keyboard in autofill mode to enter the details unless you have the KeyboardSwap for K2A plugin installed and correctly configured.
Conclusion
Thanks to its open-source end-to-end nature, KeePass is the only password manager I really recommend*. KeePass2Android is a great port of it. It is fully compatible with regular KeePass 2.x database files, syncs across devices seamlessly, and integrates far better with Android than any other KeePass port I have tired.
Its reliance on Google Play Services is a drawback, and it would be great to see an F-Droid version of the app. In my view, however, this issue is compensated for by the extra security afforded by the dedicated keyboard input method.
*Since writing this review I also recommend the open-source Bitwarden password manager.
0 User Reviews
Leave a Review
Thanks for your review!
13 Comments
Write Your Own Comment
Your comment has been sent to the queue. It will appear shortly.

Brad
To y
Imprescindibles replied to To y
Sven
Danish